Enumerating Active Directory
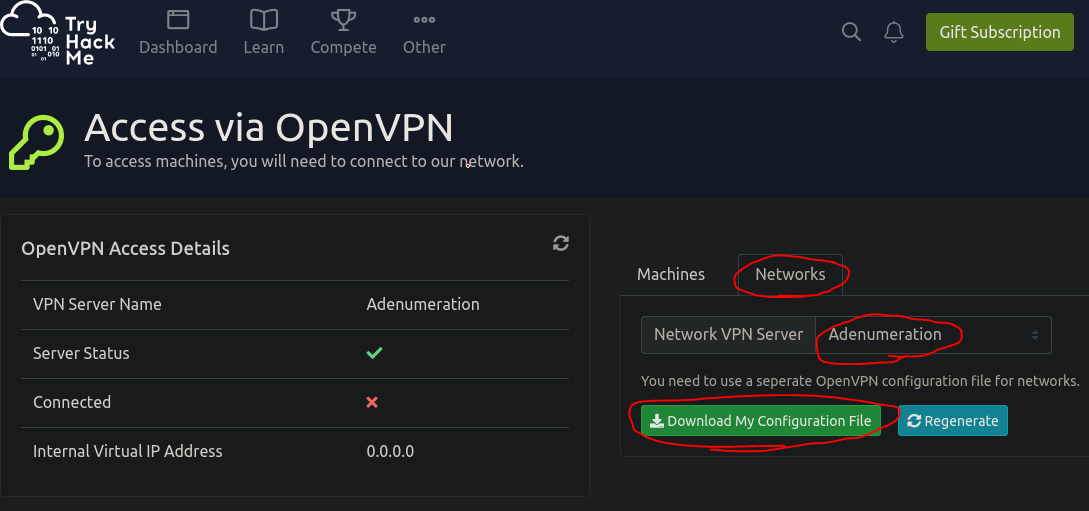
首先先到這個Access頁面下載連線用vpn:
連線之前要先做些設定,到「Advanced Network configuration」把DNS Server設定跟THMDC相同:
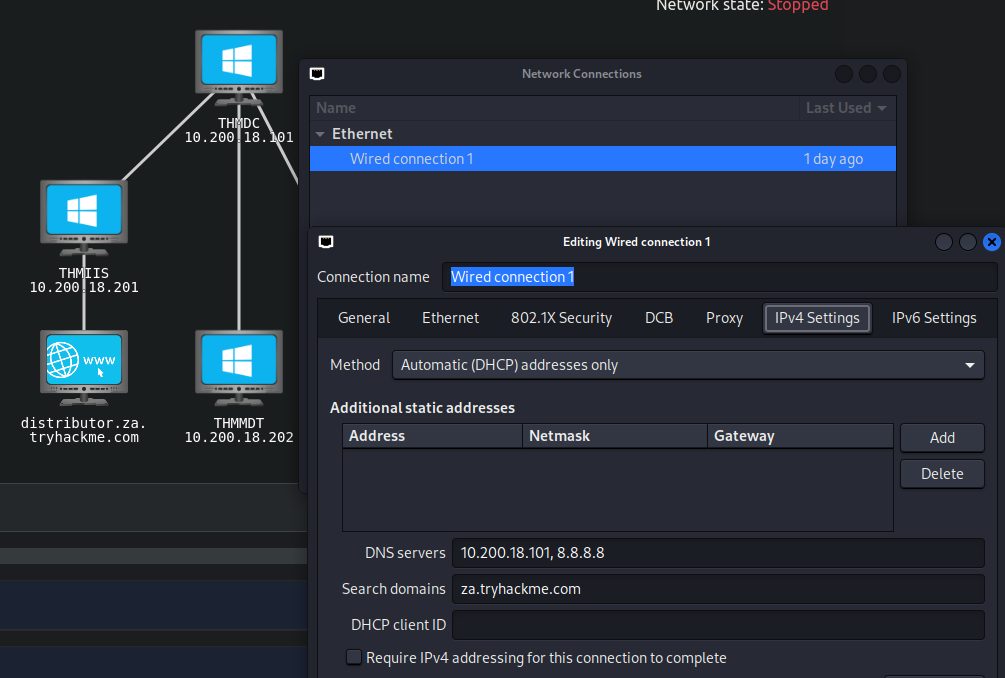
上述圖按確定後,要重新啟動網路:
┌──(kali㉿kali)-[~]
└─$ sudo systemctl restart NetworkManager
┌──(kali㉿kali)-[~]
└─$ nslookup thmdc.za.tryhackme.com
Server: 10.200.18.101
Address: 10.200.18.101#53
Name: thmdc.za.tryhackme.com
Address: 10.200.18.101
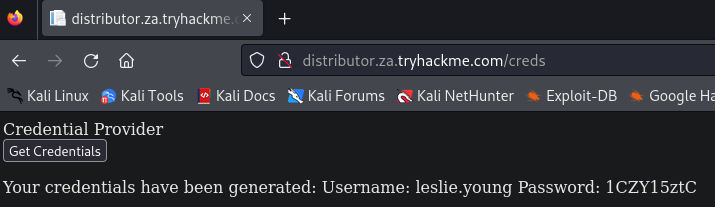
接下來到下列網址取得登入用的帳密:
http://distributor.za.tryhackme.com/creds
task 2 Credential Injection
輸入ssh za.tryhackme.com\\leslie.young@thmjmp1.za.tryhackme.com,並輸入上圖給的密碼。目前的假設是我們入侵內網的行動,已經拿到其中一台內網機器(thmjmp1)的低權限帳密,把它當跳板主機:
Microsoft Windows [Version 10.0.17763.1098]
(c) 2018 Microsoft Corporation. All rights reserved.
za\leslie.young@THMJMP1 C:\Users\leslie.young>
我们可以使用Runas注入凭据,Runas是一个合法的Windows二进制文件,它能够将我们已知的AD凭据注入到内存中。其中netonly的意義是僅對網路工作階段使用已註入的憑證,所有其他指令都會在本機上的目前用戶會話中運行;user提供目標域和用戶名的詳細信息,此處使用完全限定域名(FQDN)而不僅僅是域的NetBIOS名稱是一個更好的選擇,因為這將有助於進行DNS解析;cmd.exe則是代表注入AD憑證後將要執行的程序是cmd.exe,我們可以將其變更為其他任何內容,但此處最好的選擇是指定執行cmd.exe程式。
za\leslie.young@THMJMP1 C:\Users\leslie.young>runas.exe /netonly /user:za.tryhackme.com\leslie.young cmd.exe
Enter the password for za.tryhackme.com\leslie.young:
Attempting to start cmd.exe as user "za.tryhackme.com\leslie.young" ...
za\leslie.young@THMJMP1 C:\Users\leslie.young>
現在,我們需要驗證我們所使用的憑證能否正常運作,我們可以嘗試列出SYSVOL目錄,因為任何AD帳戶(即使是最低權限的AD帳戶)都可以讀取SYSVOL目錄的內容。SYSVOL是一個存在於所有網域控制站上的資料夾,而且是一個共用資料夾,它可用於儲存群組原則物件(GPO)和資訊以及任何其他與網域相關的腳本。SYSVOL是Active Directory的重要組件之一,它能夠將GPO交付給域中的所有計算機,而連接到域的計算機也可以讀取GPO以及應用一些可應用的GPO,並且能夠從域的中央位置針對域範圍內的配置進行變更。在嘗試列出SYSVOL目錄之前,我們還需要設定DNS。有時候,機器內部的DNS會透過DHCP或VPN連線自動配置,但並非總是如此(例如本文的THM實驗網路)。理解如何手動完成此處的DNS配置工作是很好的,我們通常會使用網域控制器作為DNS伺服器,我們只需要指定使用網域控制器的IP作為DNS IP即可
za\leslie.young@THMJMP1 C:\Users\leslie.young>dir \\za.tryhackme.com\SYSVOL
Volume in drive \\za.tryhackme.com\SYSVOL is Windows
Volume Serial Number is 1634-22A9
Directory of \\za.tryhackme.com\SYSVOL
02/24/2022 09:57 PM <DIR> .
02/24/2022 09:57 PM <DIR> ..
02/24/2022 09:57 PM <JUNCTION> za.tryhackme.com [C:\Windows\SYSVOL\domain]
0 File(s) 0 bytes
3 Dir(s) 51,580,354,560 bytes free
task 3 Enumeration through Microsoft Management Console
利用rdp:(*注意rdp指令參數,要再補充)
┌──(kali㉿kali)-[~]
└─$ xfreerdp /d:za.tryhackme.com /u:leslie.young /p:1CZY15ztC /v:thmjmp1.za.tryhackme.com /drive:.,kali-share +clipboard
[05:04:35:757] [131656:131657] [WARN][com.freerdp.crypto] - Certificate verification failure 'self-signed certificate (18)' at stack position 0
[05:04:35:757] [131656:131657] [WARN][com.freerdp.crypto] - CN = THMJMP1.za.tryhackme.com
Certificate details for thmjmp1.za.tryhackme.com:3389 (RDP-Server):
Common Name: THMJMP1.za.tryhackme.com
Subject: CN = THMJMP1.za.tryhackme.com
Issuer: CN = THMJMP1.za.tryhackme.com
Thumbprint: 87:d7:7f:fd:cd:c6:d4:c9:a8:0f:f3:72:ba:a1:35:c3:8d:4b:52:7d:7a:13:5d:9c:a5:53:41:f1:35:09:ba:5e
The above X.509 certificate could not be verified, possibly because you do not have
the CA certificate in your certificate store, or the certificate has expired.
Please look at the OpenSSL documentation on how to add a private CA to the store.
Do you trust the above certificate? (Y/T/N) Y
[05:04:44:310] [131656:131657] [INFO][com.freerdp.gdi] - Local framebuffer format PIXEL_FORMAT_BGRX32
[05:04:44:310] [131656:131657] [INFO][com.freerdp.gdi] - Remote framebuffer format PIXEL_FORMAT_BGRA32
[05:04:44:342] [131656:131657] [INFO][com.freerdp.channels.rdpsnd.client] - [static] Loaded fake backend for rdpsnd
[05:04:44:343] [131656:131747] [INFO][com.freerdp.channels.rdpdr.client] - Loading device service drive [kali-share] (static)
[05:04:44:344] [131656:131657] [INFO][com.freerdp.channels.drdynvc.client] - Loading Dynamic Virtual Channel rdpgfx
[05:04:46:742] [131656:131657] [INFO][com.freerdp.client.x11] - Logon Error Info LOGON_FAILED_OTHER [LOGON_MSG_SESSION_CONTINUE]
[05:04:47:708] [131656:131747] [INFO][com.freerdp.channels.rdpdr.client] - registered device #1: kali-share (type=8 id=1)
下圖是用rdp連進去後看到的畫面,我們用這個使用者的權限啟動mmc(Microsoft Management Console)。
啟動後選下圖的選項:
選擊Active Directory Domains and Trusts後按add:
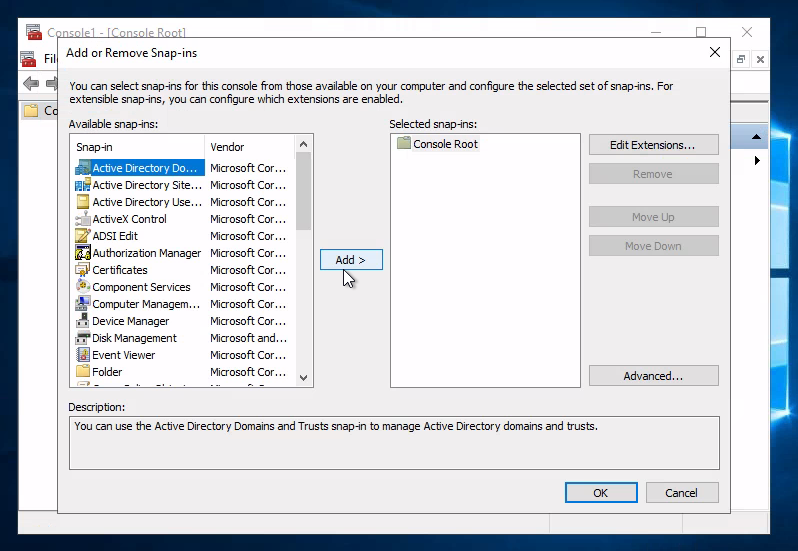
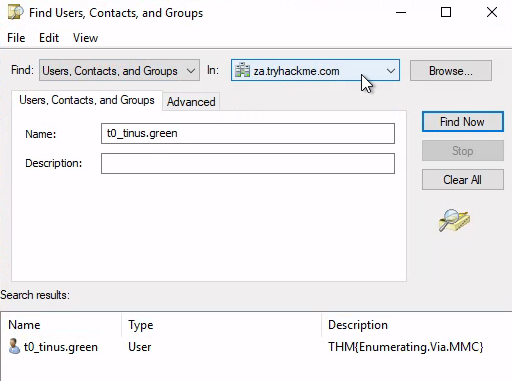
之後就可以看到如下畫面,來回答THM上出的問題:
How many Computer objects are part of the Servers OU? Ans: 2
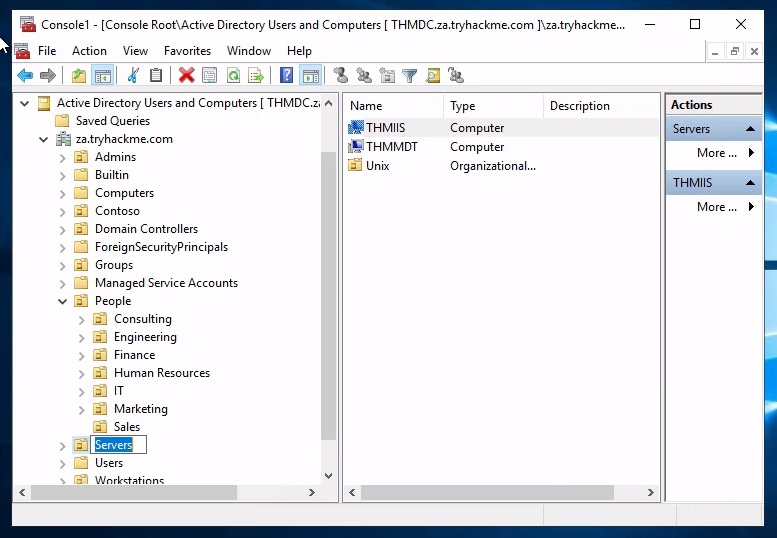
How many Computer objects are part of the Workstations OU? 1
How many departments (Organisational Units) does this organisation consist of?
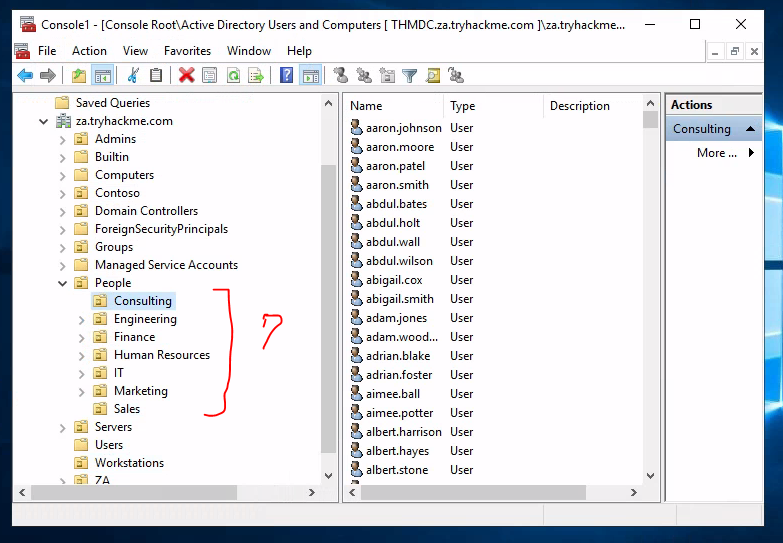
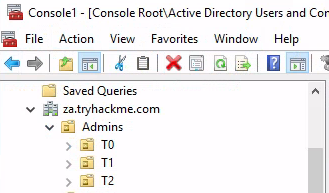
How many Admin tiers does this organisation have? 3
What is the value of the flag stored in the description attribute of the t0_tinus.green account? THM{Enumerating.Via.MMC}
task 4 Enumeration through Command Prompt
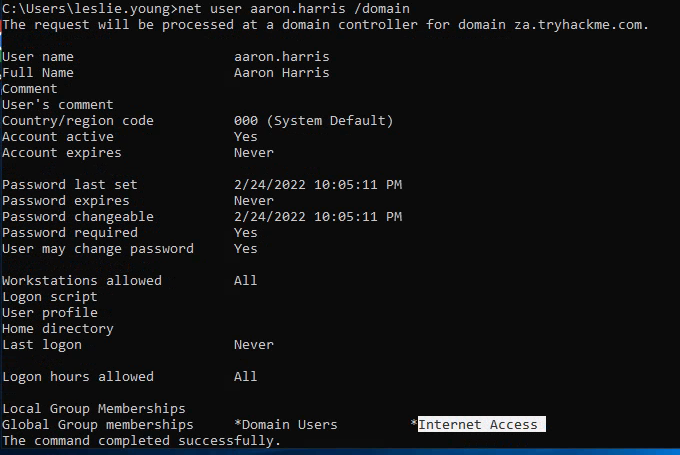
針對以下問題,可以用net user xxx /domain來得知xxx這個user從屬於哪一個group,這是重要的常用指令。
Apart from the Domain Users group, what other group is the aaron.harris account a member of? Internet Access
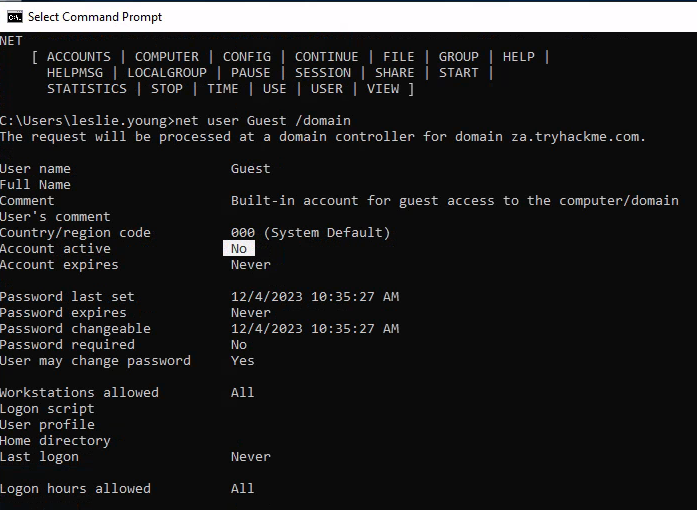
輸入net user Guest /domain來得知下題答案:
Is the Guest account active? No
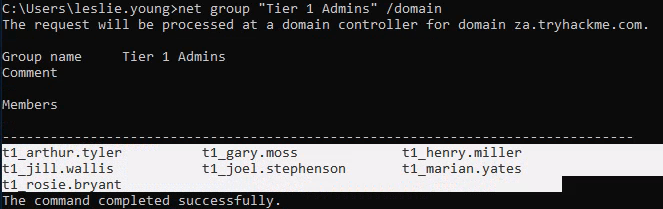
How many accounts are a member of the Tier 1 Admins group? 7
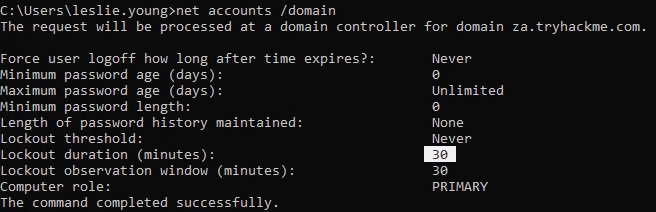
What is the account lockout duration of the current password policy in minutes?
task 5 Enumeration through PowerShell
在cmd
powershell -ep bypass進入powershell
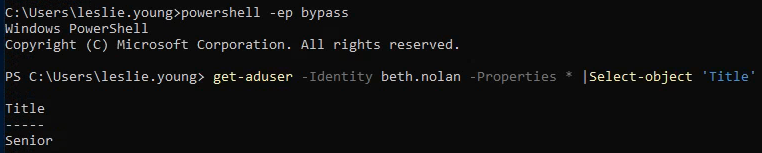
What is the value of the Title attribute of Beth Nolan (beth.nolan)? Senior
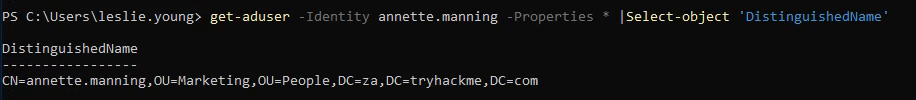
What is the value of the DistinguishedName attribute of Annette Manning (annette.manning)?
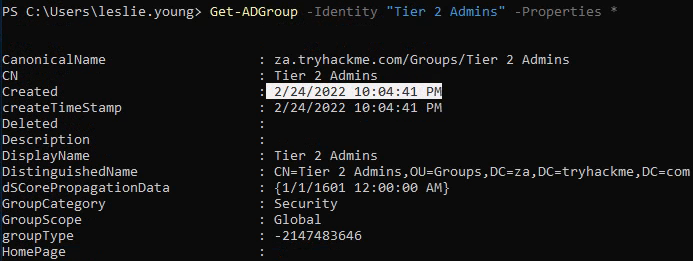
When was the Tier 2 Admins group created?
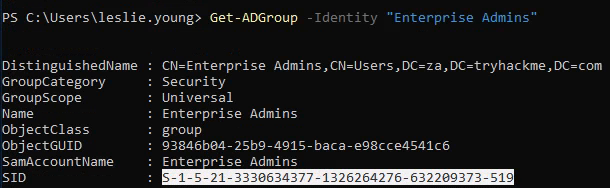
What is the value of the SID attribute of the Enterprise Admins group?
SID很重要(可使用pass the hash跟pass the ticket),這個指令要特別注意。
Which container is used to store deleted AD objects?
Task 6 Enumeration through Bloodhound
先看看目前的IP,等一下下載sharphound要用:
PS C:\Users\jenna.field> ipconfig
Windows IP Configuration
Ethernet adapter Ethernet 4:
Connection-specific DNS Suffix . : eu-west-1.compute.internal
IPv4 Address. . . . . . . . . . . : 10.200.18.248
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 10.200.18.1
注意要從https://github.com/BloodHoundAD/SharpHound/releases來下載SharpHound.exe或ps1,以下是把github上下載的SharpHound給上傳到靶機的指令:
┌──(kali㉿kali)-[~/THM/EnumeratingActiveDirectory]
└─$ scp SharpHound.exe jenna.field@10.200.18.248:SharpHound.exe
The authenticity of host '10.200.18.248 (10.200.18.248)' can't be established.
ED25519 key fingerprint is SHA256:50ZqYlTFUYKTHHPzgPNzG0gSydLnknXL0Ea7lUs7tT8.
This host key is known by the following other names/addresses:
~/.ssh/known_hosts:11: [hashed name]
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.200.18.248' (ED25519) to the list of known hosts.
jenna.field@10.200.18.248's password:
SharpHound.exe 100% 5691 22.6KB/s 00:00
用ls指令確認一下是不是真的有上傳:
PS C:\Users\jenna.field> ls
Directory: C:\Users\jenna.field
Mode LastWriteTime Length Name
---- ------------- ------ ----
d-r--- 9/15/2018 8:19 AM Desktop
d-r--- 12/9/2023 3:14 AM Documents
d-r--- 9/15/2018 8:19 AM Downloads
d-r--- 9/15/2018 8:19 AM Favorites
d-r--- 9/15/2018 8:19 AM Links
d-r--- 9/15/2018 8:19 AM Music
d-r--- 9/15/2018 8:19 AM Pictures
d----- 9/15/2018 8:19 AM Saved Games
d-r--- 9/15/2018 8:19 AM Videos
-a---- 12/9/2023 3:24 AM 5691 SharpHound.exe
輸入下列指令,由SharpHound蒐集內網資訊,並將其資訊檔上傳到BloodHound,解釋一下各個參數:
CollectionMethods:此參數用於確定Sharphound將收集什麼類型的數據,最常見的選項是Default或All;此外,由於Sharphound會緩存經過枚舉得到的信息,所以一旦第一次完成Sharphound的運行,我們就只能使用Session(會話)收集方法才能檢索新的使用者會話,這會加快枚舉資訊的處理速度。
Domain:該參數將指定要枚舉的目標域,有時候,我們可能希望枚舉與現有域具有信任關係的父域或其他域的信息,我們可以透過更改這個參數來告訴Sharphound應該枚舉哪個域。
ExcludeDCs:此參數將指定Sharphound不要直接接觸網域控制器,這將降低Sharphound執行時間引發警報的可能性。
PS C:\Users\tony.holland> .\SharpHound.exe --CollectionMethods All --Domain za.tryhackme.com --ExcludeDCs
2023-12-09T04:18:35.2672020+00:00|INFORMATION|This version of SharpHound is compatible with the 5.0.0 Release of
BloodHound
2023-12-09T04:18:35.5015575+00:00|INFORMATION|Resolved Collection Methods: Group, LocalAdmin, GPOLocalGroup, Ses
sion, LoggedOn, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote, UserRights, CARegistry, DC
Registry, CertServices
2023-12-09T04:18:35.5483935+00:00|INFORMATION|Initializing SharpHound at 4:18 AM on 12/9/2023
2023-12-09T04:18:35.8452475+00:00|INFORMATION|[CommonLib LDAPUtils]Found usable Domain Controller for za.tryhack
me.com : THMDC.za.tryhackme.com
2023-12-09T04:18:35.8921415+00:00|INFORMATION|Flags: Group, LocalAdmin, GPOLocalGroup, Session, LoggedOn, Trusts
, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote, UserRights, CARegistry, DCRegistry, CertServices
2023-12-09T04:18:36.1122225+00:00|INFORMATION|Beginning LDAP search for Sharphound.EnumerationDomain
2023-12-09T04:18:36.1122225+00:00|INFORMATION|Testing ldap connection to za.tryhackme.com
2023-12-09T04:19:06.2537062+00:00|INFORMATION|Status: 1 objects finished (+1 0.03333334)/s -- Using 51 MB RAM
2023-12-09T04:19:21.2068221+00:00|INFORMATION|Producer has finished, closing LDAP channel
2023-12-09T04:19:21.2692716+00:00|INFORMATION|LDAP channel closed, waiting for consumers
2023-12-09T04:19:21.9994556+00:00|INFORMATION|Consumers finished, closing output channel
2023-12-09T04:19:22.0489514+00:00|INFORMATION|Output channel closed, waiting for output task to complete
Closing writers
2023-12-09T04:19:22.1903366+00:00|INFORMATION|Status: 2160 objects finished (+2159 46.95652)/s -- Using 64 MB RA
M
2023-12-09T04:19:22.1903366+00:00|INFORMATION|Enumeration finished in 00:00:46.0985325
2023-12-09T04:19:22.4264353+00:00|INFORMATION|Saving cache with stats: 2119 ID to type mappings.
2122 name to SID mappings.
0 machine sid mappings.
2 sid to domain mappings.
0 global catalog mappings.
2023-12-09T04:19:22.4740447+00:00|INFORMATION|SharpHound Enumeration Completed at 4:19 AM on 12/9/2023! Happy Gr
aphing!
啟動neo4j資料庫: (不能在後面加&來背景執行?)
┌──(kali㉿kali)-[~]
└─$ sudo neo4j console
[sudo] password for kali:
Directories in use:
home: /usr/share/neo4j
config: /usr/share/neo4j/conf
logs: /etc/neo4j/logs
plugins: /usr/share/neo4j/plugins
import: /usr/share/neo4j/import
data: /etc/neo4j/data
certificates: /usr/share/neo4j/certificates
licenses: /usr/share/neo4j/licenses
run: /var/lib/neo4j/run
Starting Neo4j.
2023-12-09 07:12:51.190+0000 INFO Starting...
2023-12-09 07:12:52.911+0000 INFO This instance is ServerId{f043050c} (f043050c-22b1-4a63-a54a-4451cee05e3a)
2023-12-09 07:12:55.184+0000 INFO ======== Neo4j 4.4.26 ========
2023-12-09 07:12:56.978+0000 INFO Performing postInitialization step for component 'security-users' with version 3 and status CURRENT
2023-12-09 07:12:56.978+0000 INFO Updating the initial password in component 'security-users'
2023-12-09 07:12:58.939+0000 INFO Bolt enabled on localhost:7687.
2023-12-09 07:13:00.526+0000 INFO Remote interface available at http://localhost:7474/
2023-12-09 07:13:00.533+0000 INFO id: 4A4D38694A2B635AED3F9E5C0CD304E1C2141CB7C04AF489709380A05A024F57
2023-12-09 07:13:00.533+0000 INFO name: system
2023-12-09 07:13:00.534+0000 INFO creationDate: 2023-11-25T02:46:15.293Z
2023-12-09 07:13:00.534+0000 INFO Started.
接下來在啟動欄找到bloodhound,並啟動圖形介面:
程式執行起來後,就upload data。
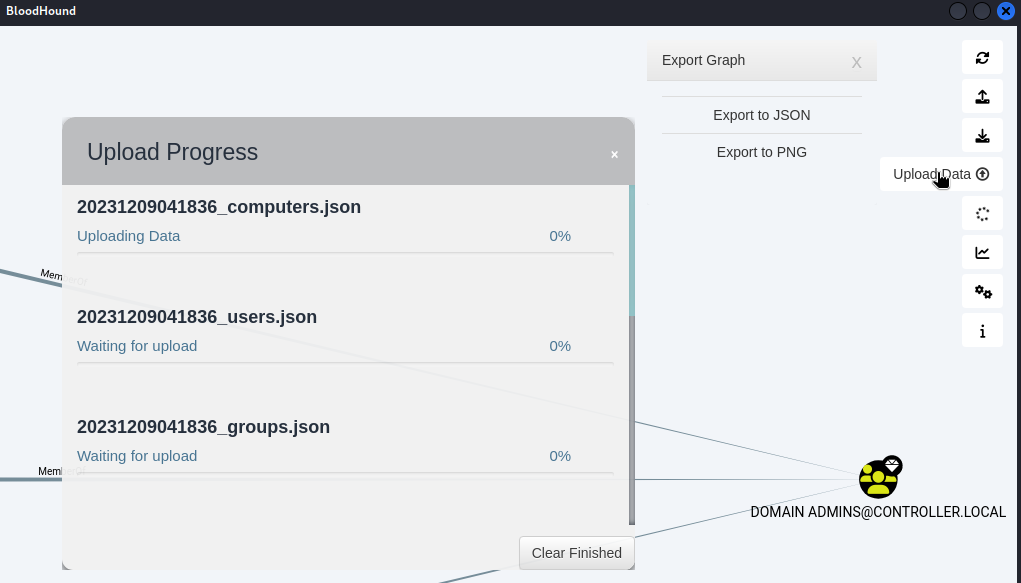
如果之前有上傳過別的內網資料,記得要清空資料庫:
奇怪的是,用我自己蒐集的json檔遲遲載不進去,不過THM官網上已經有掃好的zip檔,載下來即可導入:
導入完成後,按下Analysis裡的東西(如下圖手指)才會顯示出來。
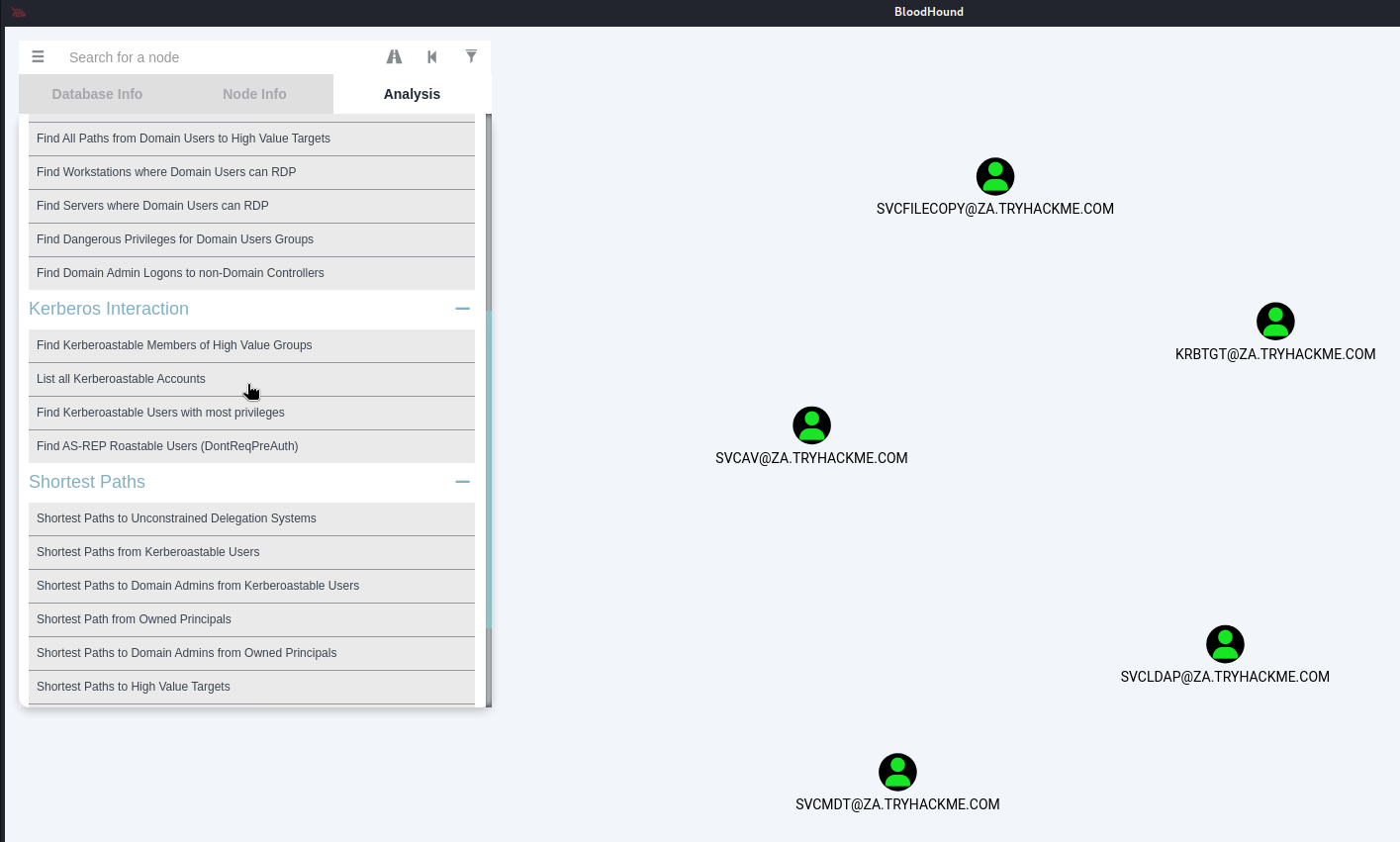
Apart from the krbtgt account, how many other accounts are potentially kerberoastable? 4
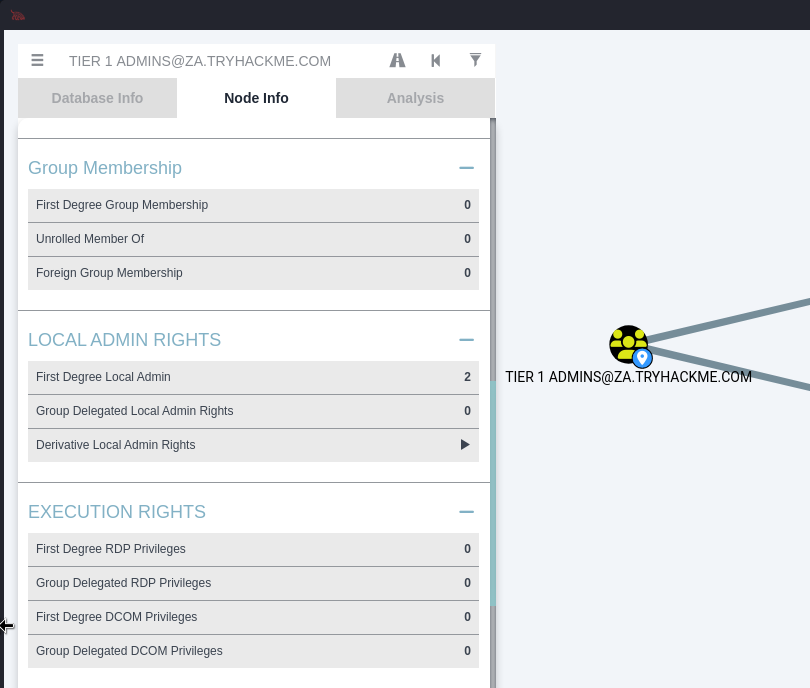
How many machines do members of the Tier 1 Admins group have administrative access to? 2
左上的搜索欄打TIER 1就會自動補完剩下的字,再去看看Node info的local admin rights的第一項,是2。
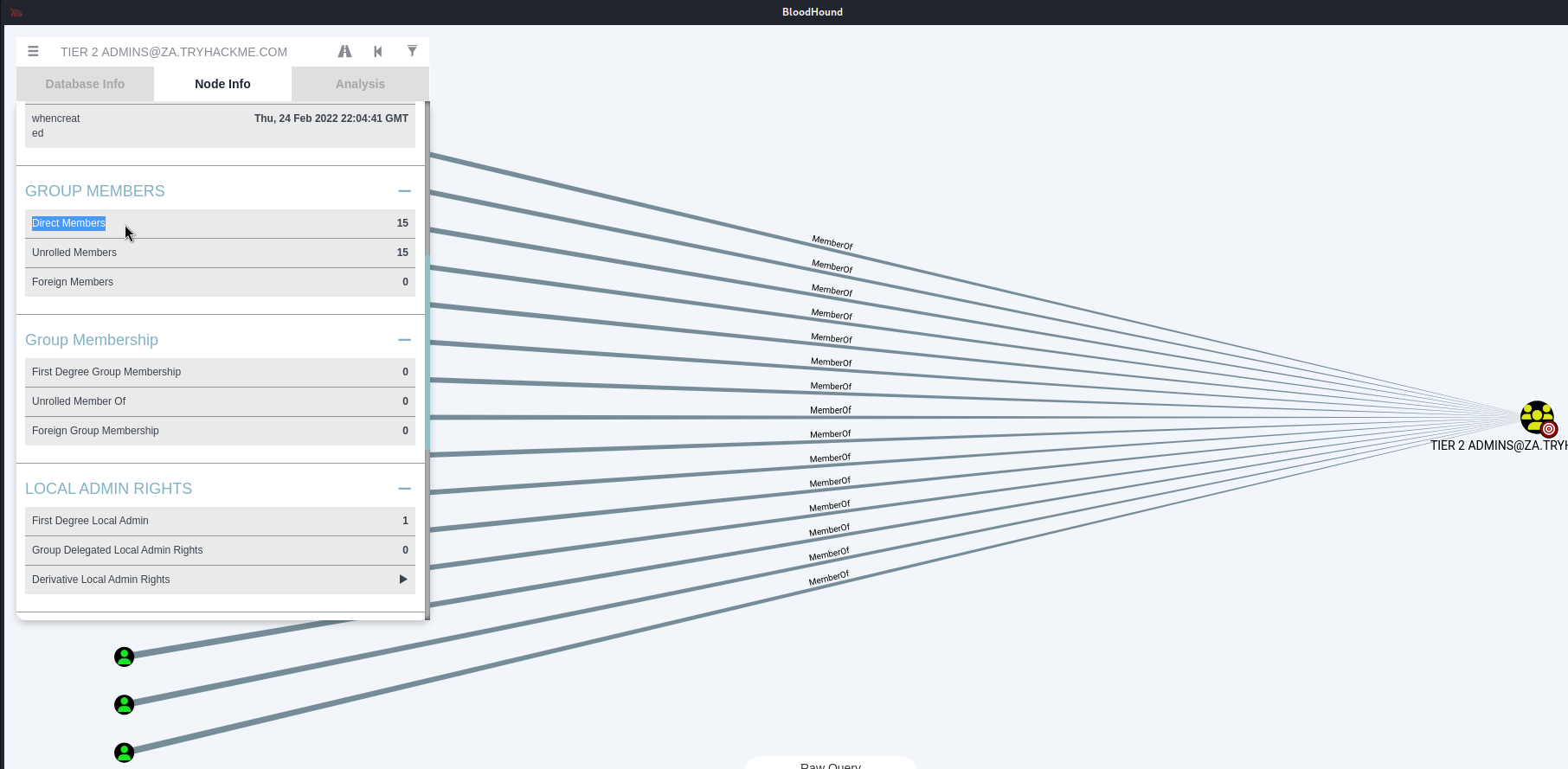
How many users are members of the Tier 2 Admins group?
先在左上搜索框打Tier 2。會自動跳出結果,再點Node info看group members,是15個。